Traditionally organizations lock up their offices to prevent break-ins, but how do you secure your organization’s IT infrastructure? As of today, most company operations are done digitally, hence, guaranteeing cybersecurity has become an essential part of any organization. This is where VAPT comes in, vulnerability assessment and penetration testing aims at identifying potential vulnerabilities before they are misused.
But how do you conduct VAPT? What are the preparations required? To get a clear picture we have created a comprehensive annual VAPT checklist. This checklist will help you prepare for vulnerability assessment and penetration testing, all necessary for data security and secure business operation.
Table of Contents
Toggle- What is a Vulnerability Assessment and Penetration Testing Checklist?
- How to Secure Your Business in UAE with the Annual VAPT Checklist?
- How Do UAE Businesses benefit from VAPT tests and VAPT checklists?
- Effective Vulnerability Assessment and Penetration Testing With Wattlecorp
- Annual VAPT Checklist FAQs
What is a Vulnerability Assessment and Penetration Testing Checklist?
VAPT is a security testing approach that combines vulnerability assessment and penetration testing to better understand the security status and identify the system’s vulnerabilities. Vulnerability assessment involves using automated tools like network security scanners to classify potential threats in a system. On the other hand, penetration testing uses automated tools and manual testing to perform testing on your environment. Thus, VAPT tests reveal weaknesses and underlying security risks that have the potential to cause security breaches.
As VAPT testing should only be carried out by professionals to avoid accidental data corruption, it requires meticulous planning with specialized tools. Especially since the process requires much expertise and as more people get involved there is a chance of missing out on anything critical. This is where the VAPT checklist is introduced, it gives an overview of all the phases involved in the VAPT testing, providing a simple solution to reduce the complexity of the process.
VAPT testing is most effective when done regularly, which is why keeping an annual VAPT checklist is essential. The checklist is more of a guide for organizations, helping them analyze and identify vulnerabilities by planning and reviewing VAPT tests annually. It ensures that all the critical areas of your network are assessed for vulnerabilities.
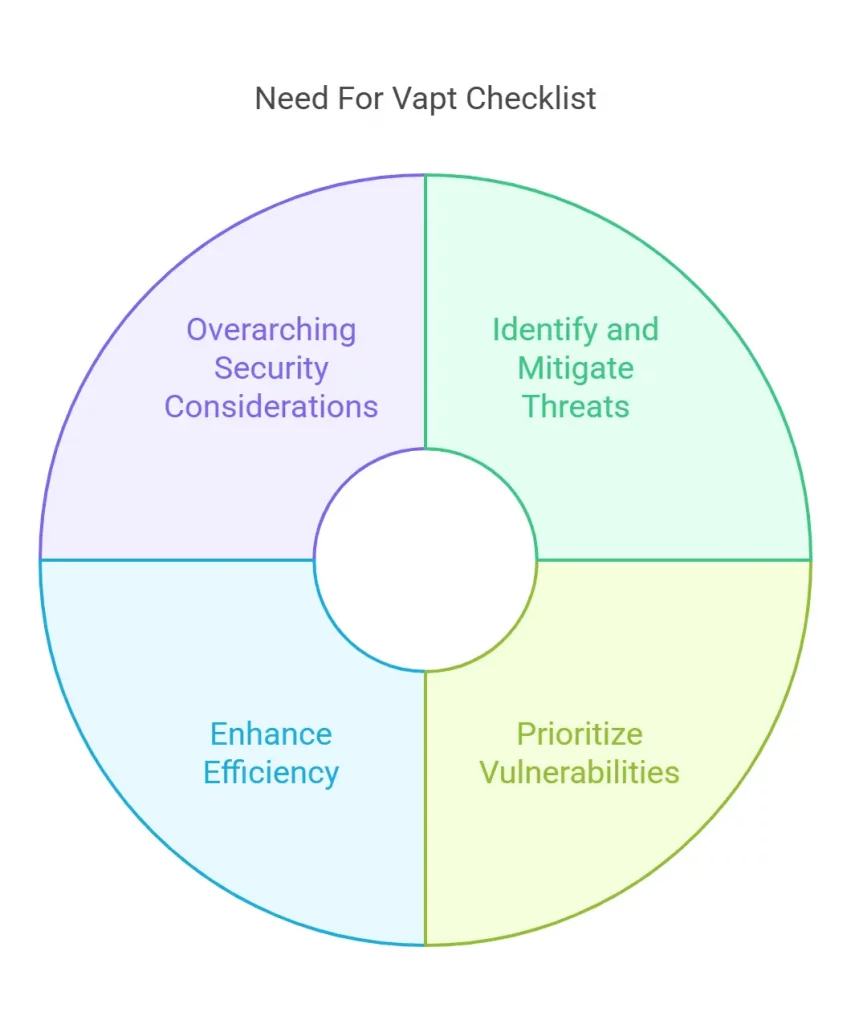
A comprehensive VAPT checklist becomes more crucial as they:
- Include steps to identify and mitigate threats
- Helps the organization’s IT team to prioritize vulnerabilities
- Enhances efficiency by helping manage tasks
- Provide an overarching idea of things to consider while performing assessments and security tests
How to Secure Your Business in UAE with the Annual VAPT Checklist?
The annual VAPT checklist can help businesses secure their network and comply with UAE cybersecurity laws such as NESA, DIFC Data Protection Law 2020, PDPL, and ADGM Data Protection Regulations. It also ensures compliance with global cybersecurity regulations including ISO 27001 and PCI DSS, making your business competent internationally. To understand the VAPT checklist in detail, let’s break down the VAPT checklist into 5 steps.
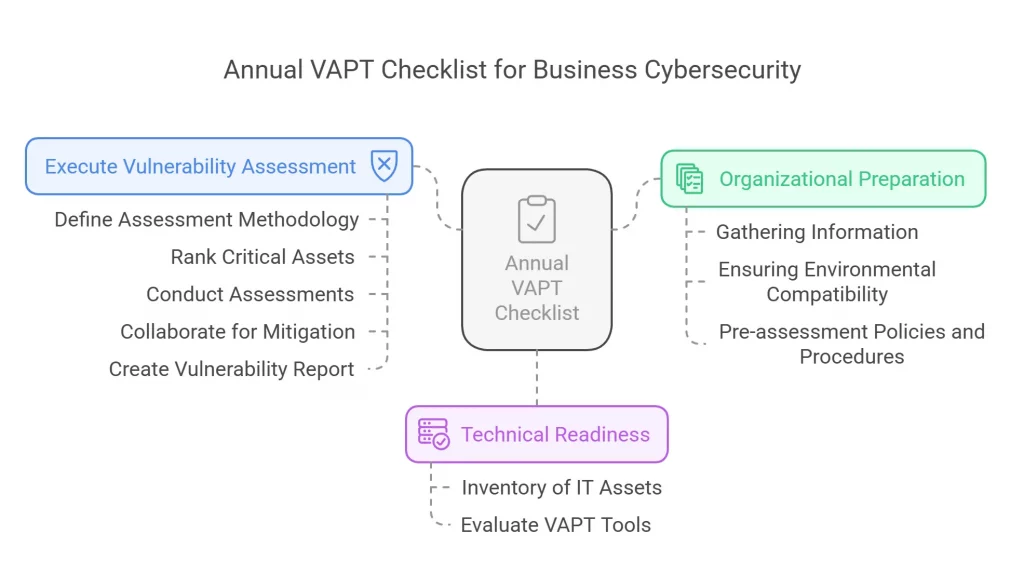
1. Ensuring Organizational Preparation
This is the stage where an organization defines the scope and objective of the VAPT test. The preparation can be divided into two stages.
Gathering information
Start by documenting the assets of the organization that need to be tested, this requires getting information about the targeted network, application, system, web server, and database server. Conduct a proper study to identify the common risks and vulnerabilities that can harm the system and what will be the outcome of VAPT, especially how it will change the business operations.
Ensuring Environmental Compatibility
Before getting on board with the preparation inform the stakeholders and third-party services linked to your organization about the test so that they won’t be caught off guard. Obtain permission from the stakeholders and coordinate with the IT team to oversee the operation to avoid any conflict.
Pre-assessment policies and procedures
Prepare a VAPT timeline with a chart defining the roles and responsibilities of each department and individual. Ensure high-level executive involvement to clear things out.
Provide an employee training program by building a VAPT team and providing an employee handbook specifying the security rules. Establish a code of conduct for effective communication and assess if employees adhere to security protocols.
2. Mandate for Technical Readiness
Prepare an inventory of IT and data assets of your organization which includes mobile, web, and SaaS applications, servers, firewalls, databases, APIs, and public and private cloud environments. Identify if these assets have thorough testing coverage. Evaluate industry-standard VAPT tools with specific requirements and ensure the tools and frameworks are updated based on the latest vulnerabilities.
3.Execute Vulnerability Assessment
After defining the goal of the assessment, determine the methodology for VA to determine the type of testing, automated tools, and how to prioritize the vulnerability class.
- Rank the critical assets based on their vulnerability
- Conduct both automated and manual vulnerability assessments on the critical asset, a further analysis based on real-time scenario is done to identify the weaknesses. The assessment is carried out until the system meets specified security standards.
- Once vulnerabilities are identified gather evidence to verify them and conduct a risk assessment to prioritize the vulnerabilities based on the risk
- Collaborate with developers and specialists to mitigate the vulnerabilities
- Re-evaluate the system after implementing the remediation
- Create a vulnerability report with the findings
4. Conduct Penetration Testing
For effective pen testing, you can choose the service from leading penetration testing companies in UAE like Wattlecorp.
- Start with defining the scope of the test, and internal tests, and gathering legal permission
- Develop a strategic testing plan and the frequency at which penetration testing has to be done
- Determine the type of pen testing, black box, white box, or grey box testing
- Conduct pen testing based on the methodology approved by the expert team, automated, manual, or social engineering tests based on the information gathered in assessing vulnerability
- Conduct pen testing mimicking real-world attackers to exploit the vulnerabilities and understand how well the security system copes
- Document the findings and process
Also Read: Key Cybersecurity Threats Addressed By VAPT In 2025
5. Assessing the Result of VAPT
VAPT only gets completed after analyzing the results of VA and PT and incorporating necessary remediation steps into the cybersecurity strategy. The following are steps to document the findings and ensure your business complies with UAE regulations.
Reporting
- Once the vulnerability assessment and penetration tests are carried out create a detailed vulnerability report
- The report should include the findings and recommendation
- Description of the risk level of each vulnerability
- Documenting the necessary steps for remediation
Remediation Steps
- Prioritize the vulnerabilities to fix them
- Keep the dev/security team in the loop during the VAPT tests to understand the risk level of vulnerabilities, identify and prioritize the vulnerability that can cause major security havoc
- Document the remediation and update the security posture
- Incorporate feed-loop mechanism to understand the effectiveness of remediation action
Also Read: Why Your SaaS Business Needs an Annual Security Program
How Do UAE Businesses benefit from VAPT tests and VAPT checklists?
- Enhancing the security posture by identifying the vulnerabilities and fixing them before it is exploited by a malicious actor.
- As VAPT testing and remediation can enhance the cybersecurity of your organization, this reduces the chance of data breach several folds, thus limiting financial losses
- Can help organizations comply with UAE regulations and government frameworks like UAE Information Assurance Regulation (IAR).
- Apart from regional VAPT tests are necessary to meet industry standard compliance, with VAPT tests and updated certification you can avoid penalties
- Security reassurance is a key factor that drives customers, they are more likely to trust an organization with a reputation for good cyber security.
Effective Vulnerability Assessment and Penetration Testing With Wattlecorp
With the rise of cybercrimes and the government deploying stronger emphasis on regulations and standards on cyber security, VAPT tests have become an indispensable part of business operations in the UAE. The annual VAPT checklist simplifies the complex process of VAPT preparation, vulnerability assessment, penetration testing, and compliance with efficient planning and execution.
But all these efforts may not be effective unless you have top-tier professional support at your back. Wattlecorp provides expert cybersecurity penetration testing services in the UAE.
By thoroughly analyzing the cybersecurity risks and threats in industries like SaaS, Fintech, HealthTech, E-commerce, and Startups, we have developed a penetration testing service in UAE that provides a customizable approach to elevate your organization’s security posture.
Annual VAPT Checklist FAQs
1. What is an Annual VAPT Checklist, and why is it important for businesses in the UAE?
The annual VAPT checklist helps organizations prep-up for vulnerability assessment and pen testing that identify and rectify the security risks and enhance security posture. As strict security measures mandated by the UAE government, which is to be maintained by businesses operating in UAE, VAPT helps to meet the strict regulations.
2. What key components should be included in an Annual VAPT Checklist for UAE businesses?
An annual VAPT checklist should include defining the scope, identifying the assets to be tested, gathering information, testing the network and system, conducting the assessment, reporting the findings, remediation, implementing best practices, ensuring compliance with UAE and other international regulations and provide room for continuous improvement.
3. How does VAPT help UAE businesses achieve compliance with local and international standards?
The primary objective of VAPT is to help businesses identify potential weaknesses in their systems before they are exploited by any malicious actor. This enhances the security posture and meets various other security requirements that are mandatory for international standards like ISO 27001 and PCI DSS. As the UAE government has strict laws regarding data protection and cybersecurity, the annual VAPT ensures compliance with UAE regulations.