A portable open-source tool for managing containerized applications, Kubernetes was the talk of the town when it was first out. But anyone who followed the software closely would be aware of the security vulnerabilities that became the reason why this technology dropped its reach. Security issues would pop up from anywhere from runtime engines to container images and weak networks.
The importance can’t be overstated especially at a time when companies are increasing their dependence on containers. Examples of everyday digital applications used by us that include containers are Google web search, a huge chunk of the Microsoft UI, and Amazon Web Services (used by a lot of websites) among others. Now that you’ve understood its importance in daily life, it is even more required to keep it safe. Here are the 5 best security practices that can be adopted while using Kubernetes.
1. Enabling Role-Based Access Control (RBAC)
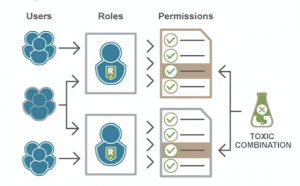
RBAC is a Kubernetes feature that allows you to control whoever has access to the Kubernetes API and the permissions given to them. This is enabled by default to ensure no user has more permissions than required for their responsibilities. The RBAC API provides four top-level roles:
- The role can be used to grant access to resources within a single namespace.
- Cluster-Role adds cluster-scoped resources, non-resource endpoints, and resources from other namespaces to the Role type.
- RoleBinding grants permissions defined in a role to a user or set of users.
- ClusterRoleBinding is the same as RoleBinding but across a cluster.
RBAC plays a huge role when companies have developers branched into strict departments with no common area.
Read More: Top 7 VPN Services
2. Update to the Latest Version
Just like any application and software even Kubernetes needs to be kept updated to the latest version to avoid being exposed to any security vulnerabilities that have been fixed since then.
There are possibilities that the containers in your application contain known or unknown vulnerabilities. To keep your application better equipped, update the source image and redeploy them into the respective containers. This is more recommended than directly updating the containers which might make the images broken.
3. Using Namespaces
Kubernetes uses the concept of namespaces to establish security boundaries. Creating separate namespaces establishes the first level of isolation between different components. There is a limitation when it comes to the usage of multiple namespaces.
Kubernetes doesn’t have a mechanism that provides security across namespaces. Hence it is recommended to use namespaces only when a need to separate two components is present. For things like limiting users to a specific component, the creation of a namespace is unnecessary and poses a security risk that can be avoided. Using RBAC is better suited for such control over users.
4. Enabling Audit Logging
One of the most important things to do while working on Kubernetes is to enable audit logs and frequently monitor them. Unwanted or anonymous API calls are to be noted, especially in times when authorization failures have been encountered. This implies something unwanted could be happening. While not everything might be external, it could also be an internal user trying to access something in a different namespace.
All log entries have the status message “Forbidden”. Kubernetes offers cluster-based logging, allowing all container activity to be logged into a central log hub. Once the central log hub is created, all the standard outputs and error outputs of each container can be ingested using an efficient agent running each node into Google Stackdriving Logging.
Read More: How Google Tracks You
5. Securing Pods and Containers
Pods are objects that house one or more containers. While configuring your pods and containers, ensure that the security context has been configured accordingly for each of them.
Pod Security Policies set defaults on how to run workloads in each cluster. Instructions to define and enable a Pod Security Policy vary depending on the cloud provider and/or deployment model.
A Pod Security Policy allows administrators to control the following:
- Running containers with privileges
- Usage of host namespaces
- Volume type usage
- Host file system usage
- Usage of the read-only root file system
- User and group container IDs and much more.
Contributors: Aswin Prasad, Labeeb Ajmal









1 thought on “5 Best Security Practices For Kubernetes”
Nice post. I was checking continuously this blog
and I am impressed! Very helpful information specifically the last part 🙂 I care for such info much.
I was looking for this particular information for a very long time. Thank you and best of luck.