As many businesses are moving to digital technologies, most of them are migrating to cloud solutions like Amazon Web Services. AWS has become a trusted platform as it helps in managing their operations more efficiently. It benefits in scaling up easily, offering everything from storage and databases to advanced AI and analytics. But with great convenience comes the need for extra caution—especially when it comes to security.
While AWS provides strong built-in protections, cyber threats are constantly evolving. This means companies using AWS must take additional steps to keep their data and systems safe. One way to do this is through penetration testing, which is like a mimic cyberattack designed to detect potential security gaps.
According to the latest study on cyber threats and pen testing, the size of the global Penetration Testing Services market is going to reach 9227 million US dollars in 2030. It proves that security threats are growing and AWS penetration testing is a biggest need in the future.
AWS penetration testing helps detect security vulnerabilities and offers suggestions on how to correct these vulnerabilities. Here you will be able to get an overview of AWS penetration testing, its significance, and how this could help in protecting your data and operations in the cloud.
Table of Contents
ToggleWhat is penetration testing in AWS?
This cyber security practice is like running a mock cyberattack on the cloud setup to find weak spots before real hackers do. The penetration testing in AWS is a controlled and authorized process. Here the security experts, also known as penetration testers, initiate real-world attacks to inspect the security of the AWS environment. After pen testing, the detailed report shows imperfections in security and denotes where to strengthen your defenses.
As AWS is a third-party platform, it’s important to follow Amazon’s specific rules and guidelines during penetration testing to prevent any system disruptions. Regular pen testing helps businesses keep their data and operations secure.
Shared responsibility model of AWS penetration testing
The responsibility of securing the AWS environment is shared between Amazon and its customers. Adding to this understanding this model is much needed for businesses using AWS cloud services.
Amazon’s Responsibilities
Amazon takes care of securing the core infrastructure that supports all AWS services. This includes the physical hardware, networking, data centers, and facilities that run the AWS Cloud.
Infrastructure layer of the cloud is managed by Amazon, making sure it remains safe from external threats and disruptions. These security measures are designed to provide customers with a secure foundation to deploy their services.
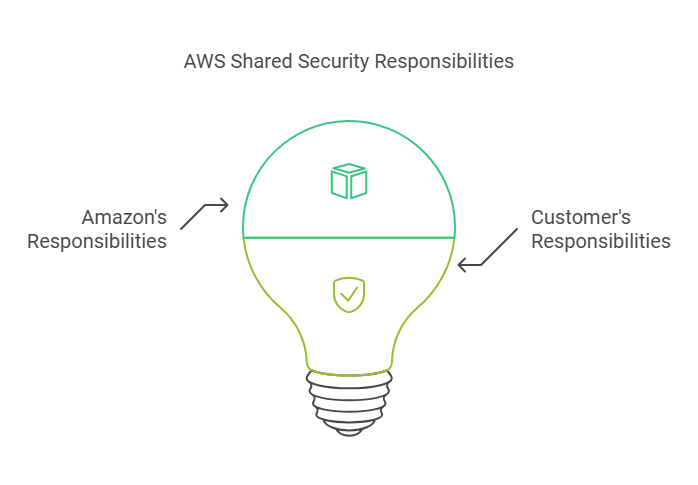
Customer’s Responsibilities
On the other hand, customers using AWS are responsible for securing their own resources and services running in the cloud. This responsibility includes:
- Customers must be aware that the operating systems of their instances (virtual machines) are properly secured, updated, and patched.
- They are also responsible for the security of any application software they install on AWS instances.
- Configuration of AWS security tools is important: Customers need to manage the security settings for tools like firewalls, network access controls, and security groups that are provided by AWS.
How to perform penetration testing on AWS
Performing penetration testing on AWS requires careful planning and precise execution for the surety of your security while minimizing any disruptions. Below is a detailed step-by-step workflow, highlighting each phase of the process.
1. Get the right permission
Before starting any penetration test on AWS, it is important to get proper authorization. AWS has strict rules around penetration testing, and performing tests without approval could lead to disruptions or even penalties.
You will need written consent from the AWS account owner or organization. If you are testing services that AWS does not officially allow for penetration testing, you may need to reach out to AWS support to get explicit permission.
2. Define the scope and objectives
Once you have completed authorization level, identify which systems, applications, and AWS services you want to test. Consider checking any specific compliance needs, such as industry regulations, and focus on areas that handle sensitive data.
Outlining the scope and objectives, will help you avoid any unnecessary risks or oversights during testing.
Also Read : Penetration Testing Trends In 2024: Staying Ahead of Cybercriminals
3. Set up a dedicated testing environment
To avoid causing disruptions in your live system, it’s best to create a separate testing environment within AWS. This means you will be testing on an isolated environment apart from your production environment.
The testing environment should include virtual instances, networks, and security groups configured solely for penetration testing. The result is that any action taken during testing won’t impact the original operations.
4. Map the AWS attack surface
It is important to understand the attack surface you are working with. Mapping out the AWS environment involves identifying all the services, instances, subnets, S3 buckets, IAM roles, and other components in use.
Analysing this will give a clear overview of the AWS infrastructure and associate where the most vulnerable points may lie. Techniques like network scanning and vulnerability scanning will help in finding hidden weaknesses in the environment.
5. Do vulnerability assessment
The purpose of any penetration test is identifying vulnerabilities. In AWS, you may find weak points in areas like IAM roles, S3 bucket permissions, EC2 instance settings, and network configurations.
During this stage, use tools like vulnerability scanners to identify misconfigurations or gaps in security that could be exploited. Also, reviewing logs, such as AWS CloudTrail logs, can help track user activity and spot any suspicious patterns that might indicate vulnerabilities.
6. Exploit the identified vulnerabilities
In this step, experts exploit the vulnerabilities to assess their severity. This test is done to check if these vulnerabilities can be used by an attacker to gain unauthorized access or cause harm.
This could involve testing weak access controls or misconfigured permissions. However, it’s crucial to only target your own resources and avoid affecting other AWS customers. The goal is to understand the potential impact of these vulnerabilities.
7. Review AWS security best practices
When you are preparing to perform pentesting evaluate whether your AWS setup follows AWS security best practices. This includes checking whether your configurations are aligned with recommended settings.
Watch if you are using services like Amazon S3, EC2, and IAM with secure configurations.
Also Reads : Most Common Penetration Testing Vulnerabilities Found In 2024
8. Deep service review: IAM and access control
A deeper review of your AWS services is necessary to identify how access is managed across the system. You have to thoroughly assess IAM roles and permissions. Verify that unused or inactive accounts are deleted.
Also limit permissions to only what’s necessary for each user or service. Enabling two-factor authentication and restricting access to service accounts are also crucial steps in securing your AWS environment.
9. Analyze network configurations and security groups
AWS provides numerous ways to control network traffic, including security groups and Virtual Private Clouds (VPCs).
During penetration testing, it’s important to carefully review these configurations. Keep your resources accessible only for trusted traffic and sensitive data encrypted while in transit. Misconfigured security groups or open ports could expose your system to threats.
10.Generate a detailed report and plan for remediation
After completing the AWS penetration testing, prepare a report defining all the vulnerabilities, their potential impact, and the steps needed to fix them.
This report should also include recommendations for remediation and best practices to follow moving forward. Share the report with the relevant team members or stakeholders explaining the identified issues to be addressed.
Does AWS allow penetration testing
Yes, AWS allows penetration testing, but this testing complies with certain boundaries to avoid disruption in the services. AWS encourages security testing to help identify vulnerabilities. In addition to the tests allowed there are also certain tests you cannot run.
Tests allowed
AWS allows penetration testing on specific services without needing prior approval. These include services like:
- Amazon EC2 instances
- Amazon RDS
- AWS Lambda
- AWS Fargate
- Amazon API Gateways
If you are testing services that you operate and configure yourself (like an EC2 instance), you have the freedom to test its security as long as it does not disrupt other users or the service itself.
Restricted tests
There are restrictions when it comes to vendor-managed services (those controlled by AWS or a third party). You cannot test the configuration and implementation of the service. Also, certain activities are strictly not authorized to test, such as:
- Denial of Service (DoS)/ Distributed Denial of Service (DDoS) attacks
- DNS hijacking or zone walking
- Protocol or port flooding
- Excessive request flooding (like login or API requests)
These restrictions are in place to protect the stability of AWS’s shared infrastructure and other users.
If you are not sure on which tests to run, checking AWS’s policies or contacting AWS Support would be helpful. Following these rules helps the testing process remain ethical, effective, and compliant with AWS’s terms.
Importance of AWS penetration testing
Securing your data and workloads in the cloud is a necessity for any organization using AWS. Experts can identify threats, protect sensitive info, and strengthen your cloud security through regular AWS penetration testing . This highlights the value of continuous security testing services in India in ensuring ongoing protection and addressing emerging vulnerabilities in cloud environments.
1. Protect data and workloads
Amazon AWS operates under the Shared Responsibility Model. This means that data and application owners are jointly responsible for protecting their information, application stacks, and workloads while in the cloud.
The best way to prevent unauthorized system access or any cyber-related attacks is penetration testing. After identifying weaknesses, experts can protect important information before facing data breach.
Also Read : Top Challenges in Enterprise Penetration Testing
2. Alignment with compliance and regulatory standards
Many industries are governed under HIPAA, ISO 27001, and SOC2, which strictly control several regulations. This mainly includes cloud-based data security. In case of failure to adhere to these regulations, some penalties may occur or reputational damage as well as legal obligation can happen.
AWS pentesting enables an organization to identify and fix vulnerabilities while showing commitment to data security to regulators and customers by complying with such standards.
3.Keep up with changing threats
The cloud environment is constantly changing, and systems, configurations, and features are constantly updated. Unfortunately, this can introduce new vulnerabilities, such as insecure APIs, weak authentication mechanisms, or misconfigured resources.

Continuous pentesting keeps organizations ahead of these changing threats by continuously evaluating and improving their security posture.
4. Increase customer trust
Data security itself acts as a gesture for organizations to show their dedication to protecting customer information.
AWS pentesting builds trust in your organization by showing that you are actively working toward the safety and confidentiality of customer data. This can be the competitive advantage required in markets that emphasize data privacy.
5. Identify and correct vulnerabilities
Pentesting finds vulnerabilities such as weak passwords, open ports, or misconfiguration that would otherwise go unseen. By resolving these issues, you can minimize entry points to attackers, and you will make sure that every aspect of your cloud infrastructure is secure.
6. Preventing downtime and data loss
The AWS setup could be vulnerable to unauthorized access, data leaks, and even system outage. Such incidents can critically affect your operations and thus lead to losses. With penetration testing, you identify and rectify problems before they get the chance to disrupt your business.
Freequantly Asked Questions
1. Is AWS penetration testing allowed, or will it violate AWS policies?
Yes, AWS penetration testing is allowed but you have to follow their guidelines. AWS provides a list of approved services and tools that can be tested. However, testing components outside the customer’s responsibility, such as the underlying cloud infrastructure, is restricted as per the AWS Shared Responsibility Model.
2. How much does AWS penetration testing cost?
The charges may vary between $5,000 to $50,000 or more. However, you can expect an increase in costs based on the size of your AWS environment and the depth of the testing required. The cost of AWS penetration testing usually depends on the scope, complexity, and expertise. Based on specific business needs, customization may cost even more depending on the tasks.
3. What specific areas of my AWS infrastructure will be tested for vulnerabilities?
AWS penetration testing typically focuses on:
Data security: Ensuring sensitive data is properly secured against unauthorized access or leaks.
Access controls: Checking authentication, permissions, and MFA setup.
Network security: Testing security groups, firewalls, and segmentation.
Application security: Analyzing vulnerabilities in deployed applications and APIs.
Configuration checks: Identifying misconfigured services or weak encryption protocols.







