Cyber threats are evolving every day. These significantly underpin the need to address security concerns by integrating VAPT (Vulnerability Assessment and Penetration Testing) and implementing VAPT-driven solutions. The prime objective of VAPT is to protect your computers, networks, and applications from cybercriminals by detecting vulnerabilities and undertaking penetration testing.
From Malware to Phishing and from Man-in-the-Middle (MiTM) to Denial of Service (DoS), the extent to which cyber threats have evolved is truly overwhelming. Cybercriminals deploying AI-enabled tools to obtain information from a target organization in smarter and faster ways will be the last straw to tighten your security belt.
Adopting advanced threat detection tools and systems to bypass those highly sophisticated malwares and ransomwares should be strictly considered and implemented and stay ahead of emerging cyberattacks.
If more advanced threat detection techniques, such as VAPT can help tackle or contradict these so-called cyber threats, then it will be a breakthrough attempt to beat cyber thefts in 2025.
This blog sets out to identify and discuss the key cybersecurity challenges that VAPT can effectively address and mitigate in 2025 and even beyond.
Table of Contents
ToggleUnderstanding VAPT And Its Effectiveness In Addressing Cybersecurity Threats
VAPT – A Brief Overview
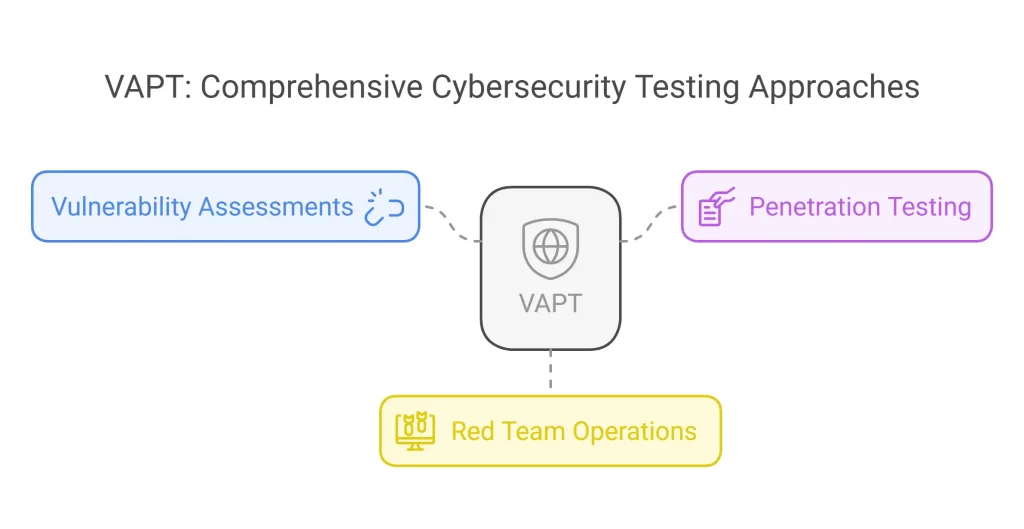
An acronym for vulnerability assessment and penetration testing, VAPT is adept at offering comprehensive security testing approaches to identify and address vulnerabilities in the security posture of an organization.
The meaning and the process behind VAPT varies from region to region, i.e., as a bracket to offer multiple distinct services. As a whole however, it covers everything from undertaking vulnerability assessments to human-aided penetration testing to also include red team operations.
The term, ‘Red Team Operations’ is nothing other than a phrase denoting cybersecurity engagement to simulate real-world cyberattacks on your system. The prime objective behind this is to assess your ability to detect and respond to inherent security threats.
Effectiveness of VAPT in Addressing Cybersecurity Threats
As a reliable threat intelligence tool, VAPT encompasses both automated and manual testing modalities and techniques. This helps organizations derive an overview of the security status of their network and systems when testing for vulnerabilities.
The effectiveness of VAPT thus lies in its abilities to aid businesses in identifying potential cybersecurity threats while also helping devise specific countermeasures to mitigate harmful vulnerabilities that can otherwise thwart business operations.
As a business, you can be rest assured that executing VAPT-oriented strategies will not only help improve your security posture, but will also enable you to achieve customer trust and ensure regulatory compliance.
Apart from the above, VAPT also serves the following purposes as these relate to identifying security gaps and addressing vulnerabilities.
Also Read: What is VAPT ?
- Improving Threat Detection And Response: By having organizations understand their vulnerabilities, VAPT can help prioritize security measures based on the extent and severity at which they present.
- Assessing Incident Response Preparedness: Concerns with evaluating a business’ effectiveness in undertaking response procedures upon simulating cyber attacks.
- Creating Security Awareness: VAPT assists you in educating your employees to take security precautions and responding to data breaches.
- Demonstrating Security Precautions: How far a business takes the necessary precautions to protect its network and systems can be well assessed through the VAPT reports.
Key Cybersecurity Threats VAPT Can Address in 2025
As per expert findings from Wattlecorp, cybersecurity threats linger despite available security measures adopted to tackle and contain them. Thanks to the popularity that penetration testing has received in recent times for efficiently determining weakness within a system. Helping eliminate security gaps by exploiting system vulnerabilities with ethical hacking is the prime objective of VAPT and the techniques that are inherent to it.
Considering the pace at which cyberattacks are rising, there has thankfully been an even simultaneous and exponential growth in penetration testing with businesses more than ever demanding for VAPT services.
With all these being stated, let’s take a look into the key cybersecurity threats that VAPT can help address and remediate in 2025.
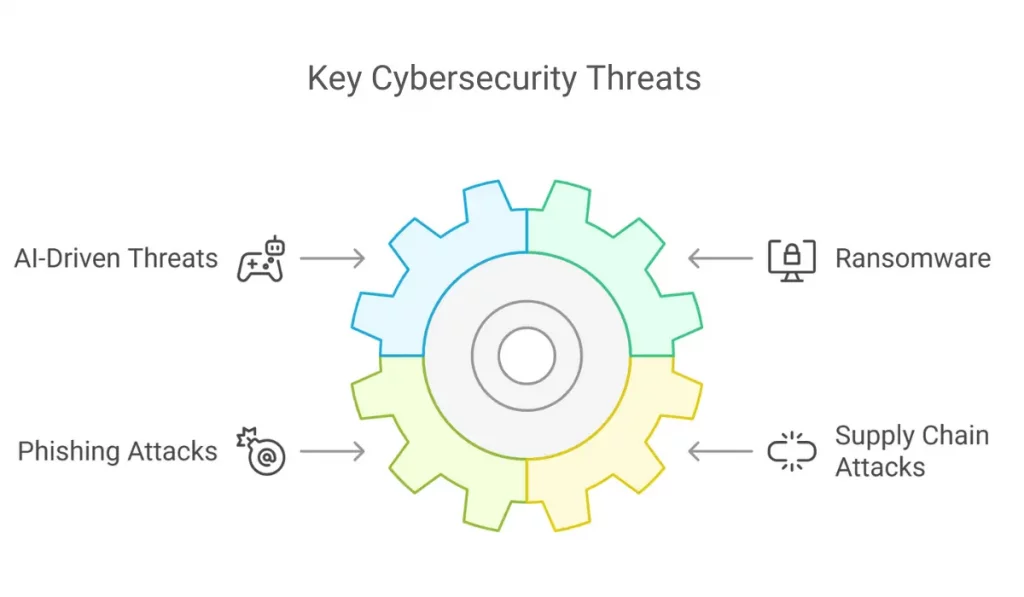
- AI-Driven Threats
If this statement can prove alarming enough, the cybercriminals have started leveraging AI-induced threats. As an organization, your ability to respond appropriately to such a massive threat in the first place is what counts.
Simultaneously, your capacity to leverage counter-AI technologies and making sure these are effective enough to tackle those challenges and threats genuinely conveys your readiness to undertake prompt security measures.
Also Read: Enterprise Cybersecurity Strategy: Best Practices in 2024
- Ransomware
With each passing year, Ransomware attacks are increasing in severity and sophistication. Demanding heavy ransom as its name suggests, these attackers encrypt data until companies pay them the desired sum.
The value of VAPT lies in its efficiency to provide visibility into the security weaknesses of your business. By bringing these expertise to your table, VAPT ultimately offers you the needed guidance to mitigate and eliminate emerging cyber threats on a real-time basis, thus keeping Ransomware out of harm’s way.
- Phishing Attacks
Among all the phishing attacks that businesses have come across so far, AI-powered phishing attacks have been identified as highly challenging. By creating personalized and realistic messages to trick people into sharing their sensitive information, these attackers cunningly steal money, install malware on devices (computers, laptops, smartphones, etc), or access systems.
Regular and effective training to employees (and even laymen) can effectively counteract the many AI-enabled phishing campaigns existing on the web.
- Supply Chain Attacks
Comprise cyberattacks that target the supply chain of an organization to compromise the latter’s system and data. With the government sectors, financial, and oil companies often falling prey to such, VAPT’s excellence to mitigate these attacks by assessing the system for existing vulnerabilities and undertaking ethical attacks can go a long way to prevent the many cyber threats lurking out there.
In the face of the above prominent cyber threats and impending cyber attacks, it would be appropriate if we as a vulnerability assessment and penetration testing team at Wattlecorp keep ourselves regularly updated on the critical cybersecurity trends for 2025. Stay tuned as we go through these in the upcoming section.
Top Cybersecurity Trends To Watch For In 2025
Corresponding to the aforementioned trends in cyber threats and attacks, here’s listed for you the top cybersecurity trends to look for in the current year and moving forward.
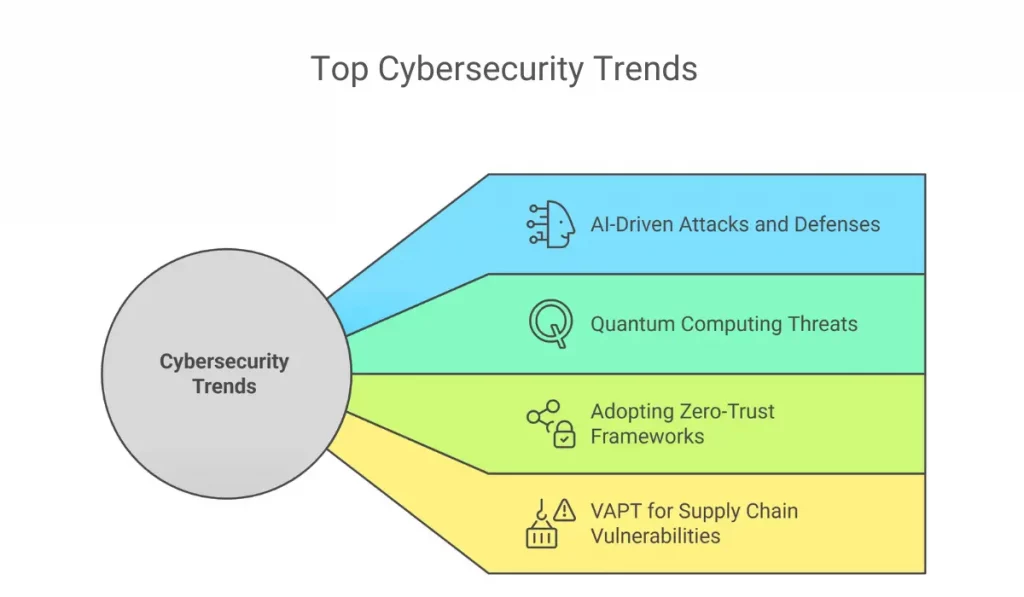
- AI-Driven Attacks and Defenses
Challenges: Among every defense strategy that cybersecurity professionals have resorted to, Artificial Intelligence or AI has always remained at the centerstage of these endeavors. For the cybercriminals, leveraging AI to initiate attacks on system vulnerabilities is no more a surprise, rather than proving highly alarming!
Also Read: 5 Common Cybersecurity Threats Found In a Penetration Test
Possible Solution: Since security teams everywhere have realized the dual nature of AI, they have started utilizing it for undertaking predictive threat intelligence, advanced anomaly detection, and incident response automation.
- Quantum Computing Threats
Challenges: Though quantum attacks can practically take years to take action, potential breaks in existing cryptographic methods and exposing sensitive data are some of the threats imposed by Quantum computing.
What can be done?: Emphasize the need to transition to quantum-safe encryption,
- Adopting Zero-Trust Frameworks To Beat Evolving Ransomware Attacks
Challenges: Evolving from the encrypt-and-demand schemes, cybercriminals have resorted to even more advanced strategies, one of them being double-extortion tactics. These enable them to steal sensitive data before encrypting the same. Companies affected by this unlawful scheme are forced to comply with ransom demands under the threat of data leaks. The launch of Ransomware-as-a-Service (RaaS) has fueled such cybercrime practices, leaving low-skilled actors with the ability to undertake sophisticated attacks.
Solution: By adopting Zero-Trust Frameworks and related strategies, such as endpoint protection and robust backup, VAPT can protect your business by mitigating emerging ransomware risks.
- VAPT For Effacing Supply Chain Vulnerabilities
What it Implies?: Supply chain vulnerabilities essentially involve globalization of supply chains. Since these tend to amplify cybersecurity risks, they conveniently open the doors for third-party software breaches. These happen like cascades through the interconnected systems and cause widespread disruptions to supply chain services.
Proactive Measures To Be Taken: Consider enforcing SBOM (Software Bill of Materials) and implementing rigorous SCRM (Supply Chain Risk Management) for enhancing and promoting security and transparency.
Benefits of VAPT
The benefits that undertaking vulnerability assessment and penetration testing can bring to a business can go a long way to adopting effective secular measures. To stay away from potential cyber threats in 2025 and years following, let’s conduct a quick review of the below-mentioned benefits of integrating VAPT for your business before winding up.

- Ensures businesses stay adherent to data protection and regulations, such as GDPR, HIPAA, SOC2, etc., thus strengthening compliance standards.
- Helps undertake risk assessment for businesses by helping the latter identify potential vulnerabilities that can significantly compromise their security by ensuing threats.
- By avoiding potential disruptions brought on by cyberattacks, VAPT can help ensure smooth operations, thereby promoting business continuity.
- Reduced Time To Market (TTM) to help accelerate your development or production processes as a business, thanks to the effectiveness of VAPT in identifying and fixing vulnerabilities on an early note.
- Financial losses can be duly prevented by VAPT through fixing vulnerabilities before these can be exploited.
Also Read: What is Vulnerability Assessment?
Vulnerability assessment and penetration testing (VAPT) is crucial to every business entity as far as protecting critical digital assets are concerned.
The role of VAPT in securing businesses across industries is prominent enough, for the former helping derive extensive and noncompromised protection from potential and emerging cyber threats and risks in 2025.
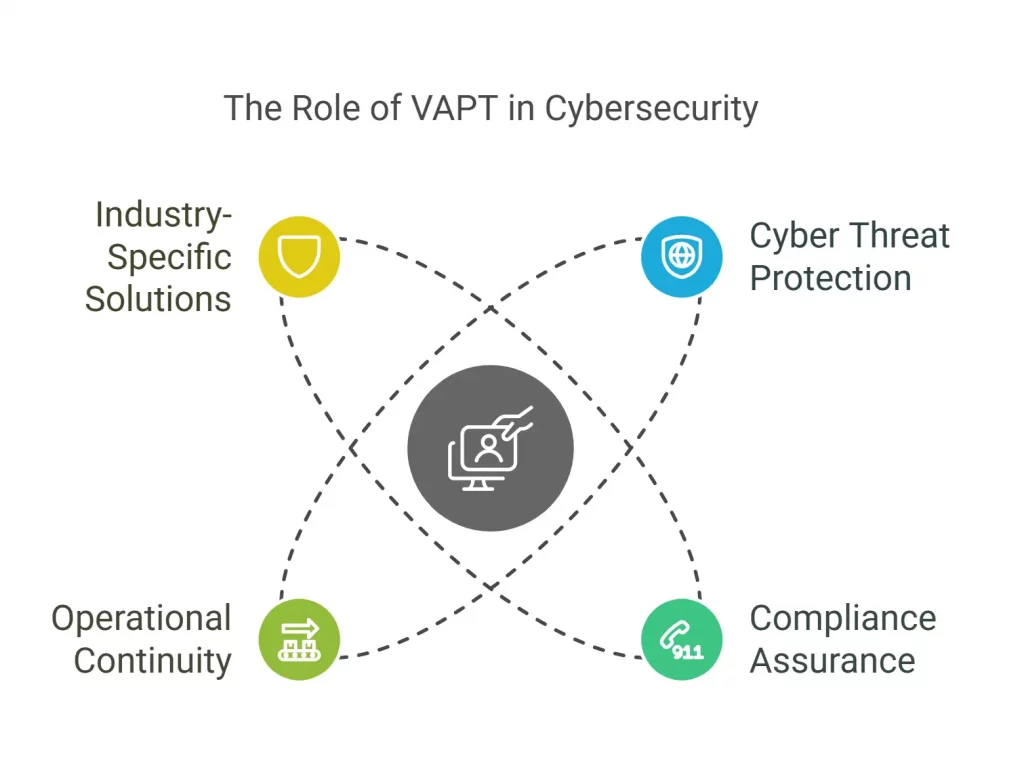
From assisting businesses in ensuring compliance to data protection and regulation standards to facilitating smooth supply chain operations, VAPT helps make sure business operations run uninterruptedly and ethically.
If the security posture of your business is what concerns you as a CTO or CEO and you are wondering about whom to consult regarding quality VAPT procedures, then Wattlecorp Cybersecurity Labs is the one for you. Equipped with cybersecurity professionals proficient in providing industry-specific VAPT solutions for cyber threats, we have gained considerable trust from our customers and clients worldwide.
So, why wait? Call us to schedule an appointment and our team will contact you in no time to secure your business and your users.
Key Cybersecurity Threats FAQs
1. What are the most effective VAPT solutions for cyber threats?
VAPT being a comprehensive process chiefly concerns with identifying and fixing vulnerabilities in your system. In line with this statement, the most effective VAPT solutions for cyber threats, both existing and evolving, include undertaking robust cybersecurity measures. These will involve exploiting detected vulnerabilities in your systems, network, and applications. You need to also leverage effective VAPT tools that will help you obtain accuracy, profound scanning service, scalability, and excellent compliance support for your business.
2. How to undertake Cyber threat assessment with VAPT?
To undertake an extensive cyber threat assessment, you need to consider the following steps:
• Defining the scope to determine what you need to test and outline the goals for the assessment.
• Identifying vulnerabilities by utilizing automated or manual scans to detect known weaknesses in your systems, network,
and applications.
• Exploiting vulnerabilities by simulating real-world cyberattacks.
• Document results to accurately report the vulnerabilities you found. This will also include assessing their impact and
providing appropriate recommendations to fix the same.
• Addressing vulnerabilities to fix them accompanied by retesting the system to confirm fixation.
• Continuous monitoring and documenting the results for any new threats or security incidents.
3. What are the 3 best VAPT strategies for evolving cyber threats?
Based on authentic sources, the three best VAPT strategies or programs to tackle evolving cyber threats include:
• Defining the scope and objectives of VAPT analysis to identify critical assets and systems that are to be tested.
• Planning and developing an appropriate testing schedule to undertake regular assessments – bi-annually, quarterly,
etc. Planning will also involve conducting continuous testing for checking for vulnerabilities in critical systems.
• Employing reliable and appropriate methodologies plus developing in-house teams, also considering external specialists.
Ensure that the concerned personnel are having relevant certifications.







