DORA compliance (Digital Operational Resilience Act) protects financial entities from the disruption brought on by cyber threats, contributing well to the EU financial sector. As a new step taken by the European Union (EU) in addressing the cybersecurity legislation throughout Europe, DORA speaks a lot beyond normal regulation.
Earlier, individual states had distinct strategies, leaving the approach more fragmented. This fragmented state emphasized the need for DORA, the regulation that effectively addresses the existing difficulties financial institutions deal with. It helps them improve security posture through prevention, containment, and response to cyber-attacks.
DORA compliance is a pathway towards operational resilience and lays a foundation for the European economic ecosystem. Let’s learn why achieving DORA compliance is the key and how businesses accommodate DORA compliance requirements.
Table of Contents
Toggle- A Detailed Outlook of DORA Compliance
- Explaining the Purpose of DORA
- DORA: What’s Its Scope?
- How Does DORA Ensure Cyber Resilience?
- DORA: Compliance Requirements
- Potential Risks of Non-Compliance
- Best Practices for Data Security in Transit for DORA Compliance
- Implementing DORA Cybersecurity Compliance with Wattlecorp
- DORA Compliance FAQs
A Detailed Outlook of DORA Compliance
Here’s a question that might be running through your mind: “What’s DORA compliance?” It is simply a regulatory framework built upon EU standards. This compliance is executed to ease cybersecurity and operational resilience, specifically catering to financial institutions. It ensures that the firms can adapt to and recover from crucial ICT-specific disruptions and eliminate systemic vulnerabilities.
Being a specialized standard for financial entities, DORA regulations establish a dominance over the general NIS2 directive in case it faces an overlap between both. For example, when NIS2 and DORA include provisions for third-party risk management and incident reporting, DORA’s specific requirements would take over NIS2.
Explaining the Purpose of DORA
DORA regulations resolve the complexity and interconnectedness that financial systems encounter, where cyber threats or ICT concerns can create huge disruptions. Its key objectives are:
- Improving the operational resilience of financial firms.
- Securing customers’ trust and financial stability.
- Optimizing ICT risk management standards throughout the EU.
DORA: What’s Its Scope?
DORA focuses on all entities of the financial ecosystem such as:
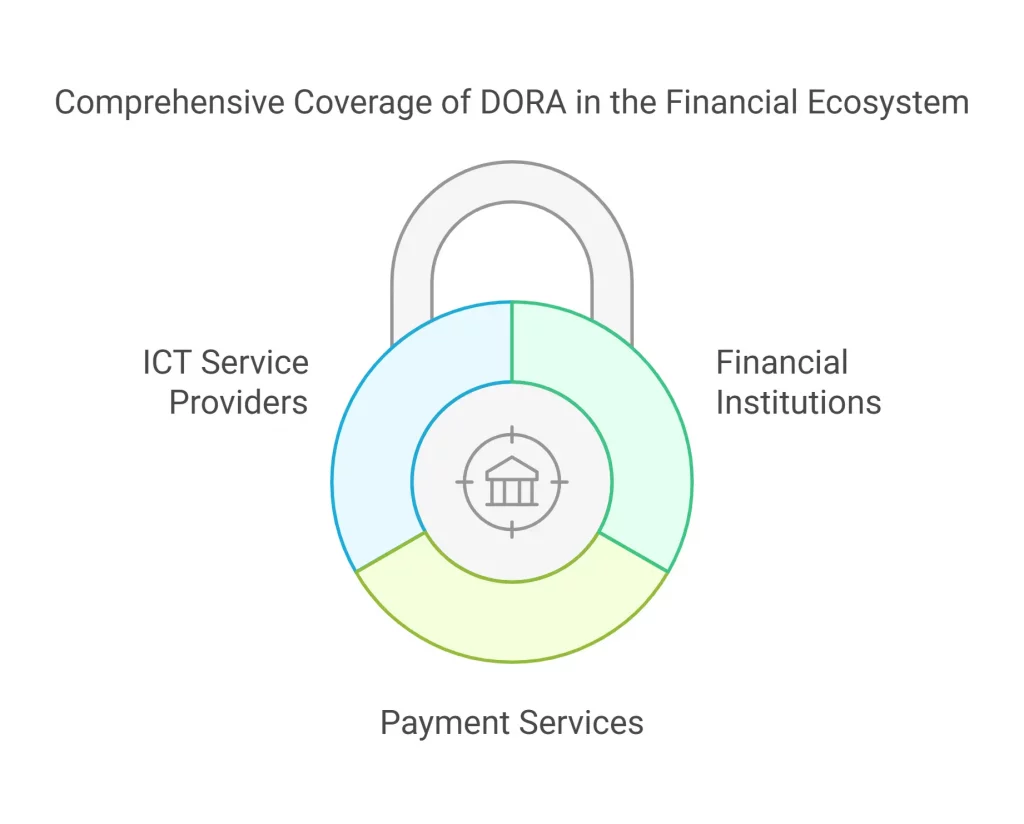
- Insurance companies, banks, and investment companies
- Electronic money services and payment service providers
- Major third-party providers for ICT services like data analytics companies, cloud service providers, software developers, etc.
How Does DORA Ensure Cyber Resilience?
DORA adopts a wholehearted approach towards cybersecurity. It not only considers financial entities but also takes subcontractors and service providers into account. In addition to conventional risk management, DORA establishes accountability. It ensures that all processes falling under DORA’s control are secure. It is inevitable in the present financial environment. Organizations largely depend on outsourced services, hence this approach demands a change in perspective. Firms should hold onto the risk management associated with the third parties.
Also Read : Navigating the Intersection of CRM and Cybersecurity: How to Protect Your Salesforce Environment
DORA: Compliance Requirements
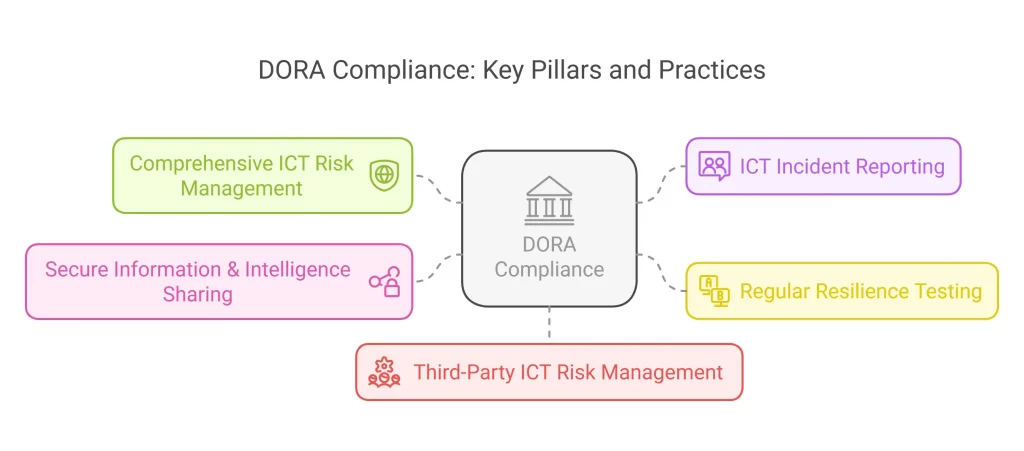
The standard emphasizes specific requirements from financial organizations to achieve compliance. Let’s discuss the key five pillars around which these requirements are structured and act like a DORA compliance checklist.
- Comprehensive ICT Risk Management
Financial firms should adopt a whole ICT management framework to detect, evaluate, and eliminate risks efficiently. This ranges across the risk assessments with careful evaluation of ICT systems to analyze vulnerabilities. This also encompasses the policies and regulations including government frameworks to track and manage ICT risks.
Also Read : How Much Does ISO 27001 Certification Really Cost? A Guide for Business
For instance, banks can use automated tools to conduct real-time risk monitoring. This enables prompt detection and collaborative resolution of threats.
- ICT Incident Reporting
Financial institutions should take care of specific timelines to report the incidents. Submission of the initial report should be within 24 hours of knowing the incident or within 4 hours of its classification. Subsequently, an interim report should be offered within 72 hours of submitting the initial report. This makes sure that it helps with quick communication and transparency in addressing the issues.
For instance, financial institutions can utilize automated incident reporting mechanisms to maintain timely communication with regulators.
- Regular Resilience Testing
Regular ICT systems testing is essential to discover the weaknesses and maintain resilience against possible disruption. Financial institutions should perform penetration testing to implement a simulation of cyber threats and scenario-specific testing to be ready for the worst-case operational challenges.
For instance, insurance companies can simulate ransomware attacks to test the incident response plans and highlight the areas to improve.
- Secure Information & Intelligence Sharing
Collaboration is the best way to combat cyber threats. DORA facilitates secure threat intelligence sharing among financial firms to enhance situational awareness and collective defense.
For instance, investment firms can get into intelligence-sharing networks to get real-time updates on the rising threats and vulnerabilities.
- Third-Party ICT Risk Management
Companies need to manage risks associated with third-party ICT providers to maintain operational integrity. This means DORA emphasizes due diligence and resilience evaluation of ICT providers well before onboarding.
For instance, banks can need cloud service providers to perform frequent independent audits to check compliance using resilience standards.
Potential Risks of Non-Compliance
Lack of compliance with DORA has caused serious risk for financial institutions, both operationally and financially. Here are the ways by which the non-compliance affects them:
- Penalties and financial risks:
Non-compliance with DORA can end up in fines of about 1% of the daily global turnover of the provider and every day, a fine for a tenure of six months.
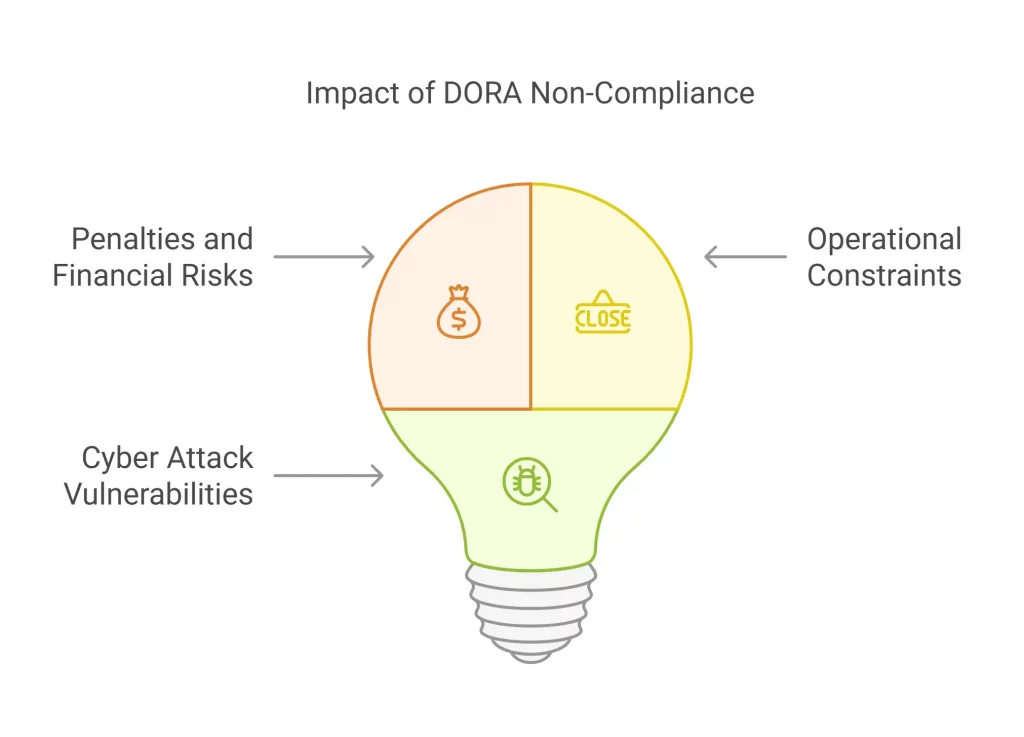
- Operational constraints:
Firms that lack compliance can miss out on the authorization to operate, which can in turn impact the business and degrade the reputation.
- Growing vulnerability to cyber attacks:
Non-compliance can cause institutions to get exposed to cyber threats, creating financial losses and reputational losses. The expenses of non-compliance can outweigh the investment required to achieve compliance.
Also Read : AWS Penetration Testing: Checklists, Tools, Strategies, and Best Practices
Process of Achieving DORA Compliance
Achieving DORA compliance needs a structured process to manage each pillar with caution. Let’s take a look at the step-by-step process towards achieving DORA compliance.
- Lay down an ICT Risk Management Framework
Create and implement policies to find, evaluate, and eliminate ICT risks regularly. Also, leverage automated tools to carry out real-time risk management and monitoring.
- Adopt Incident Reporting Mechanisms
Lay down detailed protocols to report incidents to regulators in the stipulated period. Digital tools can let you automate reporting mechanisms and stay accurate.
- Perform Regular Resilience Testing
Keep appropriate schedules for the annual penetration testing. You should also adopt context-specific exercises to measure resilience. Also, you can incorporate third-party providers for testing exercises to ensure comprehensive preparedness.
- Manage Third-Party Risks
Implement strict due diligence while you onboard the ICT solutions providers. Nevertheless, Incorporate resilience standards in contracts and track performance consistently.
- Implement Incident Response & Recovery Plan
Create detailed playbooks to respond to the cyber attacks and potential operational complexities. Hold training sessions for staff to make them familiar with response protocols.
Best Practices for Data Security in Transit for DORA Compliance
Financial entities must follow the best practices and ensure data security in transit to maintain compliance with DORA. Here’s an overview of them.
- Implement strong data encryption
Adopt data encryption in transit with powerful encryption solutions. This ensures that even while the data gets intercepted, it remains unread or restricts manipulation by the unauthorized user. Individual data is separately secured using quantum-based processes, with keys being changed every hour.
Also Read : Future-Proofing SaaS Security: The Role of an Annual Security Program
- Execute E2EE (End-to-End Encryption)
End-to-end encryption ensures that data gets encrypted at the source with the capability of decrypting only at the destination. This eradicates unauthorized interception while transmission takes place and ensures data confidentiality.
- Perform Timely Security Audits & Testing
The DORA framework demands continuous testing to measure operational resilience and cybersecurity processes. You can learn about the source of data transmission and adopt compliance through the appropriate implementation of penetration testing and conducting vulnerability assessments.
- Monitor & Log All Data Transfers
Across the network, you can log and audit the information transfers with monitoring tools. You can use this method to identify all the possible suspicious activities and the attempts for unauthorized logins. It is a key aspect that lets you report incidents aligned with the DORA compliance standard requirements.
Implementing DORA Cybersecurity Compliance with Wattlecorp
With a structured and comprehensive approach towards cyber resilience, DORA cybersecurity compliance offers consistency in the way organizations manage operational risks.
Though DORA is a complex regulation, financial institutions shouldn’t consider it cumbersome. Rather than seeking ways to circumvent these demands, it is ideal to perceive it as a valuable tool helping you enhance the security posture of your business.
By complying with DORA, financial institutions can bolster their defense strategies and stand against cyber threats, keep up the customer’s trust, and verify regulatory alignment. At Wattlecorp, we offer the best DORA compliance consulting services to guide you through the DORA requirements, compliance solutions, and everything you require to keep your institution resilient and secure against cyber threats.
Our experts also offer a comprehensive suite of services, including automated incident response, threat intelligence platforms, and cybersecurity solutions to let your institutions attain DORA compliance. To learn more, let’s connect today!
DORA Compliance FAQs
Who is affected by DORA Compliance?
DORA applies to you if you are a bank, a fintech firm, insurer, or ICT solutions company that works with financial companies in the EU.
When does DORA Compliance take effect?
DORA takes effect on January 17, 2025. This creates enough room for financial entities to be well prepared to bolster their digital resilience by the time it gets introduced.
What are the consequences of non-compliance with DORA?
Not complying with DORA cybersecurity compliance can cause reputational damage, huge fines, and severe operational losses that can impact your business’s bottom line.