Guess many of you reading this may not be knowing what CVE (Common Vulnerabilities and Exposures) program is and what it implies. In the vast ocean of cybersecurity, CVE is that vital drop that serves as the foundation for standardised vulnerability disclosure and management. Now that you’ve understood what CVE as a concept emphasises, you also need to know what CVE program extension means for cybersecurity. The recent expiry scare related to the decommissioning of the MITRE CVE contract had remarkably shaken the global cybersecurity community.
What felt like a clear disruption to the CVE program was offering critical infrastructure security, incident response, and vulnerability management. The worst nightmare, however, was the time it took to extend the CVE funding that put cybersecurity on edge for 48 hours! Now you may feel why this fund extension is a big deal for enhancing and ensuring global cyber defense. The first thing is it is! Secondly, it underpins the critical need to protect organisations and enterprises, and above all, revamping the cybersecurity strategy.
Here, we will cover everything you need to know regarding the CVE program. You will also learn how preserving/maintaining its functions and operations can help strengthen the prospects for the cybersecurity community.
Table of Contents
ToggleUnderstanding The CVE Program
- Definition and purpose
The CVE program (short for Common Vulnerabilities and Exposure) can be aptly described as the cornerstone of cybersecurity! Its objective being to help identify, define, and catalog publicly disclosed security vulnerabilities helps the cybersecurity community prioritise and address these issues effectively.
- Tracing CVE Program’s History and Evolution
The CVE Program officially took off in 1999. Its purpose, as stated above, is to establish a standardised system to identify and catalog publicly known cybersecurity vulnerabilities. Being that its primary function, the CVE Program has subsequently evolved to cover a wider range of security flaws. These comprise the cloud and service environments – further extending its reach to automation and data-driven approaches.
So how does CVE work? By providing specific CVE IDs for each vulnerability exposed, the entire cybersecurity community helps resolve the issue. To elaborate, CVE IDs connect the threats, security tools, vendor coordination, and incident response. The CVE Foundation, now a non-profit organisation, is crucial to helping enterprises worldwide understand and manage their security vulnerabilities. Prompting them to undertake proactive measures to improve and enhance their cybersecurity is its ultimate objective.
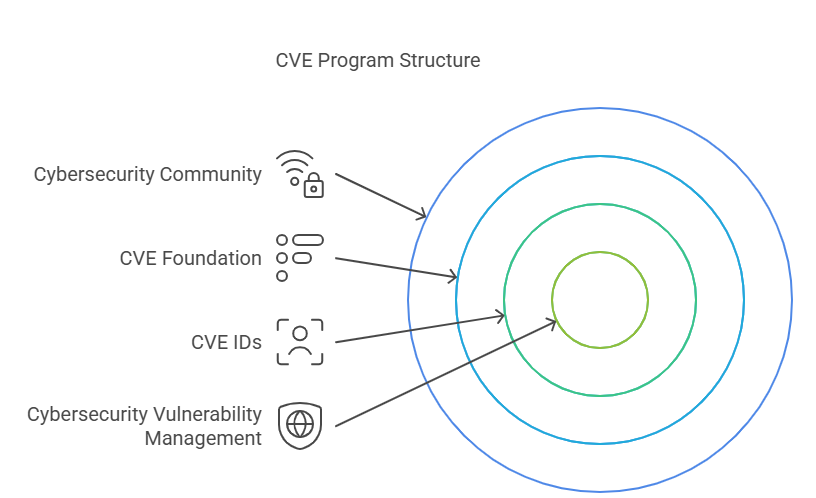
- CVE Program MITRE – An Overview
It is MITRE, a non-profit defense research organisation that primarily operates the CVE program. By offering Cyber Hygiene Services to industries, including Healthcare, the latter has also become an integral part of the CISA’s mission. Again, the credit for this goes to MITRE for providing ransomware support to various healthcare organisations and health systems.
- CVE’s Role In Global Vulnerability Management And Threat Intel
There is no doubt in pointing out that CVE plays a crucial role in global vulnerability management and threat intelligence. This is again because of its ability to provide a standardised method to identify, describe, and catalog vulnerabilities in the hardware and software. You can rightfully expect effective communication and collaboration among the global cybersecurity fraternity. With vendors and researchers also contributing their valuable inputs, businesses can only look out for well-coordinated CVE vulnerability disclosure and remediation efforts.

The Expiry Crisis: What Happened?
In what felt like a shocking event to the global cybersecurity fraternity, the CVE Board on April 15, 2025, was notified by MITRE that the US government will stop its contract to manage the CVE program. This proved alarming enough to suggest a widespread disruption of the CVE operation in terms of rendering total security to businesses across the globe.
Also Read: Cybersecurity for Small Businesses: Essential Strategies for Limited Resources
The Decommission Threat To The CVE
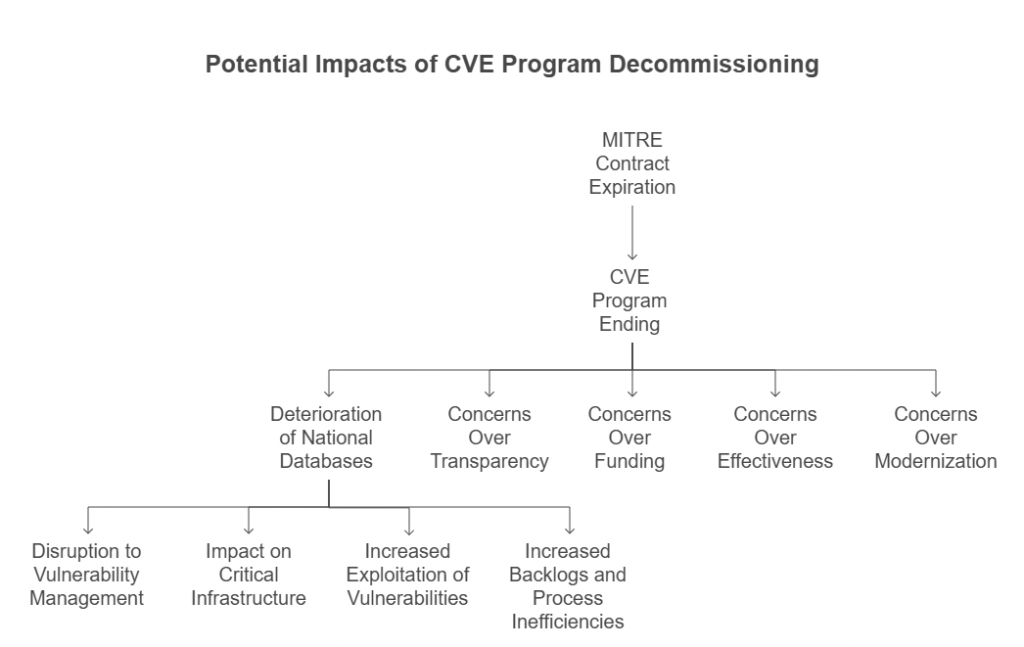
The shocking decommissioning flash news that the CVE faced was due to the concerns regarding MITRE’s contract expiration to operate this program. CVE being a critical component to track and address security flaws, discontinuing/expiring MITRE contract only meant CVE Program ending.
A major impact with the lapse of the CVE program within 24 hours of the announcement also implied national vulnerability databases and advisories deterioration.
- Concerns Over Transparency, Funding, Effectiveness, or Modernization
The CVE funding crisis can significantly halt the process of identifying and cataloging vulnerabilities. Understanding that this program’s functionality is critical to the global cybersecurity community, such a decommissioning can potentially impact CVE transparency and effectiveness.
We at Wattlecorp – one of the global cybersecurity partners, can well sense the dangers of disrupting CVE operations. The news of MITRE CVE Program expiration is enough to hamper our efforts to protect our clients’ critical systems and enterprises.
We also know that the strength of cybersecurity lies in the superior handling and undertaking of the CVE program.
- Industrial Reactions And Community Concerns Of CVE Contract Expiry
Here are the likely consequences that industrial, community, and national concerns over CVE Program defunding/decommission can bring forth:
- Disruption to vulnerability management: CVE program disruption can adversely impact an organisation’s ability to identify, assess, and mitigate security weaknesses.
- Impact on critical infrastructure: A potential shutdown of the CVE program is likely to cast a significant threat to national security.
- Increased exploitation of vulnerabilities: CVE program lapse can cause significant delays in vulnerability disclosures and remediation.
- Increased backlogs and process inefficiencies: Potential funding lapse can make it more difficult to manage and address issues related to vulnerabilities backlog.
The 11-Month Extension: A Second Chance
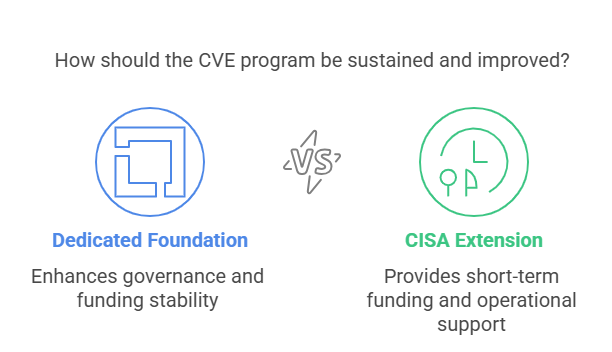
Being on the edge of potential defunding for 48 hours, the CVE program eventually received an 11-month extension from CISA (Cybersecurity and Infrastructure Security Agency) With this much time in hand, this seems a good opportunity for us to reboot CVE.
Thankfully, the future funding and operations of CVE have been made open to discussions. The road to sustaining the CVE program also sounds prognostic. Equally, considerations to convert it to a dedicated foundation and improve CVE program governance are going in accordance with the plan.
Reinventing Cyber Defense: What Needs Fixing?
It’s likely for the CVE program to have faced a good bit of challenge upon news of its potential funding lapse. Some of these include:
1. Delays in assigning vulnerabilities
2. Issues with automation (specifically, real-time integration)
3. Data standardisation and reporting gaps
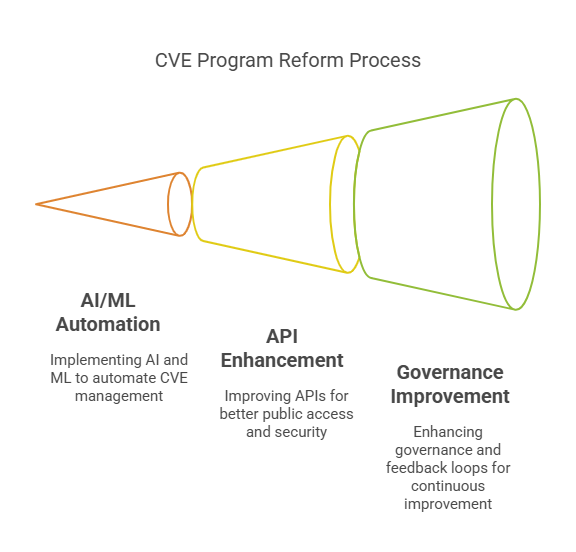
- Possible Reforms To Be Made
The 11-month contract extension for CVE program, to again state, is hopeful enough to suggest the following reforms to be made therein:
- AI/ML in CVE automation: To automate CVE management by analysing large datasets, identifying security flaw patterns, and recommending remediation strategies by utilising AI/ML models.
Better APIs and public access: To create well-documented, accessible, and secure APIs (Application Programming Interfaces) for the public with a degree of authentication. - Improved governance and open feedback loops: Ensuring continuous improvement within the CVE program by building a consistent and reliable system to label vulnerabilities. This will help enhance system responsiveness to the ever-evolving cybersecurity landscape.
The Bigger Picture: Why CVE Still Matters
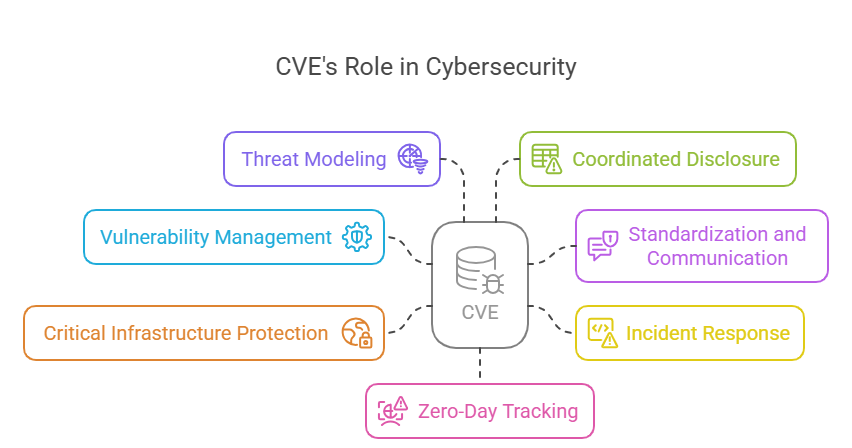
CVE undeniably remains crucial in the cybersecurity realm because of its effectiveness in underpinning the critical elements of the cyberdefense strategy. These comprise:
- Vulnerability Management and Prioritisation
- Standardisation and Communication
- Incident Response
- Critical infrastructure protection efforts
- Threat Modeling and Defensive Planning
- Ensuring a Secure Future
By fostering coordination, and collaboration in disclosing vulnerabilities, CVE acts as the central repository of vulnerability information for cybersecurity. Whether you belong to the red or blue team, SOCs, or are security vendors, you are bound to enhance your performance through CVE optimisation.
Also Read: Cybersecurity for Remote Workforces: Best Practices and Tools
- Coordinated Disclosure and Zero-Day Tracking with CVE
The coordinated vulnerability disclosure in CVE process has the security researchers to promptly report security flaws to vendors. This allows for patching/remediating the issue before disclosing it for public access. With zero-day tracking, the situation is entirely different. It involves monitoring and responding to security flaws that have been newly discovered and unpatched.
- CVE, A Trusted, Centralised Vulnerability System
CVE has been described as the common language of cybersecurity. It sets the centrestage for better communication, collaboration, and proactive security measures by offering proper reference points to identify, track, and manage vulnerabilities.
Also, through standardising vulnerability identification and communication, CVE helps facilitate proper assessment, prioritisation, and remediation of potential security flaws for organisations.
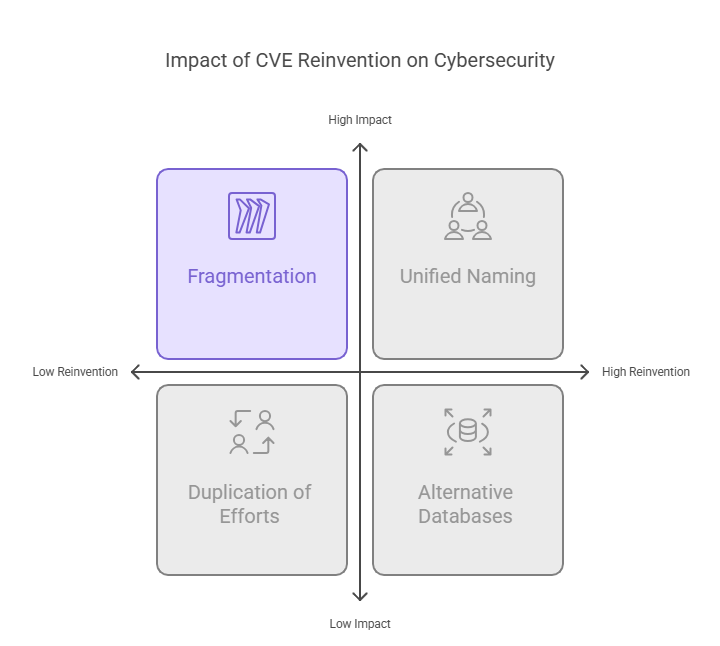
What If CVE Fails to Reinvent?
CVE, well-regarded as the lifeblood of the global cybersecurity community, should not diminish in importance. This statement highly suggests that this program should be resilient enough to support cybersecurity operations in the long run. Failure to reinvent the program no doubt signifies an end to cybersecurity functionalities – those being vulnerability identification, disclosure, and management. As individuals and organisations around the world, you can more likely expect ongoing cyber threats.
Other possible consequences can likely include:
- Risk of fragmentation
- Rise of alternative databases rise
- lack of unified naming.
- Duplication of efforts.
The news regarding the MITRE CVE program lapse left the global cybersecurity team shockingly hooked for a good long 48 hours till achieving temporary redemption from CISA . From expiry scare to extension for 11 months, this period calls for reviewing and reforming CVE program functionality in terms of vulnerability identification and disclosure to the public.
This 11-month extension also critically calls for supporting CVE’s evolution by revamping collaboration among industries, governments, and cybersecurity vendor researchers. Failing to do so means making way for decline in the CVE’s vulnerability tracking efficiency, leading to vulnerabilities in the entire cybersecurity landscape.
In our efforts to effectuate CVE functionality during this extension period, let’s come together to pledge that we can’t afford to lose CVE.
As a cybersecurity team, we at Wattlecorp know that sitting silently and letting CVE fade before our eyes means allowing vulnerabilities to kill us! This shouldn’t happen.
CVE FAQs
1. What is CVE vulnerability?
The CVE vulnerability signifies identifying, assessing, and publicly disclosing vulnerabilities found in the hardware and software. It serves to uniquely identify a disclosed vulnerability by assigning it a specific number. This makes way for easier communication and sharing of information about the identified vulnerability to prioritise, address, and remediate likely security flaws.
2. What does CVE vulnerability stand for?
The CVE vulnerability suggests weaknesses found within the software, hardware, or firmware that can likely be exploited. If no prompt actions are taken to mitigate these vulnerabilities, this can consequently lead to compromising system security. The CVE being a publicly accessible database, helps assign a unique identifier to the vulnerabilities disclosed.
3. How will the CVE program extension help cybersecurity?
The CVE program extension can remarkably help revamp cybersecurity strategies by having industries, individuals, cybersecurity researchers, and other relevant stakeholders communicate and collaborate on security issues effectively and efficiently.