Data breaches and cyber-attacks are evolving to be highly alarming and expensive to handle. This is where protecting code has become a serious issue.
Code security should be part and parcel of present-day software applications. It has become an integral part of every software development and maintenance strategy, preserving the integrity and accessibility of applications.
In this blog, we’ll break down secure code review process and why they’re crucial for protecting your business.
Table of Contents
ToggleWhat is a Secure Code Review?
As a process that examines application source code systematically, Secure code review emphasizes analyzing and fixing the potential security risks. Being a vital aspect of SDLC (Software Development Lifecycle), it helps improve application quality and security. By reviewing the source code in-depth, developers can identify the security flaws prior, eliminating potential breaches and attacks.
Security code reviews are not confined to detecting code errors, but they involve defining the patterns and practices that can cause these errors. The process includes analyzing the architectural design of the app and understanding the algorithms, data structures, and the entire coding style. With a comprehensive knowledge of these aspects, developers can eliminate such mistakes in the future and create more informed decisions.
The key focus of the secure review is to make sure that the application adheres to the best security standards and coding practices. With its proactive nature in software development, you can save on reputation, cost, and time, eliminating data leaks and security breaches.
Importance of Secure Code Review in Development
- Identification of Errors & Bugs
Code review helps software developers detect and fix bugs. By reviewing and analyzing the code, developers can fix the problems prior. Coders can fix the issue accompanied by software experts. Code reviews enable the sharing of knowledge asynchronously. It thus helps developers and coders fetch assistance without disturbing the work-life balance.

- Constant Standards of Coding
With standards of coding, you can ensure consistency. Additionally, it makes software maintenance easier. Constant standards of coding lay the guidelines the coder needs to adhere to while writing the code. These standards promise readability, maintenance, and uniformity of the codebase. The code’s adherence to these standards is assessed and executed while reviewing the code.
Also Read :The Hidden Cost of Cyber Attacks: What You Don’t See Can Hurt You
- Improvement of Efficiency Using Collaborative Review
Code review requires an additional code inspection in software development with the help of expert developers, which helps improve the development process. Reviewing code enhances efficiency and eliminates unnecessary efforts in coding. This approach saves time and improves the progress of the projects.
- Increased Collaboration & Knowledge Sharing
Code reviews facilitate collaboration and knowledge sharing among peers and team members. While the developer reviews the code of peers, they can gather knowledge about various techniques and other approaches. This ecosystem fosters open discussion, continuous learning, and feedback.
- Identification & Minimisation of Security Risks
Code reviews involve just another layer of protection. It binds many expert developers to inspect the code for security. It ensures defining and solving security issues right in the development phase.
- Continuous Improvement
Code reviews form the major part of constant improvement in the software development stage. Daily feedback with code reviews lets the team identify the mistakes and necessary improvements. This process boosts productivity and code quality.
Secure Code Review Process– Steps Involved
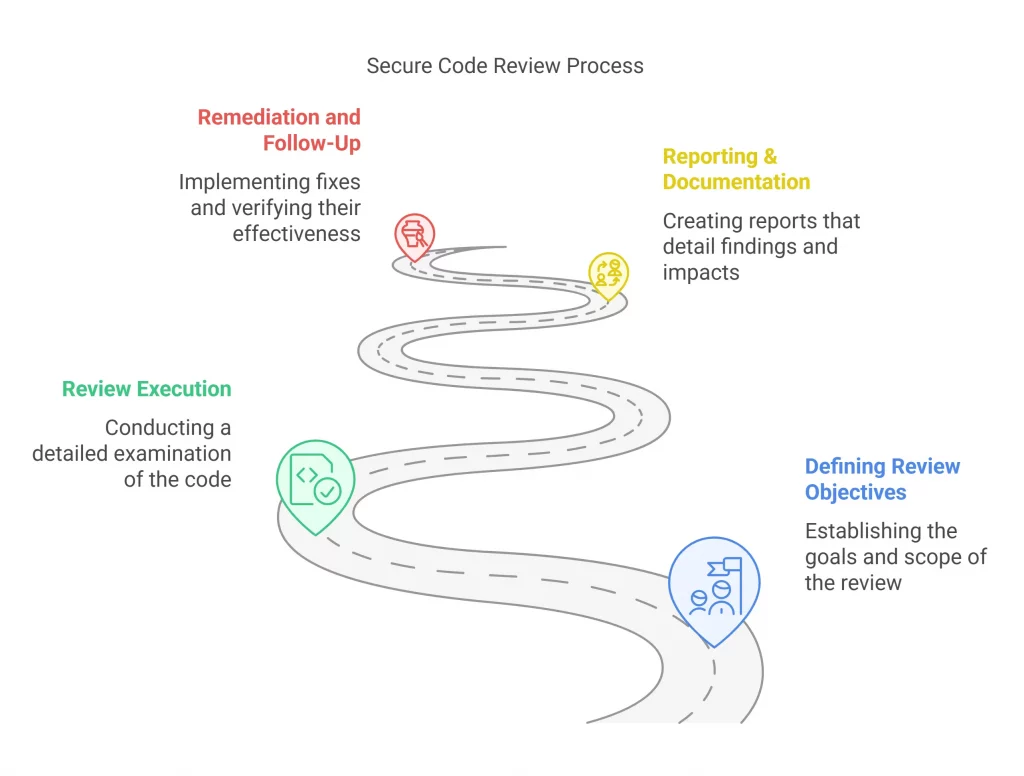
Secure code review process is not a single-step procedure, but a continuous one that moves along various stages. The process can be classified into core four stages :
- Defining Review Objectives
- Manual Code Review
- Automated Review
- Reporting, Documentation, and Remediation
- Defining Review Objectives
The initial phase is to define the objectives of the review. That is, analyzing key areas of concern, vulnerabilities we need to detect, etc. The stage also involves analyzing application architecture and functionality to guide the review process. Defining the scope of the review is also of importance which enables prioritizing the code that needs review.
- Manual Code Review
This is a much-detailed examination performed by security experts. The process involves the identification of logic flaws, insecure coding practices, and vulnerabilities that automated tools could miss. Techniques such as input and output validation checks, analysis of authorization/authentication, review of cryptographic implementations, etc. are leveraged. This stage also analyses the adherence to secure coding standards like CERT or OWASP guidelines.
- Automated Review
This step involves using automated tools to complement manual review. It includes scanning the codebase for major security issues such as cross-site scripting, SQL injections, or buffer overflows. The automated tools offer a wide code coverage and support identifying vulnerabilities efficiently. However, these findings are evaluated with a manual review to eliminate the false positives and maintain high accuracy.
Also Read :Different Types Of Hackers: A Comprehensive Guide (2024)
- Reporting, Documentation and Remediation
Reporting and documentation are the processes you need to follow once the review is executed. This follows bringing in an in-depth report that discusses the identified vulnerabilities, their impact, and the known remediation process. The report should be concise and subject-centered which makes it easy for developer experts to consider and draw conclusions. You can use automated security testing tools to auto-generate reports. The report can be used as a future reference and guide in monitoring the progress of the remediation process.
Secure Code Review Tools Used: A Detailed Look
A comprehensive secure code review, suggests including the optimal use of manual review and automated tools. Let’s learn the ideal ways of using these two tactics for code review.
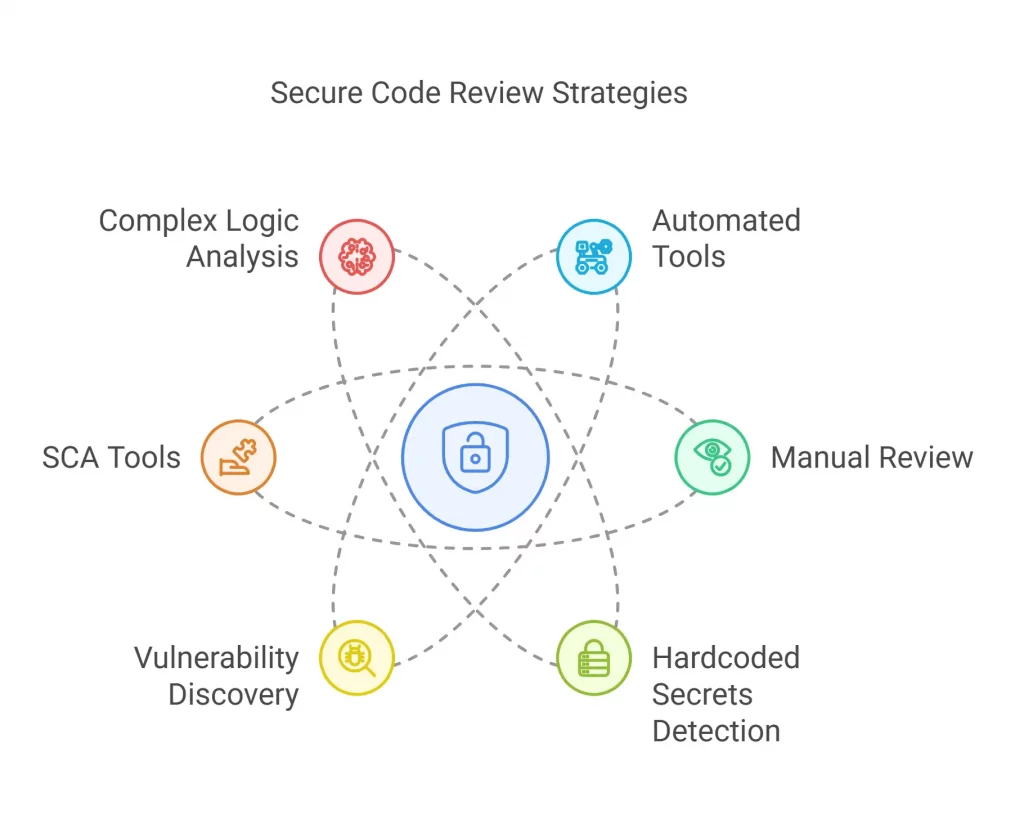
Automated Tools to Perform Secure Code Review:
- Tools that help detect hardcoded secrets: This could involve private certificates, users, passwords, API, and encryption keys.
- Discovery tools to find: XSS (cross-site scripting), buffer overflows, XXE, SQL injections, command injection concerns, and path-traversal issues.
- SCA tools: To detect the third-party and open-source components and identify Publicly Disclosed Vulnerabilities(PCVs) held within the project’s dependencies.
- Identification of missing configurations: Those in K8 Clusters, Docker images, containers, or various configuration files.
Manual Secure Code Review:
- Complex logic and context: For codes that have complex logic or when understanding context is essential, manual review is the ideal approach. Humans can interpret a huge picture and visualize how the code can suit the project objectives.
- Uncommon/Zero-day vulnerabilities: Manual reviewers can usually detect zero-day vulnerabilities that SAST tools can miss out on. They can utilize creativity and expertise to discover less common concerns.
- Follow Data Flow: Understand from code where the vulnerability resides and from the app the source it could be exploited.
- Go for a code review checklist: This makes sure it covers all common security threats and vulnerabilities.
Secure Code Review Checklist
With a code review security checklist, you can keep the different reviews consistent. This is a part of a well-structured and detailed audit process, as it clarifies the security issues to be considered. Let’s get into an ideal template of a checklist:
1 . Functionality Checks
Check if the code executes the required functionality and works based on the specified requirements. Make sure that the edge cases and potential error concerns are appropriately managed.
- Does the code execute the relevant functionality?
- Is every requirement met?
- Are the possible error scenarios and edge cases managed as required?
- Does the code act consistent according to the project specifications?
2 . Evaluation of Readability & Maintainability
Ensure that the code remains well-organized, adheres to the coding conventions, and stays easy to read. This includes consistent naming conventions, indentations, and using comments appropriately to define complex non-obvious code segments.
- Is the code easy to read and organized?
- Are the naming conventions descriptive and defined?
- Is the code formatted and intended?
- Are comments leveraged properly to define complex code segments?
3 . Analysis of Code Structure & Design
Analyze if the code is modular, and follows the standard design patterns and architectural guidelines.
- Does the code adhere to the well-laid design patterns and architectural standards?
- Is the code easy to maintain and modular?
- Do the functions and classes hold reasonable size and complexity?
- Does the code follow principles of separation of concerns and single responsibility?
4 . Measuring Performance and Efficiency
Review the code to find if any possible bottlenecks or issues exist. This could be in the form of memory leaks, unwanted loops, or even suboptimal algorithms.
- Is memory usage optimized?
- Do any potential bottlenecks or inefficiencies exist?
- Are the data structures and algorithms efficient?
5. Error Handling & Logging Mechanisms
Make sure that the code encompasses relevant error handling and logging mechanisms that support troubleshooting and debugging.
- Does the code incorporate relevant error-handling techniques?
- Are exceptions handled as desired and caught at the right level?
- Is logging executed for debugging and troubleshooting?
- Do the error messages convey clear and actionable information?
6. Security Checks
Confirm if the code sticks to the coding principles and whether it poses any security vulnerabilities.
- Does the code follow secure coding practices?
- Do any potential security vulnerabilities exist?
- Is the user input assessed and sanitized appropriately?
- Are authentication and authorization measures executed correctly?
7. Test Coverage
Check that the code includes relevant unit tests/integration tests and that they encompass mandatory functionality and edge cases. Make sure that the tests pass and are up-to-date.
- Does the code contain relevant unit tests or integration tests?
- Is the test coverage adequate for critical functionality and edge cases?
- Do the tests pass and remain up-to-date?
- Is the code readable, greatly structured, and easy to maintain?
8. Code Reuse & Dependencies
Review the code to make appropriate use of frameworks, existing libraries, and components, and make sure that possible dependencies get managed correctly.
- Is the code reusing the frameworks, existing libraries, and components properly?
- Are the dependencies managed accurately?
- Are the unwanted dependencies and duplicate code segments eliminated?
- Are the dependencies actively taken care of and hold sufficient quality?
9. Compliance With Coding Standards
Make sure that the code aligns with the organizational standards and project-bound guidelines.
- Does the code fall in place with the coding standards as demanded by the project?
- Does the code use static analysis tools to execute code standards?
10. Documentation
Check whether the code follows a specific documentation for the sophisticated code segments.
- Do the inline comments adhere to the complex code modules?
- Do functions, methods, and classes include docstrings or descriptive comments?
- Does it include high-level documentation for complex components or modules?
- Is the documentation updated regularly?
Secure Code Review Best Practices
To review the code successfully, reviewers need to analyze the application, and its use cases and be careful about the security controls to be searched for. The best practices include the following:
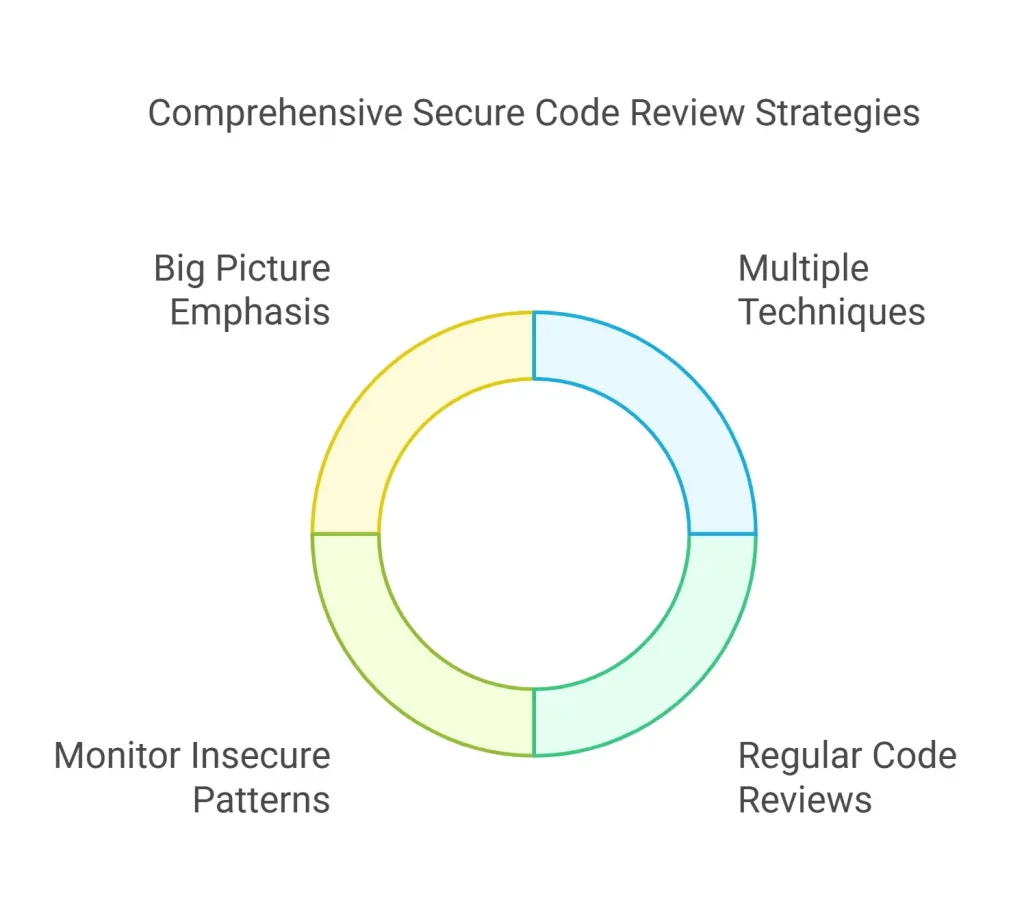
- Use Multiple Techniques
Each review technique can have certain elements that improve final results and some issues too. Hence, it is advised to use a combination of secure code review tools and complementary techniques.
Also Read :The Business Impact of Compliance Failures in SaaS
- Review Code Each Time it Demands a Meaningful Change
Testing code regularly while development is ongoing is often better than waiting till just before the release.
- Continuously monitor insecure code patterns
Tracking repetitive issues is significant for future reviews, and helps to update the review guide.
- Emphasize the Big Picture and Intent of the Review
It is perfect to go for manual reviews for specific areas, while automated secure code review tools are capable of finding specific issues. With OWASP’s secure code reviews guide, you can learn more about secure code review best practices.
Wattlecorp’s Promise of Advanced Code Review
Wattlecorp is destined to offer secure coding review with processes built around specialized manual analysis. This ensures an in-depth and accurate analysis of your application’s security. Rather than depending only on automated tools, our experts take a closer approach on exploring hidden vulnerabilities, possible threats, and logical errors that machines could not detect.
With manual testing and selective automation, we minimize false positives and offer clearer actionable insights. Our team of cybersecurity experts takes care of reviews going beyond the surface-level scans to validate every finding.
By getting committed to security and quality, we offer comprehensive reports that not only highlight concerns but also deliver meaningful solutions. Ready to enhance your application’s security? Let’s connect today!
Secure Code Review FAQs
1. How long does a secure code review typically take to complete?
The timeline can be varied; it can rely on the complexity of the codebase and the size. While smaller projects could be done in days, larger projects can take several weeks. By combining automated tools and a secure manual analysis, we ensure in-depth reviews without worries about unwanted delays.
2. What are common vulnerabilities that secure code reviews can identify?
Secure code reviews are capable of identifying vulnerabilities such as hardcoded credentials, SQL injection, and XSS. They are also equipped with the power to find issues with error handling, security standard adherence, and cryptographic executions. This makes sure that the application is secure and robust.
3. Will a secure code review disrupt my development process or timeline?
No. Secure code reviews are implemented to get along your workflows with the least disruption. At Wattlecorp, we work with your team and identify issues proactively to avoid issues later. Our secure code review methodology is rooted in the implementation of actionable insights to keep the project on schedule with high-end security.