SECURE YOUR BUSINESS WITH EXPERT VAPT STRATEGIES
How Secure Is Your Infrastructure? Book a Free Consultation with Wattlecorp’s Experts to identify vulnerabilities, develop a robust VAPT strategy, and safeguard your business with tailored protection solutions.

Every 39 seconds, a cyber attack occurs. Accumulating a staggering global loss average of 4.45 million dollars in 2023, we are seeing a 300% increase in cyber threats after 2019.
Cyber attacks are a constant and pervasive threat to businesses of all sizes. The financial losses associated with these attacks are staggering, impacting everything from operational efficiency to brand reputation.
Understanding the cost of cyberattacks across various aspects is needed for businesses to develop effective mitigation strategies. Our experts have curated this blog to give you a crystal-clear picture of the financial repercussions of cyber attacks, exploring the various costs a business might incur, the impact on different industries, and the long-term consequences for an organization.
Let’s dive deeper.
Table of Contents
ToggleBreakdown of Cyber Attack Costs
The real loss suffered during a cyber attack extends far beyond the immediate financial loss of stolen funds.

The associated losses include data breach costs, cyber attack financial losses, legal fees and regulatory fines, reputation damage, customer churn, and stock impacts. To understand these losses in detail, we’ll take a closer look.
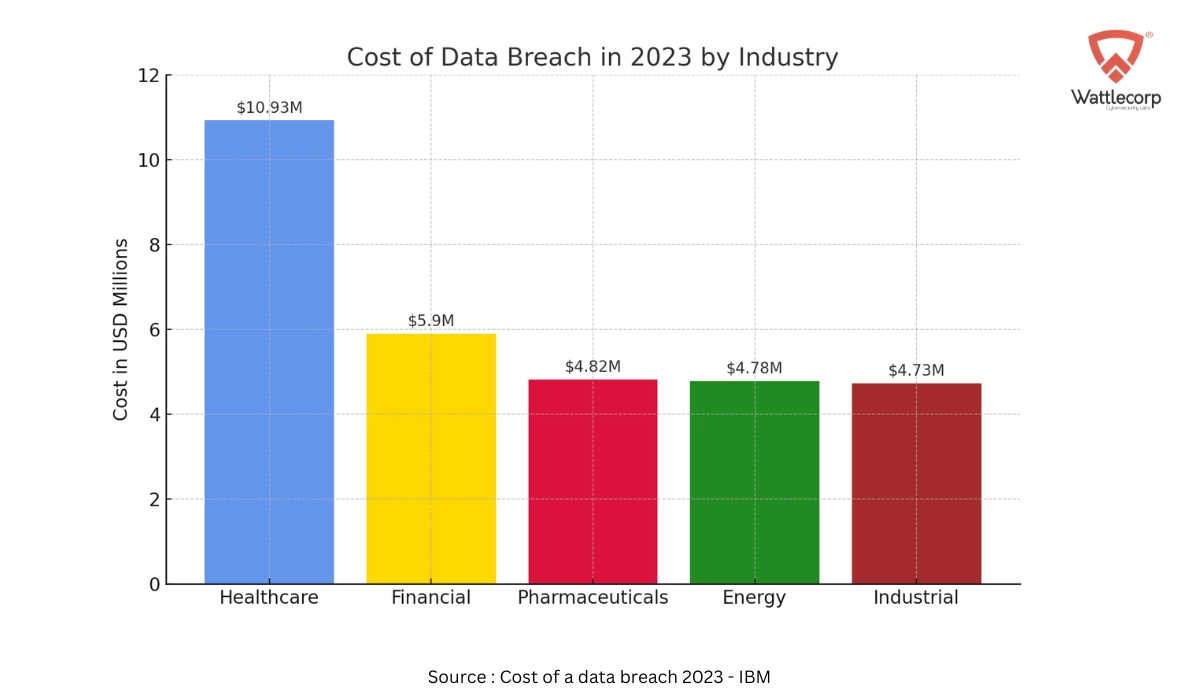
Data Breach Costs (average . global loss of $4.45 million)
When sensitive data like customer information or intellectual property is compromised, businesses face hefty costs for data recovery, forensic investigations, and credit monitoring for affected individuals.
- Forensic Investigation: Identifying the source of the breach, understanding the scope of the attack, and determining the data compromised.
- Data Recovery: Recovering lost or corrupted data can be a complex and expensive process, especially if backups are compromised or unavailable.
- Credit Monitoring: Businesses may be obligated to offer credit monitoring services to affected individuals to protect them from identity theft, adding to the overall cost.
- Regulatory Fines: Failing to adequately protect customer data can result in hefty fines from regulatory bodies, further compounding the financial burden.
Reputational Damage
According to a study by ISACA, the top five concerns about cyberattacks are:
- Impact on the Firm’s reputation—78%
- Impact on their professional reputation—29%
- Data breaches resulting in physical or financial harm—69%
- Supply chain disruptions—49%
- Loss of proprietary trade secrets—32%
In March 2024, an undisclosed number of American Express customers were notified of a potential breach of their data. The incident stemmed from unauthorized access to a third-party merchant processor, rather than their internal systems. Customers were informed of their names, account numbers, etc.
Data breaches and security incidents can severely tarnish a company’s reputation, eroding customer trust and loyalty. leading to customer churn, lost business opportunities, and a decline in brand value. You may need to spend a lot of time and money to rebuild trust.
Legal Fees and Regulatory Fines (€20 million or 4% of worldwide turnover)
Regulatory bodies are increasingly enforcing stricter data privacy laws. Failing to adequately protect customer data can result in hefty fines and legal fees, further adding to the financial burden of a cyber attack. Businesses may face lawsuits from customers affected by a data breach, incurring legal fees to defend themselves in court and incur extra losses.

In general, GDPR rules state EU authorities can impose maximum fines of €20 million or 4% of worldwide turnover, whichever figure is higher. In the UK, the Information Commissioner’s Office (ICO) can issue fines of up to £17.5 million or 4% of the total annual worldwide turnover, whichever is higher.
Data protection regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) impose hefty fines for non-compliance, especially in the case of data breaches.
Cost of Ransomware Attacks
Ransomware attacks encrypt a victim’s data, holding it hostage until a ransom is paid. This includes not just the ransom payment but also the cost of data restoration and lost productivity:
- Ransom Payment: While not advisable, some businesses choose to pay ransoms to regain access to their data. This payment incentivizes cybercriminals and fuels further attacks.
- Data Restoration: Even if a ransom is paid, there’s no guarantee that attackers will provide a decryption key. Businesses may need to restore data from backups, which can be a time-consuming and expensive process.
The Four Most Common Types of Cyber Attacks
The most common types of cyberattacks in 2024 are
- SQL Injection Attack
- Man In the Middle Attack
- Phishing Attacks
- Denial Of Service Attack
So let’s dive deeper and learn more about these common cybersecurity threats businesses face.
| Attack | Process | End Result | Staggering Stat |
| Structured Query Language (SQL) Injection Attack | The cost of a DDoS attack averages between $20,000-$40,000 per hour. | Malicious SQL codes are inserted into a victim’s database, to access private information. | 21% of organizations are still vulnerable to SQL threats. |
| Man-in-the-Middle (MitM) Attack | Hacks into a communication channel between two people, and eavesdrops on their online exchanges. | Steal login credentials, and personal information, or inject malicious software | Successful MITM threats cost businesses over $2.4 billion annually. |
| Phishing Attack | The cost of a DDoS attack averages between $20,000-$40,000 per hour. | Trick the victim into handing over their information. | Phishing attacks targeted 1339 brands in the fourth quarter of 2023. |
| Denial of Service Attack (DoS) | Making a victim’s network inaccessible by flooding their system with traffic. | Significant disruption to the victim’s services. | There is an average cost of $20,000-$40,000 per hour for a DDoS attack |
Cyber Threats and Protecting Your Business
Cybersecurity is all about a proactive approach. Businesses can significantly reduce the cost of cyber attacks if they follow some basic strategies.

Cybersecurity Budget for Small Businesses
Robust cyber security is not just for large organizations. SMBs are most often the prime targets for cyber security attacks. A cybersecurity budget for small businesses is of the highest priority, allocating a dedicated cybersecurity budget for implementing basic safeguards like firewalls, data encryption, and employee training.
Cybersecurity Insurance
Cybersecurity insurance can provide a safety net in the event of a cyberattack, helping to offset costs associated with data recovery, legal fees, and business interruption.
The key factor is choosing the right policy based on organizational needs.
Focus on Prevention
Preventive measures like firewalls, data encryption, and regularly updated software are far more cost-effective than recovering from a cyber attack.
- Firewalls: act as a barrier between your internal network and the internet, filtering incoming and outgoing traffic to prevent unauthorized access.
- Data Encryption: Data encryption scrambles sensitive information, making it unreadable to unauthorized users even if it’s intercepted.
- Software Updates: Regularly updating software with the latest security patches addresses known vulnerabilities that cybercriminals might exploit. Patching promptly is crucial for maintaining a robust defense.
Employee Training
Employees need to be aware of the cameras running around them. Basic knowledge of skill training to identify and avoid cyber threats like phishing should be considered a mandatory part of onboarding. It is important to inform them of:
- Phishing Awareness: Phishing emails are a common method for attackers to steal login credentials or trick users into downloading malware.
- Password Security: Strong password practices are essential for protecting user accounts.
- Social Engineering Techniques: Social engineering tactics leverage psychological manipulation to trick employees into compromising security measures.

Incident Response Plan
Always have a backup or a contingency plan in place. A well-defined incident response plan ensures a swift and coordinated response to an attack. Your business continuity plan should outline roles, responsibilities, and communication protocols to minimize downtime and damage.
- Detection and Containment: Establishing procedures for identifying and isolating a cyber attack to prevent further damage.
- Investigation and Eradication: Investigating the source and scope of the attack and taking steps to remove the threat.
- Recovery and Restoration: Restoring compromised systems and data from backups.
- Reporting and Communication: Having a clear communication plan for notifying relevant stakeholders, including law enforcement, regulatory bodies, and customers, if necessary.
Takeaway
So finally you have understood the cost of cyber attacks and how they affect business, as cybersecurity is an evolving and perpetual process with proactive measures and preventive policies. Your security posture must be regularly updated and adapted to tackle the new-age cyber security challenges. We, Wattlecorp, a pioneer in this industry, are here to help. We offer a comprehensive suite of cybersecurity solutions and services, from security assessments and penetration testing to managed security services for all businesses, and we always have something for you. Contact us today to learn more about how we can help your business build resilience against cyber threats.
Frequently Asked Questions [FAQ]
Direct costs are immediately associated with the incident, such as the cost of incident response, damage or theft of IT asset infrastructure, and regulatory fines.
Indirect costs: These are not immediately visible but can have a significant impact over time. Like unexpected downtime, loss of productivity, decreased morale, and damage to the company’s reputation.
Calculating your potential impact involves understanding, analyzing, and quantifying your organization’s cyber risk. This rigorous task requires significant expertise to gather and analyze large amounts of data, categorize risk, and calculate potential impacts across a range of scenarios. Even though there is software readily available for it, some organizations still opt for the manual approach.
The cost of hiring a cyber security expert is always less than the costs you suffer after a cyber attack.
Making a business case for investing in cybersecurity involves demonstrating the potential return on investment (ROI) that can be achieved through cost avoidance and fostering business growth.







