SECURE YOUR BUSINESS WITH EXPERT VAPT STRATEGIES
How Secure Is Your Infrastructure? Book a Free Consultation with Wattlecorp’s Experts to identify vulnerabilities, develop a robust VAPT strategy, and safeguard your business with tailored protection solutions.

🤔Did you know? OWASP board changed W to “Worldwide” from “Web” in February 2023 making it “Open Worldwide Application Security Project”.
In this blog let’s have a sneak peek into the OWASP top 10 2021 and its relevance to ensuring security in your applications.
Table of Contents
Toggle- What is OWASP top 10 ?
- The history behind OWASP Top 10
- OWASP Top 10 ( 2024 Updated )
- A01:2021—Broken Access Control
- A02:2021—Cryptographic Failures
- A03:2021 — Injection
- A04:2021 — Insecure Design
- A05:2021—Security Misconfiguration
- A06:2021-Vulnerable and Outdated Components
- A07:2021 – Identification and Authentication Failures
- Also Read: OWASP Mobile Top 10 Vulnerabilities
- A08:2021 – Software and Data Integrity Failures
- A09:2021 – Security Logging and Monitoring Failures
- A10:2021 – Server-Side Request Forgery (SSRF)
- OWASP security design principle
- Staying ahead of the vulnerabilities
What is OWASP top 10 ?
It is a research-backed standard application security awareness document gathered from 40 voluntary organizations across the globe. The priority order in the listing is based on the occurrence of incidents reported from each bug (the highest reported vulnerability takes the first place).
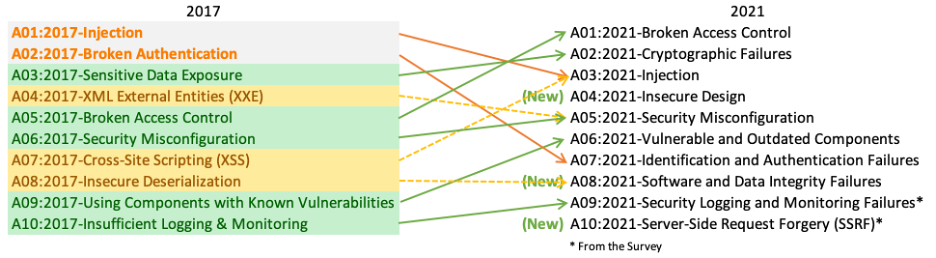
The project is led by The OWASP Foundation, which is a non-profit organization that distributes application security-related free and open resources, forums, documentation, technologies, tools, and methodologies. And is updated once every three to four years, with the latest updations based on
Rather than being a mere vulnerability list, the OWASP top 10 vulnerabilities list helps to assess every flaw with the OWASP Risk Rating methodology. And provides examples, guidelines, and best practices to prevent cyber attacks. With this, developers and security experts can build cyber resilience to keep their applications safe from threat actors.
The history behind OWASP Top 10
According to sources from Wikipedia and Veracode, the initial phase of OWASP was laid on September 9, 2001, by Mark Curphey to make software security visible to everyone.
The introduction of OWASP has been a revolutionary helping hand for developers worldwide to make software security visible and give them the power to make truly informed decisions about common vulnerabilities and their solutions. Jeff Williams had been the chair from late 2003 until September 2011.
OWASP Top 10 ( 2024 Updated )
Using the OWASP Top 10 2021 list as a standard is arguably one of the greatest ways to secure your organization’s software development culture to one that results in more secure code.
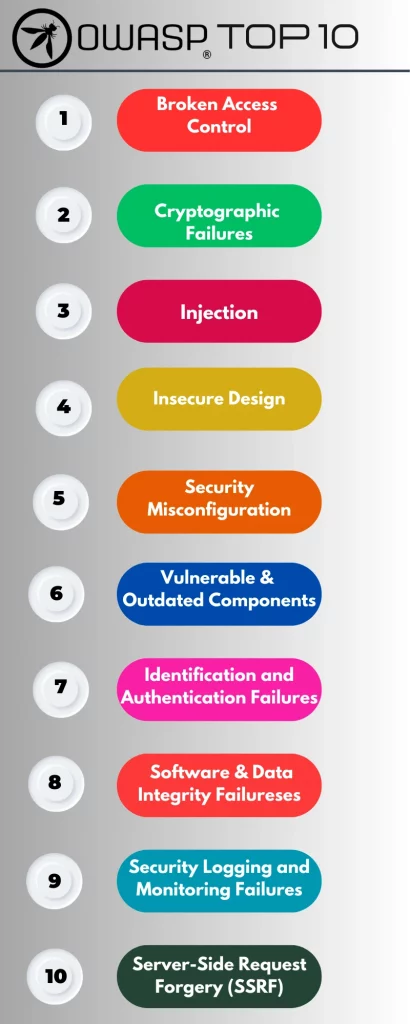
Following are the OWASP top 10 2024 vulnerabilities list:
A01:2021—Broken Access Control
This vulnerability allows bad actors to bypass authentications and gain access to sensitive data and systems. They can exploit this vulnerability simply by modifying the URL or by changing the parameter within the browser.
And it occurs due to the lack of proper access control configuration.
Impacts of Broken Access Control:
- Admin privilege even without being logged in
- Add, modify, or remove the data from the user record
- Reputational loss
How to prevent Broken Access Control:
- Implement deny-by-default for resources that are not to be made public
- Minimize Cross-Origin Resource Sharing (CORS)
- Implement monitoring and alert for admins for suspicious user access
- Implement rate limiting to prevent brute forcing
- Ensure metadata and backup files are not present in web roots
A02:2021—Cryptographic Failures
This vulnerability enables bad actors to bypass encryptions implemented over sensitive data such as passwords, financial records, credit card numbers, health records, personal information, and even business-related classified information.
This vulnerability is exploited in scenarios in which either automatic database encryption is used or a lack of proper encryption of network requests or when simple or unsalted hashes are used for encryption for data storage.
Impacts of Cryptographic Failures
- Sensitive data breach
- Hefty fines from legal authorities due to lack of data privacy compliance
How to prevent Cryptographic Failures
- Encrypt sensitive data in transit and storage with secure protocols and standards
- Delete sensitive data that is stored unnecessarily
- Ensure cryptographic randomness wherever possible and ensure it is not predictable
- Store passwords with strong and adaptive hashing functions
- Avoid outdated cryptographic mechanisms
A03:2021 — Injection
This vulnerability allows attackers to exploit an application or even gain access to its infrastructure when it does not properly sanitize user input.
It can be executed by uploading unintended data or pieces of code along with the web request, which makes the interpreter output sensitive information stored in the database server.
Also, injection is a group of vulnerabilities that contains:
- SQL/NoSQL Injection
- Command Injection
- Server Side Template Injection
- Header Injection
- Cross-Site Scripting (XSS)
- HTML injection
- CSS injection
Impacts of Injection attacks?
- Data leak
- Partial or complete access to the server
- Response manipulation
- Loss of user integrity
How to prevent Injection attacks?
- Source code review
- User input sanitation and filtering
- Output encoding
- Implementing limit over output and connection timeout
A04:2021 — Insecure Design
Secure design is a process for evaluating threats continually and ensuring that code is robustly built and tested to prevent known attack methods.
A lack of inefficient control design leads to this vulnerability and it fails to choose the level of security architecture for the application or the organization.
Impacts of Insecure Design
- Access to sensitive data stored in the vulnerable system or server
- Altering the functionality of the application
How to prevent insecure design
- Implementing security checks from the initial phase of SDLC(Software Development Lifecycle)
- Validate all important flows that are immune to the threat model and create use-cases and misuse-cases for each layer of your application.
- For important authentication, access control, business logic, and key flows, use threat modeling.
- Implement and use secure design patterns and libraries
A05:2021—Security Misconfiguration
Indeed we must configure security measures in our systems and applications. But what if they are not properly configured?
It can be misconfigured or unchanged default (common) credentials, enable unnecessary features such as (ports, services, privileges, pages, etc.), outdated software, etc.
Impacts of Security Misconfiguration
- Complete access over the server or the system and the data stored
- Functionality manipulation of the application, which affects the user
How to prevent Security Misconfiguration
- Make the application minimal with just the necessary features and frameworks used
- Share security practices and directives with the clients
- Implement separate credentials for each phase of development (development, QA, production) environments
A06:2021-Vulnerable and Outdated Components
Software service providers fix vulnerabilities in their products with each software security upgrade. This includes the operating system, web and application servers, database management systems, runtime environments, libraries, and all APIs and related parts.
This vulnerability takes place if we haven’t updated or implemented the latest version of the secure software. It results in making the entire application vulnerable from the vulnerable framework or software we used within.
Also, this vulnerability takes place when you implement software and its related components in your application for unreliable or untrusted sources.
Impacts of Vulnerable and Outdated Components
- Server compromise
- Reputational damage over the firm
How to prevent Vulnerable and Outdated Components
- Update the software and framework patches
- Remove unnecessary dependencies
- Only rely on components and dependencies from secure sources
A07:2021 – Identification and Authentication Failures
This vulnerability is related to security weakness in the login module.
It occurs due to a lack of restrictions for automated attacks, unchanged default passwords, improper session validation or expiry, and a lack of restrictions for weak or well-known passwords.
Impacts of Identification and Authentication Failures
- User account takeover
- Identity theft
How to prevent Identification and Authentication Failures
- Restrict weak or default passwords
- Implement Multi-Factor Authentication
- Log failed password attempts and implement an admin alert system
- Implement delay for numerous failed login attempts
- Enforce password length, complexity, and password standards
Also Read: OWASP Mobile Top 10 Vulnerabilities
A08:2021 – Software and Data Integrity Failures
This vulnerability occurs due to a lack of integrity in either or both of the code and infrastructure of the software being used.
It can be due to using plugins, modules, or libraries from illegitimate sources. Also, a lack of proper integrity checks of software updates would lead to the same.
Impact of Software and Data Integrity Failures
- Database compromise
- Unauthorized updates making it run over all the installations
How to prevent Software and Data Integrity Failures
- Ensure packages, libraries, and dependencies are utilizing trusted repositories
- Verify the authenticity of the software or data with proper digital signatures
- Implement and ensure proper access control, configuration, and segregation in the CI/CD pipeline
- Use a software supply chain security tool, such as OWASP Dependency-Check or OWASP CycloneDX, to ensure that components do not contain known vulnerabilities.
A09:2021 – Security Logging and Monitoring Failures
Monitoring and logging incidents play a vital role in the detection of breaches. This category is to help find and respond to active breaches properly, with the help of logs.
It occurs due to a lack of or unclear logs of failed or suspicious login attempts, high-value transactions, etc.
Impact of Security Logging and Monitoring Failures
- The source and the intensity of a data breach can’t be analyzed due to a lack of incident logs
- Database compromise
How to prevent Security Logging and Monitoring Failures
- Establish proper monitoring and alerting of suspicious activities
- Ensure logs are implemented
- Encode the logs to prevent injection attacks on the logging system
- Implement a standardized incident response and recovery plan
A10:2021 – Server-Side Request Forgery (SSRF)
SSRF vulnerabilities occur when a web application retrieves a remote resource from the server or database without verifying the user-supplied URL.
It allows the bad actor to send a forged request to an unexpected network destination, even if it is secured by a firewall, VPN, or any sort of network access control measures.
Impacts of Server-Side Request Forgery
- Compromising the infrastructure of the application including its internal services
- Sensitive data leakage
- Conduct further attacks such as RCE (Remote Code Execution) and DoS (Denial of Service)
How to prevent Server-Side Request Forgery
- Implement deny-by-default in firewall settings which block all except essential intranet traffic
- Sanitize and validate all the client-supplied input data
- Enforce URL schema, port, and destination with a positive allow-list
- Disable HTTP redirections
- Use network encryption
OWASP security design principle
The aim of software security is simple; maintain and ensure the CIA triad (Confidentiality, Integrity, and Availability) of the information resources from any digital platform to the user.
Confidentiality simply implies nothing but the data should only be accessible to the authorized or to the intended recipients. Integrity sets that in an application, the data should be stored securely in a standardized form. Whereas availability is to ensure that the data is made available to them at ease.
The purpose of OWASP security design principles is to assist developers in “building” the current-best secure web applications aligning to the CIA triad.
The following are the security design principles, which consists of the following:
1. Clarifying the assets
To get started implementing a security design, the first step is to define the assets subjected to vulnerability in your firm or organization and create specific preventive measures to defend each set of assets from possible attacks, based on its risk exposure. Also, we must keep in mind that not all assets hold the same value.
It can be classified into hardware, software, information, infrastructure, and outsourced services based on the data it withholds.
With asset clarification, OWASP helps the developers define security controls for the data level of security withholds based on its criticality.
2. Understanding attackers
Knowing the opponent plays a key role in any attack or defense strategy. The same is applicable, when it comes to defining ways to secure the applications/firm too.
This can be either an insider or an external entity as follows:
- State-sponsored hackers
- Employees with bad intentions for the organization with access to the systems that have access to the sensitive data of the organization.
- Cybercriminals that target your organization
- Amateur hackers
Implementing defense strategies from the development phase itself (shift-left security approach) by considering each classification of bad actors as mentioned above would be helpful to ensure cyber resilience.
3. Implementing proper security architecture
OWASP suggests every application should be designed in such a way that it covers all kinds of possible cyber risks varying from accidental usage risks to sophisticated attacks.
Also, STRIDE or DREAD threat modeling framework (both created by Microsoft) techniques are also suggested for developers to identify and classify the threats based on their rating, while implementing security architecture.
In simple terms, STRIDE is used by security professionals to answer “What could go wrong in this system we’re developing?”
It stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of privilege (Privilege Escalation). Developed by Microsoft in the late 1990s, it is used to find and categorize threats.
It is used alongside a parallelizable model of the target system that depicts all processes, data stores, data flows and trust boundaries in detail.
Whereas DREAD is another threat modeling framework that is used to measure the severity of the identified threats. It’s the abbreviation for Damage, Reproducibility, Exploitability, Affected Users, and Discoverability. And is calculated by taking the average of all the 5 metrics in it.
As depicted in the OWASP development guide, the security principles can be classified into the following:
3.1. Minimizing attack surface area
With each addition of a feature, the application gets more and more vulnerable. This can be reduced by implementing controls and preventive measures within the newly added function.
3.2. Establishing safe defaults
Strong rules for security should be for the user account and privilege-related functions in an application. This includes how new registrations are handled, the frequency of password updates, the complexity and security of passwords, how user data is handled, etc.
3.4. The Principle of Least Privilege (POLP)
The concept is clear: “A user may only access information and resources that are essential.” It also implies that each type of user account should only be granted the rights required to carry out its intended role.
3.5. The Principle of Defense in Depth (DiD)
It implies many levels of validation, extra security auditing tools, and logging tools instead of a single security control for user access. This multi-layered strategy with planned redundancy improves overall system security and handles a wide range of attack vectors.
3.6. Zero trust
The application should always validate the data sent by third-party services and not provide such services high-level access within the app. Many websites and applications use third-party services to gain access to extra functionality or data.
From a security standpoint, this concept suggests that you should never trust these services.
3.7. Fail secure
The application security should be designed in such a way that a failure takes the same execution route as disabling the operation. If security measures are capable of throwing exceptions, they must be extremely clear about what that condition entails.
It specifies that applications must fail securely. Failure should not provide the user further access, nor should it disclose sensitive information to the user, such as database requests or logs.
3.8. Separation of Duties (SoD)
Separation of responsibilities (SoD) is an administrative control organizations employ to prevent fraud, sabotage, theft, information misuse, and other security breaches. And it can be enforced statically or dynamically.
SoD involves breaking down work that may fairly be handled by a single person into several tasks so that no single person has complete control.
3.7. Security Through Obscurity (STO)
STO is based on the idea that a software system is secure as long as its details are hidden and weaknesses are unknown or impossible to identify. As the primary security strategy, STO is centered on concealing sensitive information and ensuring secrecy.
It is a key means of ensuring “pseudo-security” in computing systems.
Staying ahead of the vulnerabilities
OWASP Top 10 2021 is one of the global security standards used by developers and security professionals to ensure maximum security from vulnerabilities at every phase of the application from development to post-production penetration testing.
Fixing the vulnerabilities at the earliest is the key to ensuring the security and integrity of the application or service you provide, which keeps the users and their data safe and secure from cybercriminals. And it is no longer a great concern since the best cybersecurity firms are here to help you with the same.








1 thought on “OWASP TOP 10 Vulnerabilities 2024 (Updated)”
Pingback: OWASP Top 10: Understanding Web Application Vulnerabilities 2023 | Your Articles