Client: Regional Law Enforcement Agency
Objective: Develop secure, efficient applications quickly by integrating cybersecurity into every step of development.
Background
A regional law enforcement agency wanted to launch multiple applications to improve operational efficiency across its teams.
To meet tight timelines, they partnered with several third-party development vendors. This approach helped speed up the process, but it also brought significant cybersecurity risks that couldn’t be overlooked—especially given the sensitive nature of law enforcement data.
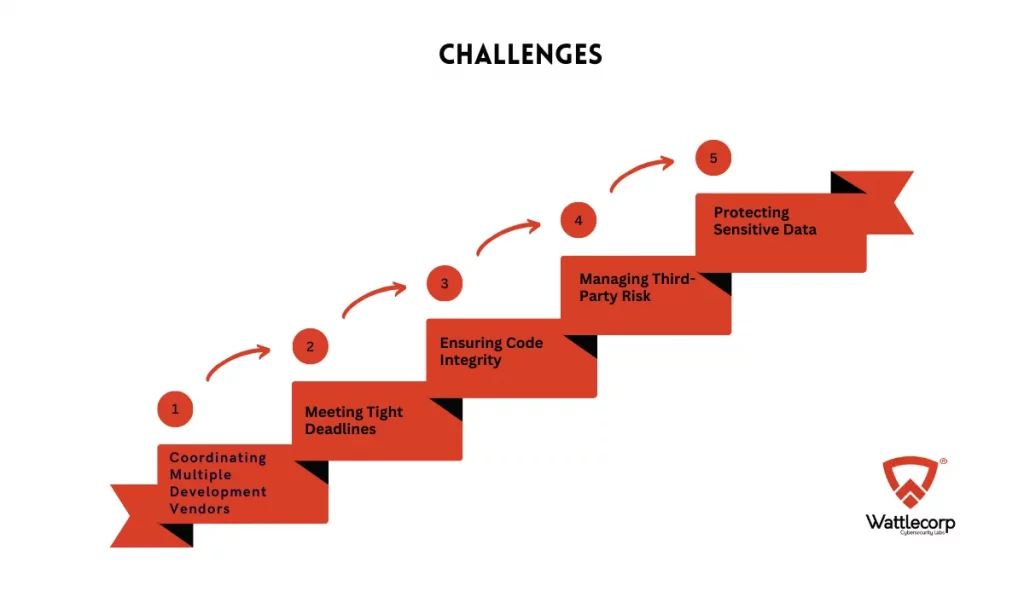
Challenges
1. Coordinating Multiple Development Vendors
Managing different development teams meant coordinating various coding standards and ensuring everyone followed the same security practices.
2. Meeting Tight Deadlines
The agency needed functional applications quickly, creating pressure to develop, test, and deploy without cutting corners on security.
3. Ensuring Code Integrity
Each application had to be resilient against cyber threats, especially with multiple teams contributing to the codebase.
4. Managing Third-Party Risk
The agency needed thorough vetting and continuous monitoring of third-party developers to prevent vulnerabilities from external sources.
5. Protecting Sensitive Data
Handling sensitive law enforcement information required strict data privacy compliance with regional and international regulations.
Approach and Solutions
1. Industry-Standard Cybersecurity Frameworks
- Implemented cybersecurity frameworks (NIST, ISO 27001) to establish baseline security standards for all applications.
- Provided clear security requirements to guide every vendor’s development efforts and ensured uniformity across projects.
2. Secure Coding Across Teams
- Enforced secure coding practices across all development teams and offered detailed guidelines to prevent common vulnerabilities.
- Conducted training on essential security issues (e.g., OWASP Top Ten) to ensure every developer understood potential threats.
3. Integrating Security into the Development Lifecycle (DevSecOps)
- Embedded security checks at every stage, from planning to deployment, to detect issues early and reduce time spent on rework.
- Utilized automated tools for static and dynamic code analysis, streamlining security assessments and enhancing code quality.

4. Third-Party Risk Management
- Conducted comprehensive security assessments of each vendor, from onboarding through project completion.
- Set up continuous monitoring to detect and address any security lapses in real time and drastically reduce third-party risk.
5. Data Privacy and Compliance Consulting
- Engaged data privacy experts to consult on compliance. This helped the agency handle complex regional and international regulations.
- Developed solid data privacy policies and performed Data Protection Impact Assessments (DPIAs) on each application.
6. Regular Security Audits and Penetration Testing
- Scheduled regular audits and penetration tests to proactively identify and remediate vulnerabilities across applications.
- Brought in external security testers to provide an unbiased assessment of each application’s resilience.
7. Cybersecurity Training and Awareness
- Conducted cybersecurity awareness programs for all stakeholders, including third-party teams, to instill a security-first mindset.
- Reinforced best practices in cybersecurity, making sure every team member knew their role in protecting sensitive data.
Results
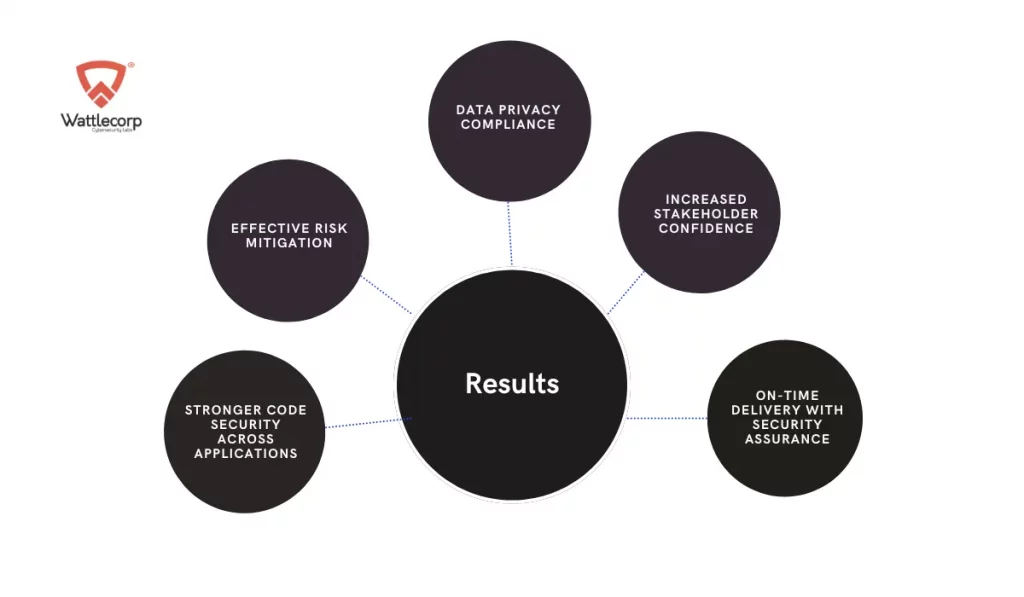
1. Stronger Code Security Across Applications
By embedding security from the start, the agency achieved a solid, secure codebase across all applications, reducing vulnerabilities and safeguarding against potential threats.
2. Effective Risk Mitigation
Proactive monitoring and comprehensive assessments allowed the agency to manage third-party risks effectively, keeping external vendors aligned with the agency’s high-security standards.
3. Data Privacy Compliance
Met all regional and international data privacy regulations, ensuring sensitive law enforcement data was consistently protected.
4. Increased Stakeholder Confidence
Clear, reliable security practices increased trust among stakeholders, including executive leadership, third-party vendors, and the broader law enforcement community.
5. On-Time Delivery with Security Assurance
Delivered each application within the agency’s tight timeline while maintaining uncompromised security, setting a new standard for secure, efficient development

