The Internet is rife with cyberattacks. With the introduction of various cloud-based applications, such as SaaS (Software-as-a-Service), PaaS (Platform-as-a-Service), and IaaS (Internet-as-a-Service), and many more, including APIs, this has even aggravated the risks of cyber threats over the years. Securing your computers, networks, and applications has inadvertently become more than a necessity to protect them from black hat hackers.
Among multiple security measures that cybersecurity professionals have developed so far as part of their cybersecurity defence strategies, penetration testing has been recognized to be the most latest and happening for it can help identify security vulnerabilities associated with your systems, software, and related applications.
API Penetration Testing is one of the many types of penetration testing modalities that serves to secure APIs from cyberattacks lurking out there, The fact that APIs largely deal with handling sensitive data makes them easily susceptible to cybersecurity risks.
This blog takes you through the essential aspects of API Penetration Testing, which include various methods and best practices.
Table of Contents
ToggleUnderstanding API Penetration Testing
What is API Penetration Testing?
API Penetration Testing is a type of security testing that involves the identification and prevention of vulnerabilities and any related organisational risks. The primary goal of API Pen Testing is to ensure basic security measures are in place. It covers authentication, user access and encryption.
API Pen Testing – Exploring Key Components
Pen testing for APIs identifies vulnerabilities. This process includes:
- Security Misconfiguration: Situations demanding penetration testing API include an incorrectly configured API or not following best security practices.
- Broken Authentication: Involves fixing weak authentication mechanisms to prevent unauthorised access.
- Broken Object-Level Authorization/BOLA: Involves looking for common vulnerabilities, such as weak access control for API resources.
- Rate Limiting: Works by setting limits on the frequency and methods of API calls and preventing DOS (denial of service) attacks.
- Authentication and Authorization: Testing involves ensuring that only authorized users assess APIs to perform specific actions.
Unravelling The Key Methods Of API Penetration Testing
Coding without encryption on an API is like leaving your main door open to a hotspot of cybercrime.
Keep yourself abreast of the proven methods and techniques of Pen Testing APIs.
- Rate Limiting: Helps ensure an active handling of requests to protect against automated malicious attacks.
- Static Analysis: Used to identify potential vulnerabilities by involving specific security analysis tools, such as Burp Suite, Postman, Apache JMeter, etc., to analyze the source code of an application.
- Penetration Testing: Involves the use of manual processes by security experts that help them mimic the strategies employed by cyber thefts.
- Cloud Penetration Testing: Used to assess vulnerabilities in various cloud configurations, including APIs by combining manual testing and automated tools.
Note that learning and understanding the above methods of conducting API Pen Testing should not omit the proper encryption of the application source code.
A Focus On The 5 Most Reliable API Penetration Testing Tools
Adjunct to the methods discussed above, it would be highly appropriate to utilize reliable API Security Tools for a consistent and ongoing protection of your applications, systems, and network.
Fetched from credible sources are the below-mentioned list of some very popular API Penetration Testing Tools:
- Apache JMeter
- What It Is?: An open-source Java application, originally designed to test the performance and scalability of a web application.
- What It Does?: Apache JMeter has also been widely utilized for functional, load, and stress testing APIs, web servers, and databases on various OS, such as Linux, Mac, and Windows. When used as an API testing tool, Apache JMeter considers testing REST APIs to check performance and response time.
For your information, REST APIs, short for Representational State Transfer Application Programming Interface, comprises a set of tools and conventions to build and interact with web services. REST APIs help define how clients, i.e., web browsers or mobile apps, can communicate with a server on the Internet. This typically involves the use of HTTP methods.
Also Read: OWASP API Security Top 10 (Updated )
- Postman
- What It Is?: A widely used platform to build and test APIs.
- What It Does?: Enables team collaboration, helps conduct automated testing, and engage in request chaining by organizing, grouping, reusing, and sharing API requests and examples.
- Burp Suite
- What It Is?: An API security testing tool that is primarily used to test any endpoint of REST API.
- What It Does?: The Burp Suite API Pen Testing tool tests a REST API endpoint by making sure that you employ a normal client to generate normal traffic. The process being to proxy a client’s traffic through Burp helps detect attacks which can be possibly made on a typical web application by testing REST APIs.
- Apigee API Management
- What It Is?: Apigee API Management is a part of the Google Cloud and helps with designing, building, testing, deploying, and monitoring APIs.
- What It Does?: This API security testing tool enables application developers to track traffic, rate errors, and track response times.
(By having users expose their APIs on Apigees through API proxies helps detect possible threats or attacks and prevent the same by a process called decoupling created by the API proxies. As such, the app-facing APIs are decoupled from back-end services, thus facilitating a non-interrupted call from the apps even if any code changes have happened on the back end.)
- Assertible
- What It Is?: A simple yet powerful API testing and monitoring tool.
- What It Does?: Assertible as an API security testing tool helps facilitate JSON Schema Validation and JSONPath data integrity checks via conducting turnkey assertions for domain-specific testing. Note that Assertible is one of those tools in API testing that remarkably keeps tests up to date without causing any time lapse by automatically syncing changes in API specifications to API tests. These include responses, parameters, and headers.
Shielding API with Top Best Practices in Penetration Testing
The significance of pen testing in API is such that it has become impossible to extract coding from security testing for the various APIs out there. As a developer, you also need to adhere to the following to ensure your API stays protected at all times:
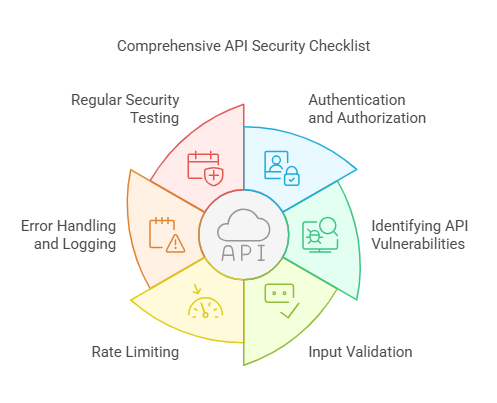
- Implementing Authentication and Authorization
- Identifying API Vulnerabilities
- Input Validation
- Rate Limiting
- Error Handling and Logging
- Conducting Regular Security Testing
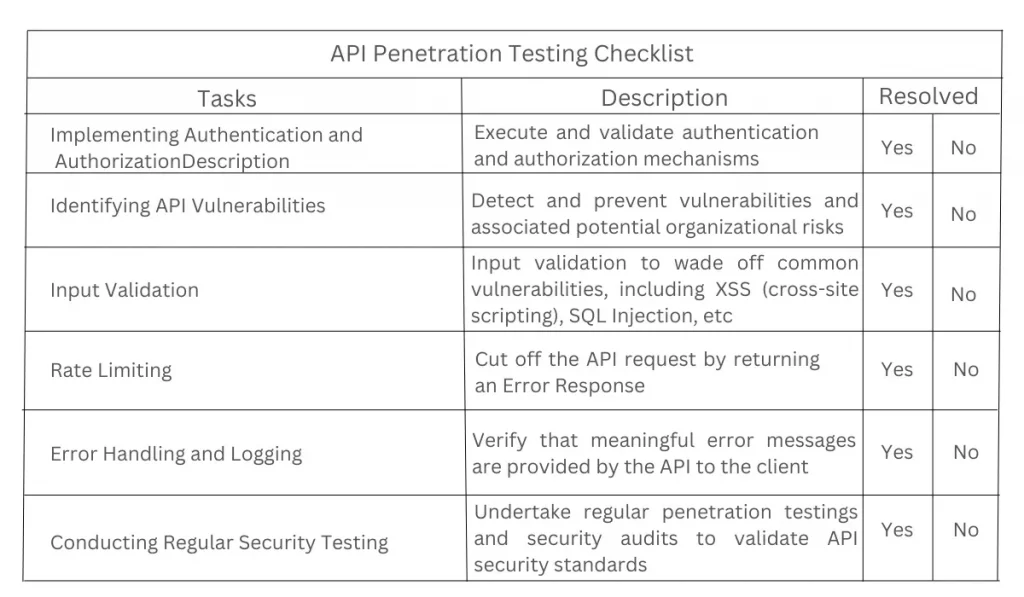
What if you could develop and execute an API Penetration Testing Checklist that considers all the above parameters at one stretch? Sounds easy, isn’t it? Using a checklist for API security testing helps uncover actionable insight.
Also Read: API Security Testing: A Comprehensive Guide [2024]
Executing an API Penetration Testing checklist is one of the best approaches, for the benefits associated with it, which include:
- Deriving consistency across different APIs, projects, and teams.
- Attaining efficiency and streamline security testing processes
- A comprehensive coverage on vital areas, such as rate limiting, input validation, and authentication.
- Risk Mitigation to address known vulnerabilities, including SQL injection and cross-site scripting.
- Report and Documentation to attain accountability and transparency.
API Penetration Testing plays a pivotal role in securing your API from any known or unknown attackers to prevent data breaches, ensure compliance, protect sensitive data, and build trust among users, especially business entities who rely on various software applications.
For the sensitive data APIs handle, Penetration Testing API mandates identifying vulnerabilities on a regular basis to strengthen security.
Wattlecorp, a pioneer in the realm of cybersecurity services, has been highly reputed for its offering impeccable API Penetration Services to its clients across the globe. In addressing the security concerns associated with APIs, Wattlecorp has effectively acknowledged the fact that APIs are the ‘connective tissue that exists between everything on an application.’
The expertise that this cybersecurity service provider has demonstrated in having its API Pen Testing team dig into the security coverage of the API of its clients and penetrating them to report existing flaws there is highly laudable.
Is your API security vulnerabilities worrying you out of your wits? Book a free security consultation with us and have your API secured through our Wattlecorp’s expert cybersecurity professionals.
API penetration testing FAQs
1.How does API penetration testing differ from traditional application testing?
API penetration testing focuses more on an APIs server-side functions. A traditional application on the other hand, is more concerned with securing the user interface.
2.Is API penetration testing required for compliance?
Yes, it is. The fact that API Penetration test is conducted to look for vulnerabilities in its security aspects is the first line of action to determine security compliance. For this reason, this process significantly calls for making a proactive security measure by identifying and addressing vulnerabilities.
3.How often should API penetration testing be performed?
As an API developer or a penetration tester or both, you need to conduct API penetration test as regularly as possible to ensure you keep updated on the security aspects of your application to effectively and proactively keep cyber attacks out of line.







