SECURE YOUR BUSINESS WITH EXPERT VAPT STRATEGIES
How Secure Is Your Infrastructure? Book a Free Consultation with Wattlecorp’s Experts to identify vulnerabilities, develop a robust VAPT strategy, and safeguard your business with tailored protection solutions.

Cyber attacks are rising at a greater pace, creating challenging times for governments, businesses, and many other organizations. This makes them move with cybersecurity measures to strengthen security. Here, penetration testing comes. It is one of the most crucial methods to determine the cybersecurity threats. With penetration testing gaining popularity, it is estimated to reach a $4.5 billion market by 2025.
Penetration testing aims to determine the further weaknesses within the system and eliminate the gaps that give hard times. Besides addressing system weaknesses, it exploits them with ethical hacking.
If you are not sure where the penetration testing role holds the power to detect all the hectic security vulnerabilities or attacks, keep reading. Here, we will cover the list of 5 most common cybersecurity threats uncovered by penetration testing.
Table of Contents
Toggle- 5 Must Know Threats Detected By Penetration Testing
- 1. Weak Passwords
- 2. Unpatched Software and Systems
- 3. Misconfigured Security Controls
- 4. Social Engineering Attacks
- 5. Insecure Application Development
- Why Is Penetration Testing Important?
- Types Of Penetration Testing
- How should you react after passing a pen test?
- Frequently Asked Questions (FAQ)
5 Must Know Threats Detected By Penetration Testing
Cyber attacks can impact the entire business operations and damage the reputation to a greater extent. With penetration testing, you can neutralize most of the cyber threats. Here are some of the most common cyber threats detected by penetration testing.
1. Weak Passwords
Weak passwords are among the most common and easy targets for cybercriminals to enter the system. By implementing penetration testing, businesses can fix the weak links and do all the possible things to strengthen cybersecurity.
However, reusing the password at multiple places can raise the risk of attacks, which makes it easy for cybercriminals to use compromised credentials to attack the system.
2. Unpatched Software and Systems
Outdated and unpatched software is the most common cyber threat that allows attackers to exploit the vulnerabilities to gain unauthorized access. Penetration testing is the solution here that can easily discover the root behind the attacks, and the major risk is critical security patches not applied on time.

It is recommended to check for these vulnerabilities within the other systems, including operating systems, network devices, and third-party software.
Before completely relying on security measures, an organization needs to take some prior action, like prioritizing timely patch management practices to prevent unpatched software and systems from posing risks.
3. Misconfigured Security Controls
Misconfigured security control is yet another cyber attack that penetration testing uncovers conveniently. Misconfigured security controls, like routers, firewalls, and access control lists open the way to cyberattacks.

With penetration testing, you can quickly discover vulnerabilities and future issues. As a result, you can take security measures to fill the security gaps and strengthen the network system.
4. Social Engineering Attacks
Cyber threats have touched psychological manipulation where attackers infringe on the user’s identity to gain access to personal and financial information.

This is where penetration testing plays a vital role in uncovering the attack scenarios to determine vulnerability to social engineering attacks, such as phishing. With the right cyber security training and security awareness, businesses can eliminate most cyber attacks.
5. Insecure Application Development
Penetration testing plays an important role as a light for businesses to uncover security compromises in application development. Within insecure application development, the attacker exploits vulnerabilities in custom or third-party applications to gain unauthorized access or manipulate sensitive data by exploiting logic flaws, input validations, or authentication mechanisms. Penetration testing, as part of continuous security testing services in India, ensures that such vulnerabilities are promptly identified and mitigated, providing ongoing protection for SaaS applications.
Why Is Penetration Testing Important?
The penetration testing process is an important component of any cyber security strategy. Security testing helps organizations validate their systems, applications, and networks. The penetration testing role is to identify flaws in security before criminals do. A penetration tester launches a simulated attack to discover security holes. In this way, an organization can identify and fix flaws before criminals can exploit them.
Types Of Penetration Testing
Pentesters may be tempted to conduct a general test in which they “test everything”. However, by doing this, they will only scratch the surface of several vulnerabilities.
This means it would be possible for them to miss important intelligence by concentrating on just a few areas. Different pen tests focus on different parts of an IT infrastructure to ensure they’re effective. Here are a few :
1. Network Penetration Testing
It is the most commonly performed type of pentest. Testing the network infrastructure of your organization for weaknesses and vulnerabilities is the goal of network penetration testing.

The ethical hacker runs tests locally and remotely when conducting this type of pentest. The tester will target the following areas of the network:
- IPS deception
- Firewall configuration testing
- DNS level attacks
- Stateful analysis testing
It is important to perform network service penetration testing to safeguard your organization against network-based threats.
- DNS level attacks
- IPS/ID evasion attacks
- SSIT attacks
- Router attacks
- Unnecessary open port attacks
- Man in the middle attacks
- Proxy server attacks
- Database attacks
2.Web Application Penetration Testing
Web application penetration testing is among the most crucial types of penetration testing undertaken by businesses to evaluate vulnerabilities in web applications. The penetration testing for the web application will include browsers, web applications, plug-ins, and so on.
Increasing threats and the complexity of web applications require more time for penetration testing to plan and execute as techniques evolve.
A pentest of this type is mainly performed to uncover security flaws in your web-based applications and their back-end network components, databases, and underlying code.
Additionally, it provides solutions to mitigate determined vulnerabilities and helps prioritize them.
3. Social Engineering Penetration Testing
A pentester performs a social engineering penetration test to get sensitive information from users, such as their passwords and usernames. Several common attacks pen testers use, including:

- Phishing attacks
- Smishing (using SMS)
- Imposters
- Vishing (using Voice)
- Pre-testing
- Eavesdropping
Penetration testing with social engineering is an integral part of pen testing. According to recent statistics, social engineering accounts for 98% of all cyber attacks.
4. Physical Penetration Testing
Pentesters simulate real-world threats by attempting to breach physical barriers to access an organization’s infrastructure, employees, and systems.
It is imperative to perform physical penetration testing because most businesses neglect physical barriers, but malicious actors can damage your server room if they are allowed access.
Conducting physical penetration testing to find out what vulnerabilities exist in cameras, locks, sensors, and barriers is useful.
5. Different Approaches To Penetration Testing
As with all types and testing methods, pen testing can be approached differently depending on the tester’s qualifications and access rights.
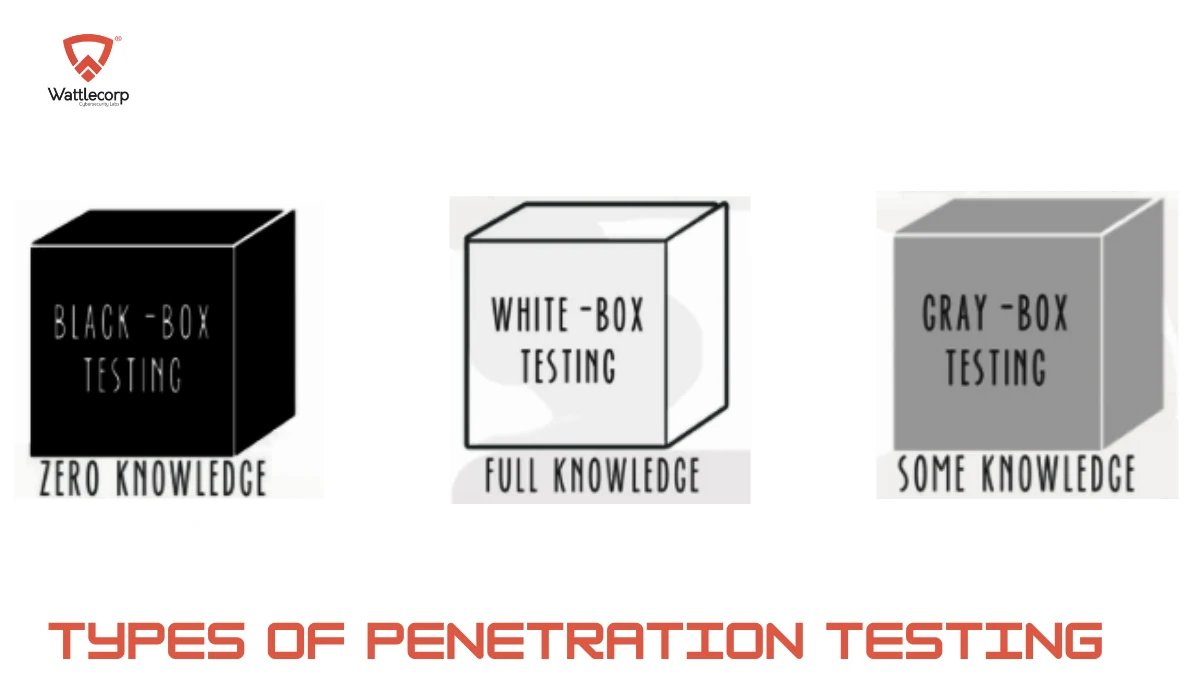
There are 3 main types of pen testing: white box, black box, and gray box.
- White-box Penetration Testing
White-box pen testing involves testers having full access to the system and knowledge of it. In addition to allowing for in-depth testing, this approach may be able to uncover vulnerabilities that are difficult to locate or remote.
- Black-box Penetration Testing
The black-box penetration testing is an approach that involves penetration testing without knowing the system’s inner workings. A tester would design the pen tests as if the tester were an uninformed attacker. Using this method is most similar to working with real-world systems, where hackers can’t access the source code.
- Gray-box Penetration Testing
Grey-box testing lies between white-box testing and black-box testing. As a result, the pen tester will have a limited understanding of the system.
Also Read: 7 Key Phases To Successful Penetration Testing- Complete Process & Tools
How should you react after passing a pen test?
It consists of patching real-life, tested vulnerabilities and developing a long-term security strategy. Taking action on pen test results quickly is crucial to avoiding cybersecurity breaches, downtime, and fines associated with those who violate data protection laws.
When you have completed your penetration test, make sure you:
- Discuss the findings with your in-house cybersecurity team and the external pen testing team
- Putting together a cybersecurity strategy that includes remediation
- Make sure your patches and upgrades are succeeding and progressing by repeat testing and vulnerability scanning
Pen tests are designed to be comprehensive. The reports provide detailed information about a system’s potential weaknesses and their severity. Therefore, you can always rely on actionable findings to help you strengthen your security.
Penetration Testing is a great way for an organization to determine the cybersecurity threats within the system. From large to small businesses, penetration testing holds something for every business prioritizing security within the business environment. If you have not started implementing penetration testing for your businesses, it’s time to begin now and open wonders of security for your business. Get hands-on with the best penetration testing practice and witness your business operating in the secure stage.
Frequently Asked Questions (FAQ)
Yes, penetration testing works for all types of businesses in determining the cyber threats and taking the best possible security measures to address the concern.
Penetration testing plays an important role as it helps businesses get into the details of security threats. With penetration testing, businesses get a stage to identify vulnerabilities that need to be taken care of actively.
Yes, penetration testing is great for discovering all the common cyber threats that can push businesses backward. With penetration testing, you will not be in the dark regarding the attacks damaging your business reputation.
Penetration testing is a highly effective measure for businesses to locate and address security gaps before they become severe and open up to cybercriminals.
Penetration testing has a bright future in the business world, where cyber attacks are inevitable, and penetration testing is the perfect fit to define the attacks and address them on time. Businesses are taking a positive approach towards implementing penetration testing to eliminate security vulnerabilities.








