As businesses are more interconnected globally, the threat of cyber attacks looms over every organization. Cybersecurity frameworks are introduced by many organizations to address this threat. Keeping track of emerging cybersecurity risks and cybersecurity frameworks associated with your industry and region is crucial to meeting your business goals and ensuring you don’t get fined for non-compliance.
Here we will talk about the top 15 cybersecurity frameworks, the challenges in adopting them, and the benefits of cybersecurity frameworks
Table of Contents
ToggleWhy are cybersecurity frameworks essential?
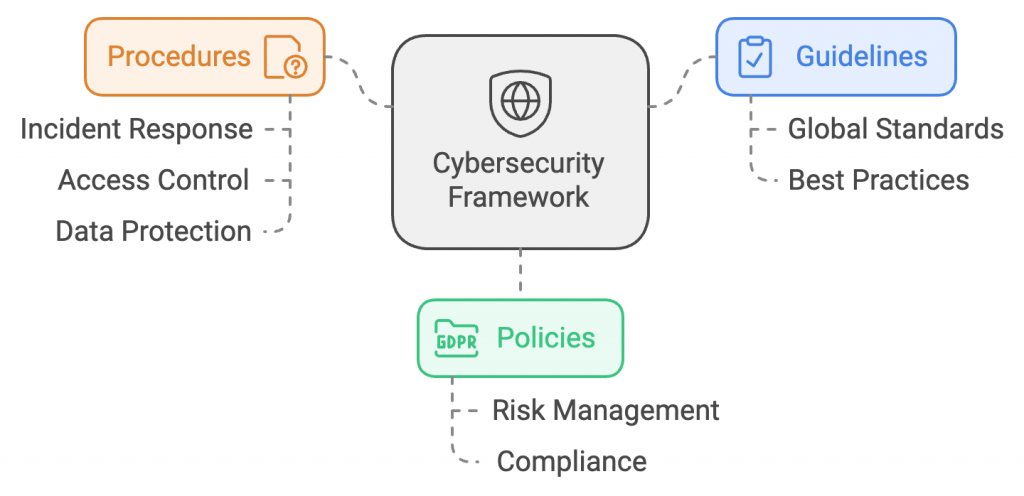
The cybersecurity framework looks more like a blueprint that provides a set of guidelines, policies, and procedures implemented in an organization to strengthen its cybersecurity posture. With standards of security that are common across the globe, cybersecurity frameworks help develop unique security strategies that safeguard your organization against cybersecurity threats.
Cybersecurity frameworks list
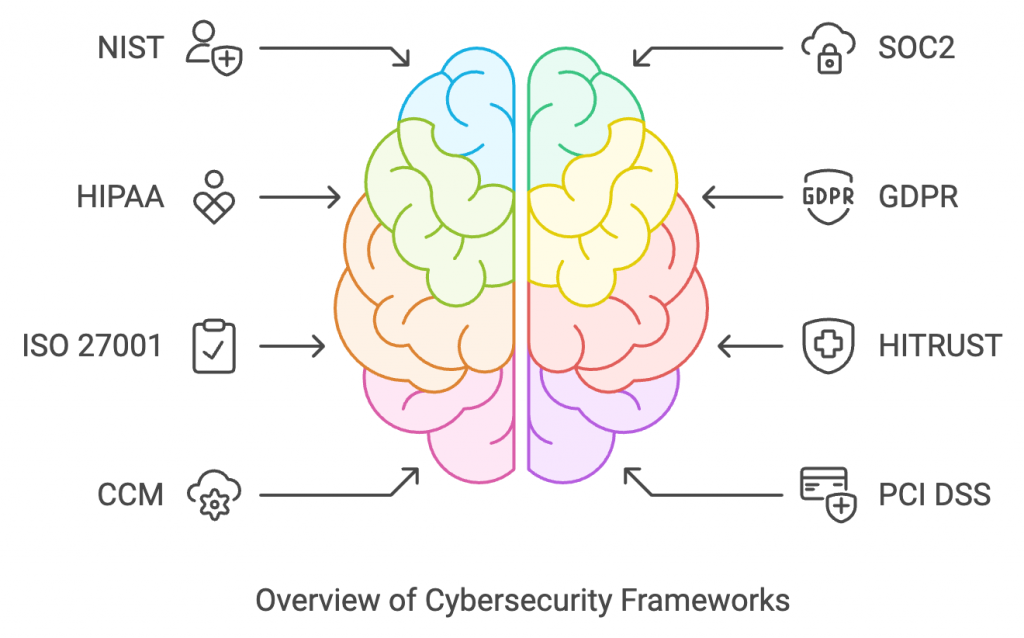
1. NIST cybersecurity frameworks
NIST Cybersecurity Framework provides industry standards, guidelines, and a complete set of best practices for organizations to identify, protect, respond to, and recover from cybersecurity threats. It ultimately helps to strengthen the security poster of an organization by providing insights on asset management, incident response planning, risk assessment, and supply chain management.
The framework was crafted in 2014 to ensure federal agencies meet the security standards within the United States. Implemented in critical sectors like healthcare, energy, finance, and transportation.
2. SOC2
Service Organization Control (SOC) Type 2 was developed by the American Institute of Certified Public Accountants (AICPA) to ensure that vendors and associates are securely managing their client data. It is an auditing standard that consists of more than 60 compliances and auditing processes, used by third-party to access company services.
As it is designed for cloud service providers. As it requires companies to provide documents regarding cyber security, privacy, and confidentiality, it is considered one of the most difficult cybersecurity frameworks to implement; hence, they are mostly implemented in the finance and banking sectors.
3. HIPAA
The Health Insurance Portability and Accountability Act is a cybersecurity framework that ensures healthcare organizations meet the security and privacy compliances of Protected Health Information.
This framework also involves training employees and conducting risk assessments, it is applicable for healthcare providers, health plans, and healthcare clearinghouses
Also Read: HIPAA Compliance Checklist: Enhancing Healthcare Cybersecurity
4. GDPR
The General Data Protection Regulation was established in 2016 and consists of 99 articles related to a company’s compliance responsibilities to ensure data protection of every European Union citizen. This framework is specifically impactful for all organizations working in the EU and the ones that store the private data of EU citizens. Regardless of the size of the company, safeguarding the private data of citizens of the EU GDPR imposes a heavy fine of 4% of the firm’s global annual revenue for non-compliance.
5. ISO 27001
ISO 27001 is a certification created by the International Organization for Standardization which provides a framework for companies to improve their information security management system. It is an internationally recognized information security standard that is implemented across any industry that handles sensitive data by offering sets of best practices to mitigate information security risks.
6. HITRUST – CSF
Health Information Trust Alliance Common Security Framework (HITRUST CSF) is a cybersecurity framework specifically crafted for the healthcare sector, which includes a comprehensive list of compliance requirements, risk assessment, and cyber security governance.
It provides various guidelines that ensure an organization meets the regulatory compliances and risk assessment, which ultimately safeguards sensitive healthcare information.
7. CCM
Cloud Control Matrix is a cybersecurity framework released in 2010 by Cloud Security Alliance that includes best practices and standards specifically designed for cloud-based systems. It provides guidelines on cloud governance, risk management, and compliance.
It consists of 197 control objectives that are structured in 17 domains covering the key sectors of cloud technology.
8. PCI DSS
The Payment Card Industry Data Security Standard framework is adopted to protect customers payment card data. It ensures the security of cardholder data to prevent fraud or unauthorized access to customer information.
PCI DSS consists of 12 requirements that every financial organization, merchant, payment processor, and store has to meet to secure customer data. It includes security for encryption and tokenization technology as well.
9. SAMA compliance
SAMA cyber security framework was Introduced by the Saudi Arabian Monetary Authority in 2017, which includes security guidelines for organizations to protect information assets and online services. All financial organizations, including insurance companies, are responsible for complying with SAMA compliance. SAMA conducts periodic reviews to ensure the framework is updated with emerging cybersecurity threats. It is organized into four main domains: Cyber Security Leadership and Governance, Cyber Security Risk Management and Compliance, Cyber Security Operations and technology, and third-Party Cyber Security.
10. SIA/NESA compliance
National Electronic Security Authority (NESA) was reintroduced in 2014 and has been known as UAE Signals Intelligence Agency (SIA) to ensure the security of UAE’s critical information infrastructure. All the public and private sector companies operating in UAE and the governmental entities are supposed to comply with UAE SIA regulations. It includes specified controls, sub-controls, performance indicators, and automation and implementation guidance for controls.
11. DORA compliance
The Digital Operational Resilience Act is a regulation introduced by the European Council to address cybersecurity risks that concern the financial sector. It consists of technical security standards, Information and Communication Technology (ICT) risk management, incident reporting, third-party risk management, and threat intelligence sharing.
The primary objective of DORA is to unite multiple ICT risk regulations into one framework and mitigate ICT-related security issues across the European financial industry.
12. COBIT
Control Objectives for Information and Related Technologies is a cybersecurity framework introduced by the Information Systems Audit & Control Association to provide guidelines regarding legal and regulatory compliances that a company needs to follow to meet its business objective while reducing the risk of non-compliance and fining.
13. SWIFT CSP
Society for Worldwide Interbank Financial Telecommunications (SWIFT) is an interbank messaging network that introduced a Customer Security Program (CSP) intending to enhance the security posture of the SWIFT payment network. They are mandatory security controls for SWIFT users.
It consists of securing the user’s local environment, preventing and detecting fraud in the user’s commercial relationships, continuously sharing information, and preparing to defend against future cyber threats.
14. ADHICS compliance
Abu Dhabi Healthcare Information and Cyber Security Standards are security guidelines that all healthcare businesses and professionals operating in Abu Dhabi should comply with to improve the security standards of patient data.
The guideline is focused on meeting international privacy standards and ensuring the quality and accuracy of the shared data.
15. ARAMCO CCC
The Cybersecurity Compliance Certificate (CCC) program was introduced to mitigate the cyber security risks for ARAMCO and its vendors. It was developed to ensure all Saudi ARAMCO third parties adhere to the cyber security compliance of Cybersecurity Standard (SACS-002).
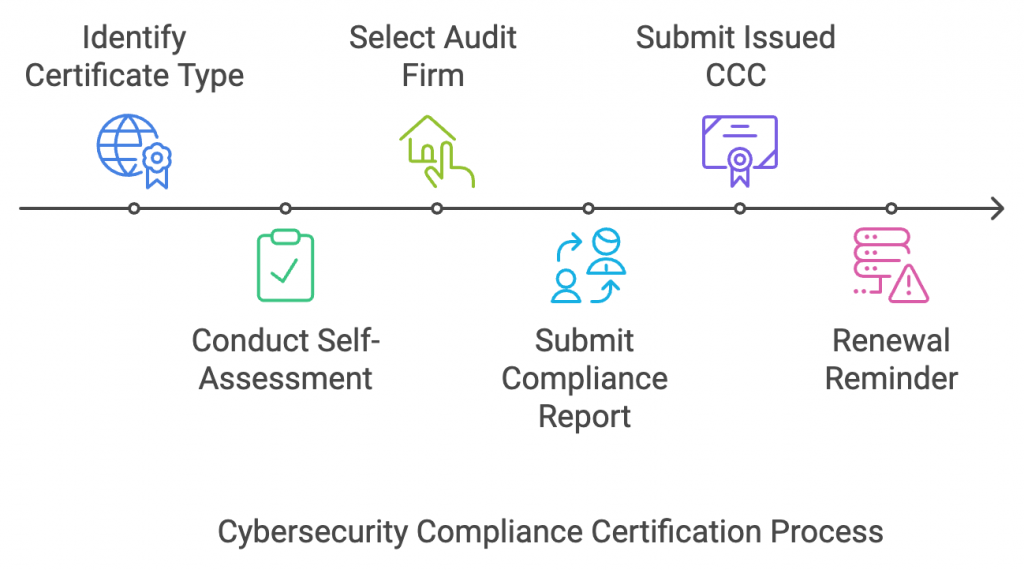
Steps to follow to obtain CCC
- Identify applicable certificate type and assessment requirements
- Conduct self-compliance assessment
- Select an authorized audit firm
- Submit the filled Third-Party Cybersecurity Compliance Report for verification and issuance
- Submit issued CCC
- CCC has a 2-year validity and should be renewed
How to choose the right cybersecurity framework?
Keep these factors in mind while choosing a cybersecurity framework for your organization
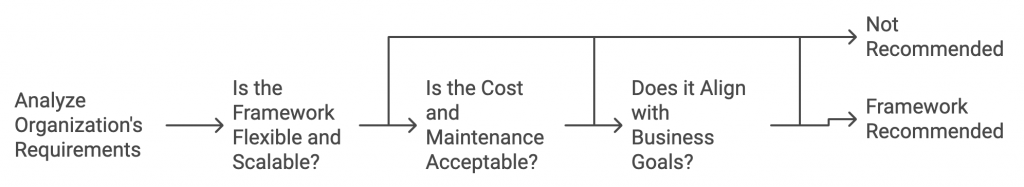
- Analyze your organization’s requirements:
Consider your company size, security goal, risk tolerance, and your client’s specific needs. - A flexible and scalable framework:
Choose a framework that can assist you at every step of your cybersecurity journey. It should be adaptable to industry regulations and the changing technological landscape. - Cost & Maintenance:
Analyze the cost associated with implementing and maintaining the framework to understand how it stands within your budget. - Aligning with your business goal:
Analyze the cybersecurity status of your company, the industry you are operating in, the geographical scope of your business, potential business threats, and your business objective.
The Bottom line
Cybersecurity frameworks play a vital role in deploying an effective cybersecurity strategy and strengthening the security posture of an organization. To name a few, NIST, SOC2, GDPR, HIPAA, and ISO 27001 are some of the prominent frames. The region your business operates, business goals, and budget are to be prioritized when choosing a framework.
Choosing the right cybersecurity framework can be tiresome; not complying with regional regulations will cost you heavily. If you are looking for guidance, choose the expert.
Cybersecurity Frameworks FAQs
1. How can I pick the best cybersecurity framework for my business?
Initially analyze your organization’s requirements, business objectives, and geographical scope. Choose a cybersecurity framework that adheres to industry regulations, evaluate the cost associated with maintaining the framework, and choose a framework that adapts to cybersecurity needs.
2. How can a cybersecurity framework help me follow data protection laws?
By adhering to mandatory cyber regulations and relevant laws like GDPR, SAMA, and HIPAA, the cybersecurity framework meets the legal obligation.
3. What challenges do businesses usually face when using a cybersecurity framework?
Organizations can face issues while implementing any framework. Lack of management support, lack of tools that automate and audit effective control, and lack of budget can all contribute to the challenges a business faces when using a cybersecurity framework.