As organizations are making progress digitally day by day, cyber threats are also on the rise. The best way to keep your organization away from Cyber intrusion is to take precautionary steps. The attacks come unalarmed and can also come from any direction and it might be from inside or outside your organization.
You might have known about external penetration testing, where experts imitate attacks from outside your network. But what happens when the threat comes from within? That is where internal penetration testing is needed for an organization.
This internal attack can happen as an intentional act or an unknowing employee falling prey to a phishing email or other internal security vulnerabilities. Severe breaches can happen if left unchecked. These attacks may happen through social engineering or even weak internal practices.
internal penetration testing helps in identifying internal security fallback and finding weaknesses which are hard to recognize from the outside. Here is everything you need to know about internal penetration testing and how it helps improve an organization’s cybersecurity.
Table of Contents
ToggleWhat is an Internal Penetration Test?
Internal penetration testing, also called internal pen testing, is a security assessment. This testing evaluates how easily a threat actor can access systems and sensitive information within an organization’s internal network. Our services like Web Application Security Testing Services in India also play a vital role in identifying and mitigating security vulnerabilities in web applications that may extend to internal networks. It simulates what could happen if an attacker bypasses external defences and gets access to the internal system. Running this test helps to identify vulnerabilities that could lead to significant security risks.
During an internal pen test, ethical hackers mimic real-world threats to identify potential risks like:
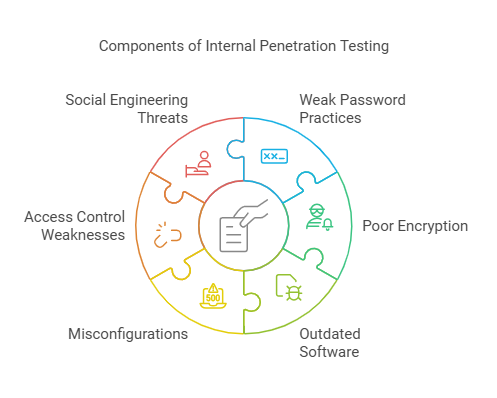
- Weak password practices- Issues like single-factor authentication or easily guessed passwords.
- Poor encryption- Insecure methods of protecting sensitive information.
- Outdated software– Vulnerabilities due to unpatched or old systems.
- Misconfigurations- Mistakes in system settings that could allow unauthorized access.
- Access control weaknesses: Gaps in who can access sensitive systems or data.
- Social engineering threats: Simulating phishing or manipulation of employees to gain access.
Internal vs External Penetration Testing
When many growing companies are falling prey to cyber threats, penetration testing is becoming a feasible security practice. There are two main types: internal and external penetration testing. Each serves a unique purpose and both tests are essential elements for a strong security-compliant organization. External penetration testing works on the outside-in approach.
It simulates attacks from an outsider’s perspective, aiming to identify vulnerabilities in your network’s perimeter. Security experts test for common entry points like open ports, weak firewall configurations, exposed web applications, or phishing scams. These tests assess how easily an external attacker can gain unauthorized access.
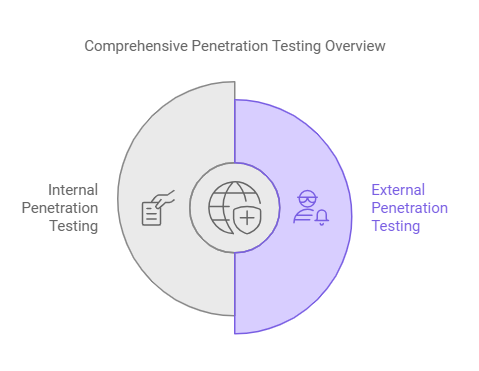
On the other hand, internal penetration testing is about testing the inside. It examines what could happen if an attacker—either a malicious insider (in-house employee) or someone who has already breached the perimeter.
Internal pen testing is to analyse if the attacker can gain access to your internal systems. This type of testing highlights weaknesses in internal controls, such as misconfigured permissions, unprotected sensitive data, or vulnerable endpoints. It gives an outline of the damage that could occur after the initial breach.
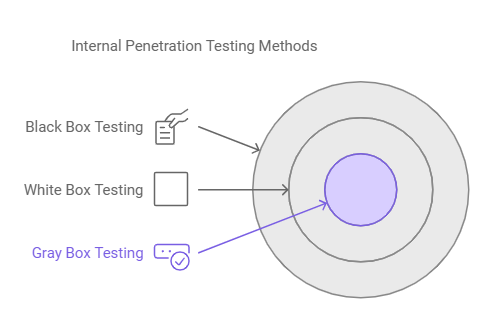
Internal penetration testing methods
Internal penetration testing uses different methods to mimic real-world scenarios and evaluate the security of internal systems. These methods are typically categorized into Black Box, White Box, and Gray Box testing approaches, each tailored to simulate different attacker profiles. Here’s a simple breakdown:
1.Black Box Testing
Black Box testing is an approach where the tester has no prior access to sensitive data or internal system details. Here, the tester operates as an external attacker who has managed to connect to the organization’s network (e.g., by physically plugging into a network port, connecting to Wi-Fi, or compromising non-domain equipment).
The main goal is to gain valid access to internal systems, such as a user workstation or server, without predefined permissions. This method is time-intensive but offers valuable insights into how attackers might exploit unknown vulnerabilities to penetrate the network.
Also Read: AWS Penetration Testing: Checklists, Tools, Strategies, and Best Practices
2.White Box Testing
White Box testing is done on the tester’s full knowledge of the internal systems, such as schematics, IP addresses, credentials, and source code. This approach intends a thorough and detailed examination of vulnerabilities, as testers have complete visibility into the infrastructure. White Box testing is best for identifying deep-seated issues that attackers with insider knowledge might exploit.
Through this testing, organizations gain a comprehensive understanding of their security posture. In addition to this, it requires more planning and resource commitment.
3.Gray Box Testing
Gray Box testing is the midpoint between Black Box and White Box approaches. The tester then has partial access to an internal system; for instance, he may have a valid account that is not administrative. A mock-up of an attacker who broke an employee’s credentials and is using that employee’s account due to phishing or got some device connected to the network is also one of his objectives.
By utilizing this restricted access, the testers try to escalate the privilege and obtain access to the sensitive assets like administrator accounts or critical data. The most effective technique to test for insider threats and privilege escalation vulnerabilities is through Gray Box testing.
How to Conduct Internal Penetration Testing
Internal penetration testing is a step-by-step testing process done to find and analyze the security strengths and loopholes of an organization’s internal systems. Here’s a simple and easy-to-understand flow with the key stages:
1.Plan and set goals
The first step is to plan the testing process. This involves clearly defining the scope of the test—what systems or areas need attention? The testing objectives, such as evaluating password security or identifying access loopholes, are also determined during this phase. This preparation ensures that the testing is focused and effective.
2.Collect information
Next, the testing team gathers detailed information about the organization’s network and systems. This could include identifying key devices, mapping the network structure, and analyzing how data flows within the system. The collected data helps testers choose the right tools and strategies for identifying potential vulnerabilities.
3.Identify vulnerabilities
At this stage, testers examine threats from the information they have collected. Weak spots in the network are spotted using methods like automated scanning tools, brute-force attempts, or even social engineering methods. These vulnerabilities are then checked to understand how they could be exploited.
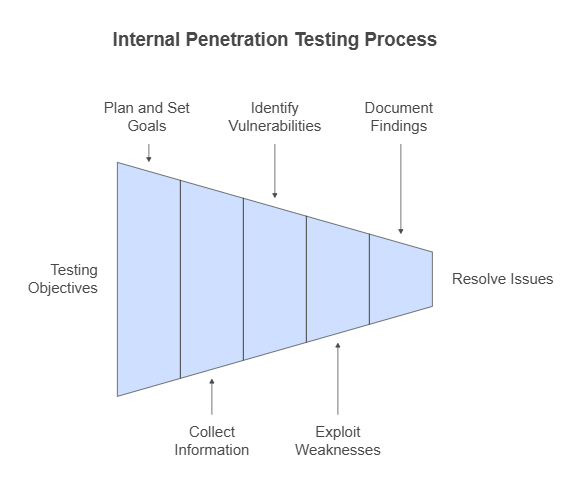
4.Exploit the weaknesses
The actual testing happens at this phase. Here professionals like Wattlecorp experts use advanced tools and techniques to exploit the vulnerabilities they have tracked. This helps the experts assess how an attacker might gain access to sensitive data, take control of systems, or disrupt operations. The extent of damage that is possible through a real attack can be found this way.
5.Document the findings
After completing the testing, the team records the instances they identified. The findings include the vulnerabilities discovered, the way it was exploited, and the potential risks associated. The report also provides insights into the systems’ strengths and weaknesses, explaining the validation of the organization’s security posture.
6.Address and resolve issues
Once the vulnerabilities are identified, they must be addressed during the test. Security experts collaborate with the organization to develop a plan for fixing the weaknesses. Rectifying includes updating software, changing configurations, or improving internal processes. This step prepares the system to face future threats.
Also Read: Penetration Testing Compliances In 2024 – Ultimate Guide
Benefits of Internal Penetration Testing
When internal penetration testing gives clarity to organizations on how a hacker could break into their internal systems, there are also multiple benefits. Here are a few:
1.Prevents financial and reputational loss
In an organization, a data breach can cause significant money loss and disrupt a company’s reputation. Enabling internal penetration testing helps businesses find weaknesses before a real attack occurs, preparing them for the worst-case scenario. This testing can prevent costly damage and protect the company’s security image.
2.Identifies insider threats
Most of the cyberattacks originate internally, which can be through malicious employees or accidental actions. Internal pen testing detects vulnerabilities that could be exploited by insiders.
3.Provides a fresh perspective
Testing offers an external viewpoint on existing security protocols, policies, and employee training. This new perspective helps organizations identify gaps that might not be evident from within and implement necessary improvements.
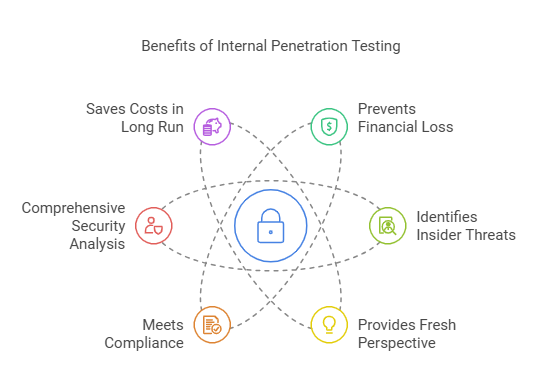
4.Meet compliance
Internal pen testing helps organizations meet regulatory and compliance standards by showing they are actively checking and improving their security. This is especially important for industries with strict rules, like healthcare, finance, or technology.
5.Comprehensive security analysis
Another benefit of internal pen testing is the rigorous analysis of every network layer, from infrastructure to applications and databases. This top-to-bottom review highlights security flaws and provides actionable insights to check on the organization’s overall defences.
6.Saves costs in the long run
Recognizing the security threats in an organization and fixing them early can save huge expenses associated with data breaches. The company can save their operations from consequences including fines, legal fees, and recovery costs. Testing also serves as an investment in the company’s long-term security.
Internal Penetration Testing FAQs
1.How can internal penetration testing help prevent insider threats or data breaches?
Internal penetration testing is an evaluation of an internal network security attack in an organization. This testing identifies security weaknesses that could be exploited by insiders, such as poor password management or inadequate access controls. Finding these issues early and fixing them before real threats can save businesses from major damage.
2.How does internal penetration testing differ from external testing, and why do I need both?
Internal pen testing drives a security analysis within the organization’s network, assuming the attacker has already bypassed perimeter defences. External testing, on the other hand, looks at vulnerabilities from outside the network, where an attacker has no inside access. Both tests are necessary because external testing protects against outside threats. However, internal testing helps in securing internal systems and preventing insider attacks.
3.What are the key benefits of conducting internal penetration tests?
Internal penetration tests help identify hidden vulnerabilities within the network. They provide insights into how a hacker could exploit these weaknesses. Additionally, they help improve security protocols, prevent costly breaches, and ensure the organization meets compliance standards