Popular culture has played an important role in opening up the world of hackers to the common person. Movies like Blackhat tv shows like Mr Robot and even games like Watchdogs 2 completely focused on hacking, while a lot of crime shows and detective movies relied on tech support/ethical hacker. This portrayal has been steadily increasing, while at the same time, these portrayals have fed a huge number of myths to the unsuspecting public.
While the concept of what hackers do, on both sides, is well understood by the general public these days, there are a lot of misconceptions as well. If you look at it, the portrayal has had both good and bad things to come out of it. The world of hackers is filled with myths and facts from all angles. It is difficult for the common man to distinguish between them.
Let us have a crack at it. While we can’t deal with all prospective confusions, let us look at 5 of each – 5 myths and 5 facts. Here’s the time to separate them from the root.
1. Your Password is Eternally Secure
Having a password filled with special characters and symbols is not enough to be safe from cybercriminals. No passwords are safe forever. There are chances of each password being leaked or cracked.

The only way to stay safe from being robbed of your password is by frequently changing the password. While it need not be daily or every other day, passwords need to be changed every once in a while.
Read More: How to Create Strong Passwords
Verdict: Myth
2. Rising Data Breach Charges
It is estimated that it costs a major enterprise at least Rs 25 crore to recover from a breach. While the costs are dependent on a lot of factors, they can be basically boiled down to one thing – the scale of the attack. If the number of attacks is increasing over the past few years, it makes sense that the massiveness of each attack also increases.
If the attacks get bigger and meaner, it is understood that the costs involved in recovering and getting back on track after a breach would be more as days progress. The rising costs aren’t surprising for someone who follows and analyses the patterns. The size of data lost in an average breach has gone up by 3.9% since 2018. This itself can be a huge parameter that leads to an increase in financial losses. With just below 30% of global organizations expected to be targets of cybercriminals within the next 24% months. For all these reasons, it is quite evident that the costs related to such data breaches are high.
Verdict: Fact
3. Frequent Cyberattacks
Research conducted by Maryland University states that a cyber attack happens as frequently as 39 seconds.

The most common among these attacks is a basic dictionary attack on the most commonly used usernames and passwords. Insecure usernames and passwords lead to higher success rates for hackers. Successful root access opens up the entire computer to the hacker.
Verdict: Fact
4. All Threats are External
Quite a common misconception, all threats aren’t purely external for an organization. Researches state that almost 75% of data breaches are a result of someone on the inside.

The people on the inside could be a disgruntled employee, an ex-employee out with a grudge, or even an unsuspecting employee who fell victim to a social engineering attack or someone ignorant who granted access to the entire organization’s data.
Organizations that train their employees in the safe practices that can be taken from their side to avoid such cyber threats reduce the chances of such problems. A common reason for the rise of such threats is the negligence of cyber-awareness protocols.
Verdict: Myth
5. Rise of IoT-Connected Devices
There were roughly 9.5 billion IoT-connected devices by the end of 2025. That number is expected to reach 75 billion by 2025. While this increasing number is a parameter to show the technological advancements done by the world and their reach to people, it brings its own set of problems.
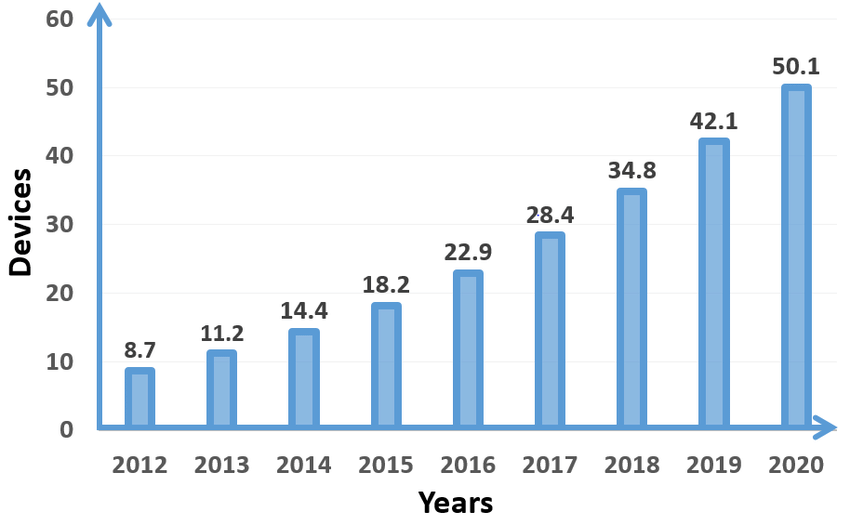
More devices create more opportunities for hackers. Having more IoT-connected devices in a network opens up more entry points that hackers can exploit. With most IoT-connected devices having minimal to no security protocols at the moment, it is a minefield for hackers.
Verdict: Fact
6. Bringing Your Own Device is Safe
A lot of companies opt to ask employees to bring their own laptops and ask them to bring their personal devices to work. This is economically viable for the company and helps small to mid-range companies which don’t have the budgets to allocate to get laptops for each employee.

At the same time, companies forget to think about the security impacts this could create. In places where Bringing, Your Own Device is the norm, every employee has at least two devices – a laptop and a smartphone, apart from others. When each of them is connected to the network, it opens up new entry points for the hackers. Before allowing staff to bring their own devices, companies should make sure that they follow the best cybersecurity policies and adhere to the rules and regulations of the company.
Verdict: Myth
7. Your Organisation is Safe
No organization is 100% safe from cyber threats. Every industry is at risk. If your company is connected to the internet, you are at risk of getting attacked in one way or the other.

Unlike movies and tv shows that show you only the tech and finance industries are prone to cyberattacks, every industry has a target on its back. Even if your company doesn’t have an e-commerce website, you can be attacked by breaking into your organization’s network.
Verdict: Myth
8. The Most Expensive Virus Originated in 2004
MyDoom, a Russian virus that originated in 2004, has incurred the biggest financial damages. The financial damages of MyDoom go close to 290 billion rupees. The author of the virus hasn’t been discovered yet.

The virus spread quickly through email worms. The far-reaching and rapid spreading allowed it to bag the title of the most expensive virus. If a user was infected by the virus, it created network openings that allowed others to access the computer. Apart from that, the virus also opens random programs on your computer. By the end of 2004, an estimated 25% of all emails were infected by the virus.
Verdict: Fact
9. The IT Department can Handle Cyberthreats
When one thinks of the department in a country that will handle cyber threats, everyone’s first answer would be the IT department. Yes, the IT department does do a few things connected to stopping cybercrime but they can’t take care of everything.

The IT department will implement and review policies, monitor the network, and take necessary action in the face of cyber threats. But the final responsibility lies on each employee’s shoulder to ensure that they report any threats and follow the guidelines issued by the company.
Verdict: Myth
10. Cybercrime Damages to Reach an All-Time High
Cybercrime has grown from simple viruses that pop up random messages to complex and sophisticated ones that make their presence known only after crippling the organization’s entire server, spreading from one organization to the other. Cybercrime has become the most rapidly growing crime in the US. The increasing complications and sophisticated cyberattacks are a sign of developing times.
All these rack up huge costs for organizations that become victims. Reports state that damages incurred by cybercrime could go up to $6 trillion by 2021. Cybercrime costs include damage and destruction of data, stolen money, lost productivity, theft of intellectual property, theft of personal and financial data, embezzlement, fraud, post-attack disruption to the normal course of business, forensic investigation, restoration and deletion of hacked data, and systems, and reputational harm.
Verdict: Fact
Interested to bust more myths in cybersecurity and learn the truth about them? Follow our blog to keep yourself updated with the latest trends in cybersecurity.








1 thought on “Cybersecurity Myths v/s Facts : Unraveling The Truth”
Thank you for your valuable information.