For cybercriminals, APIs have been the source of frequent attacks. As a vulnerable hit, it needs careful handling. A security breach is a gateway that gives unauthorized access to sensitive data. This results in identity theft, financial losses, and much more.
The implementation of key security measures is an integral aspect of creating a secure ecosystem for users while encompassing the API security basics. This blog includes the most awaited API security testing checklist with the actionable measures that ensure your APIs are super-secure.
Table of Contents
ToggleWhat is an API Security Checklist? How to Use it?
API security best practices checklist enforces a list with necessary security methods to create a technical standard. This strengthens APIs to fight against possible cyber threats.
Each time a patch gets released, the build undergoes an update, or the source code gets tweaked, you should run a whole API security check. It lets you eliminate loopholes when you remediate an existing problem. This persuades organizations to use automated API security tools to completely attain visibility and API coverage, ensuring high security.
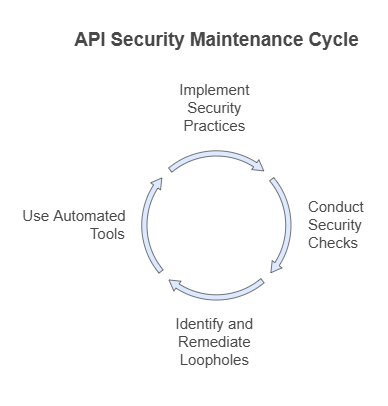
API Security Testing Checklist- Actionable Steps
Now, let’s learn the most significant tasks and security measures you need to consider for API security. As this isn’t an exhaustive list, you can consider adding to it with items specific to your process.
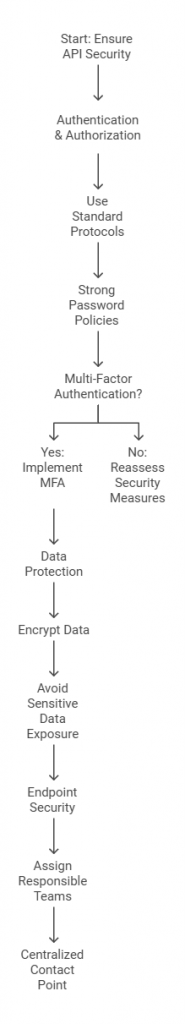
- Authentication & Authorization
Your basic line of defense is ensuring that only legitimate users can access your API. The use of relevant authentication and authorization protocols can avoid unauthorized access and possible data breaches. Use standard authentication protocols. For example OAuth 2.0, JWT. An appropriate use of JWT ensures that tokens are created, transmitted, and stored with high security.
- Adopt strong password policies.
- Implement Multi-Factor Authentication as required.
- Use attribute-based or role-based access control.
- Test the business logic of the authorization policies.
- Use API gateways.
- Deploy Web Application Firewalls(WAF).
- Data Protection
Data, particularly sensitive data, has become a breeding ground for cyber-attacks. Data protection in transit and while at rest makes it secure enough so that attackers can’t crack the data even if they get access. With a detailed API assessment process, you can identify vulnerable endpoints, and make sure the sensitive data is well protected.
- Encrypt data in transit and at rest.
- Avoid exposure of sensitive information in URLs.
- Encrypt sensitive information in API responses.
- Ensure that the endpoints adhere to the principle of least privilege.
As each API endpoint signifies a possible entry point for the invaders, it is important to ensure that every endpoint remains secure for high API security.
Also Read: OWASP API Security Top 10 (2024 Updated )
- Know the Responsible Hands Behind API Security Testing & Maintenance
Different teams are involved in the API lifecycle. Hence the project could undergo many changes and iterations. It is necessary to assign a person for API documentation and make sure the tests are completed and the results are implemented.
With a huge focus on web app environments and Cloud services, more business units and various app owners might be involved in the API security governance. It makes it more necessary to have a centralized point of contact.
- Budget Time and Resources Required
Security testing needs more time and money; hence businesses should think about these factors while commencing a project. Threat modeling outlines the potential API threats and vulnerabilities that demand addressing. However, a budget to maintain and update tests after the project is live is also essential. Note that any APIs the third-party providers develop and maintain can change at times. Security and app teams should adhere to accommodating project cycles and dynamic API checks.
- Input Validation and Output Encoding
Attackers usually exploit under-validated input to activate malicious codes and commands. An appropriate input validation and output encoding eliminates such vulnerabilities.
-Validate all input data
– Utilise parameterized queries
– Encode output
– Leverage a strong type system
- Adopt Transport Layer Security
Being an essential layer of security to API communications, TLS (Transport Layer Security) encrypts the information transmitted between the API and the client. This prevents attackers from eavesdropping, message forgery, or tampering. You need to make sure that the APIs follow the latest TLS version and configurations to improve overall security and prevent known vulnerabilities. Encryption ensures that sensitive data like personal data and authentication credentials remain secured while transiting over the Internet.
Adhering to TLS is a basic security measure for APIs as it eliminates data breach risks and ensures data integrity and confidentiality. Using TLS also supports compliance with different data protection standards that often demand data encryption in transit.
- Register, Classify, and Document API uses and its functions
Document APIs and their applications. This data lets tests evaluate whether an API can manage acceptable/unacceptable actions and valid/invalid information. Humans and machines can explore and learn API capabilities with standards like OpenAI specification, GraphQL, and AsyncAPI. Different API tools use the specifications to improve the overall API development lifecycle.
- Run Tests Beforehand & Automate Whenever Possible
Everyone can save cost and time once security concerns are detected early in the development lifecycle. There are many API security tools accessible, open source, and licensed. It facilitates integration with the present workflows and CI/CD delivery pipelines. Tools that include mocking services eliminate the necessity to create full-scale replicas for the production systems. Additionally, learn who is performing the tests and when they should run. It is ideal to run tests for every build of the application. Different API testing tools can be now completely integrated for continuous/ triggered testing.
- Define Various Test Types to Run
Subject API Security assessments to the tests as below:
- Invalid Inputs: Handling API inputs should be in such a way that they come up from an untrusted source. Fuzzing is a process of sending random data to the API and finding out if it can handle unexpected data without any crashes.
- Injection Attacks: Use test attacks to make sure that API rejects requests that make an effort to manipulate the backend database.
- Parameter Tampering: Parameters passed with an API request, like the price of an item in the cart, are easier for the intruders to change. With parameter tampering, you can check that the API validates and sense-checks parameters before they are processed.
- Unhandled HTTP methods: Send requests with HTTP methods to restrict unnecessary methods like CONNECT, DELETE, PUT, or TRACE from being allowed to the server. The methods can raise a security risk if they return a valid response instead of an error.
- Business Logic Vulnerabilities: Design flaws and API implementation can cause an attacker to induce undesirable behavior through unintended API interactions. Testing is difficult for these vulnerabilities with automated tools as the issue is unique based on its application and function. With a clear design and data flow documentation, encompassing assumptions at every phase lets you prevent these kinds of vulnerabilities.
- Excessive Loads: The number of times API can be called in a period, called Rate limit controls stop unapproved connections, and make it secure against DDoS attacks.
- Perform Regular API Vulnerability Assessments
Implementing regular API vulnerability checks, such as those offered through API Penetration Testing Services, is an important step to identify and address security concerns before they get exploited. Automated scanning mechanisms can detect multiple vulnerabilities like misconfigurations, insecure coding practices, and unpatched software with in-depth insights into the API’s security posture. Integrating these scans into development and deployment processes ensures flawless security assessment. Regular vulnerability scan lets organizations stay at the forefront of potential threats by proactively remediating vulnerabilities. Being a part of the API security strategy it lets you ensure the key aspects of API services, such as integrity, availability, and confidentiality.
- Fix Tests that Fail and Perform Retests
Share reports to a designated person to fix errors and ensure warnings. Retest to make sure that the code is updated and solves the problem. Vulnerability management experts should also confirm exceptions that demand approval from concerned stakeholders. For third-party APIs that don’t fulfill security requirements, create a plan to correspond with the service provider and retest.
Revealing too much data in the error messages can hint to attackers about the potential vulnerabilities and the system configurations. Refrain from showing detailed error messages or stack traces. Also, log errors to conduct internal reviews.
Also Read: API Security Testing: A Comprehensive Guide [2024]
- Update Documentation and Adopt Best Practices
You need to understand the advanced techniques cybercriminals use to attack APIs. This enables updating code, conducting tests, and adopting security controls. The security team should update everyone involved in the project regularly. The following OWASP top 10 API security checklist is a good source to begin with protection against vulnerabilities:
- Broken Object Level Authorization
- Broken Authentication
- Broken Object Property Level Authorization
- Unrestricted Resource Consumption
- Broken Function Level Authorization
- Unrestricted Access to Sensitive Business Flows
- Server-Side Request Forgery.
- Security Misconfiguration.
- Inappropriate Inventory Management.
- Insecure API Consumption
APIs are the most exposed network elements and have fallen under attack, causing various data breaches. Due to the increased security risks, API testing should stay at the heart of every project.
- Follow Zero-Trust Security
Ensuring zero-trust security principles for API architecture ensures that no system or user is trustworthy by default. This approach demands identification and authorization verification for systems and users per every transaction, minimizing the risk of unauthorized access. Zero-trust security is implemented regardless of the network perimeter and relies on powerful authentication, API interaction tracking, and least privilege access controls.
Even though the API security audit checklist encompasses a huge range of API vulnerabilities, this list keeps updating and evolving against the hackers’ techniques and methods of attacks. Abusing legit API functions to enjoy data access or implementing actions, which are not permitted, gives hackers the privilege of causing damage. With advanced tools and technology measures that track APIs round the clock, it helps you stay ahead of cybercriminals. Our cybersecurity experts at Wattlecorp help you stand against potential vulnerabilities with appropriate API security checks and implement vulnerability scans for your APIs to remain resilient and secure. Let’s connect today to learn how we adopt a secure API ecosystem and avail of our services.
API Security Testing Checklist FAQs
1.What common mistakes should I avoid when conducting API penetration tests?
Neglecting the test, authorization, and authentication, causes escalation attacks due to the exposed APIs. Depending on static test cases or OWASP top 10 API is not enough to detect API- led vulnerabilities. Also, understanding the business logic flaws and not simulating real-world attacks can cause missed security gaps.
2.What types of attacks can API penetration testing help prevent?
API penetration testing can identify invalidated input points to avoid attacks including command injection, SQL injection, and XML injection. It also eradicates risks like brute force attacks, object-level authorization, session hijacking, etc.
3.How often should API security testing be performed to stay secure?
It is ideal to conduct API security testing regularly, preferably with integration into the CI/CD pipeline to maintain alignment with the development cycle. You can ensure security by performing tests quarterly, after the code changes, or before core releases.