Securing your network systems is important to protect your sensitive data and keep your environment safe from data breaches. This builds trust with your clients and highlights the need for regular Network Security Testing. The world of the Internet laden with cyber threats makes network security testing critical to secure our systems and network from innumerable hackers out there.
Understanding the seriousness of the need to undertake regular network security checks to identify and address security vulnerabilities, this blog intends to explore the fundamental aspects of network security testing. While these include exploring the types, tools, and techniques involved, it is hopeful that it will provide valuable insights on effectively securing your network and everything associated there.
While you are here, it would also be worth learning how we at Wattlecorp as a cybersecurity service provider tackle emerging cyber threats.
Table of Contents
ToggleUnderstanding Network Security Testing
- Network Security Testing Explained?
‘Network Security Testing’ refers to the act of finding security vulnerabilities or loopholes across a network. It helps protect network data and every other devices and applications from potential online threats by conducting regular security checks to strengthen an organization’s security posture.
Network security testing is bound by policies as measures to prevent unauthorized access to the devices on a network. It critically underpins the need to monitor any misuse, modification, or suspicious activity on a network, appropriately responding to the same by engaging in specific network security monitoring techniques, such as SIM (Security Information Monitoring) and SEM (Security Event Monitoring)
- Importance of undertaking Network Security Checks?
As mentioned earlier, network security checks are pivotal to identifying any security loops that may put your devices (and the network that it comes under) at any risk of cyber attacks. When you undertake security tests for your network on a regular basis, you prove your willingness to stay compliant with industry-specific laws and regulations related to security requirements.
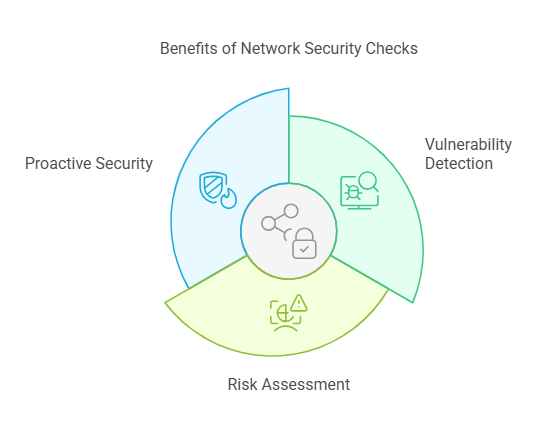
Additionally, network security testing helps you plan and implement counter measures to identify and address potential cyber threats and keep them out of your league. Next comes the benefits which you can avail when undertaking regular network security analysis. As such, these include:
Also Read: Black Box Penetration Testing Services In Saudi Arabia
- Vulnerability Detection: Scans network to identify vulnerabilities to enable timely remediation.
- Risk Assessment: Allows you to undertake risk assessment for potential impact upon vulnerability detection.
- Proactive Security: Enables you to address identified security issues and devise remediation measures before being exploited by real-world hackers.
Network Security Testing – Analyzing Key Types, Tools, and Techniques
1. Types of network security tests
Typically speaking, network security testing comprises the following:
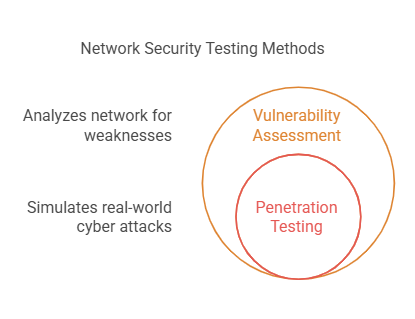
- Penetration Testing: One of the most proactive segments of network security testing, penetration testing aka pen testing involves mimicking real-world cybercrime to check for vulnerabilities in a security system. Penetration testing thus helps determine the possibilities of real cyber attacks.
- Vulnerability Assessment: Pertains to analysing or examining the network architecture to look for any weaknesses. Robotic tools are made use of to identify common security vulnerabilities to help prevent security incidents.
Note that both vulnerability assessments and penetration testing are complementary to each other when conducting network security testing.
2. Tools For Network Safety Analysis
There exist specific tools for safely and effectively executing network safety checks. These include:
- Nmap: Known to be an open-source tool, Nmap helps scan networks for available hosts, operating systems, and services, thus helping identify both harmless and malicious servers.
- Responder:A tool that listens to your requests for obtaining credentials when assessing a computer network.
- Wireshark: Similar to Nmap, Wireshark is an open-source tool meant to analyze network traffic and protocols to detect vulnerabilities.
- Burp Suite: Even though Burp Suite is widely utilised for Web Application Security Testing, it allows penetration testers to identify vulnerabilities in web applications through a combination of manual and automated methods. Burp Suite in this maneuver, serves as a key component in network security testing.
- Metasploit: The most effective tool in the realm of network security testing, for it helps identify security weaknesses in web applications, servers, and networks.
Additional tools to help conduct network security analysis also include automated scanning tools, such as Qualys, OpenVAS, and Nessus. These help undertake quick security checks for network vulnerabilities.
There also exist specific penetration testing frameworks, say OWASP Zap, which can be used to thoroughly check security weaknesses in an organized manner. In this regard, OWASP Zap stands similar to Metasploit as specified above.

3. Network Security Testing Methodologies and Techniques
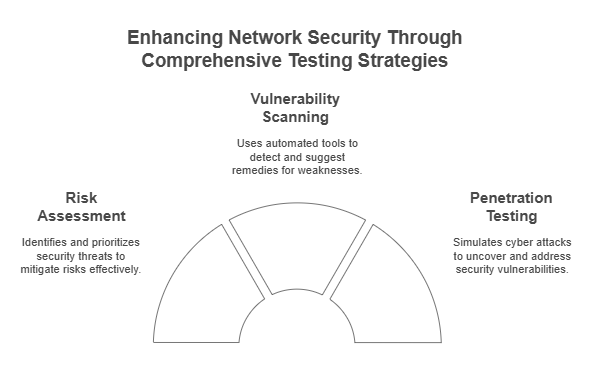
Based on current trends in the cybersecurity assessment arena, the three major techniques to assist in network security checks are Risk Assessment, Penetration Testing, and Vulnerability Scanning.
- Risk Assessment As A Network Security Testing Tool
Uses: Risk assessment fundamentally serves to identify and prioritize security threats in an organization. Usually, it is the IT and critical digital assets, including customer data, accounts, and other sensitive information that are more subject to risk assessment. Results from vulnerability analysis and penetration, as well as other forms of security analysis are usually considered to perform risk assessment.
Benefits: Helps organizations mitigate security risks and devise proper countermeasures to tackle and prevent cyber threats and attacks.
- Vulnerability Scanning To Proactively Nullify Cyber Threats And Attacks
Uses: Mostly employs automated programs to carry out security vulnerability assessments. These tools automatically scan systems to identify weaknesses in there.
Benefits: Automated programs for vulnerability scanning help businesses identify misconfigured file servers, security updates which are outdated, and common security holes. Vulnerability scanning (through automated programs) is also useful in detecting innumerable vulnerabilities with appropriate remedies to fix them.
- Penetration Testing For Security Vulnerability Analysis
Uses: Acts like cybercrime in the real world to deeply assess the network system of an organization.
Benefits: Thorough penetration testing helps reveal security vulnerabilities to proactively tackle any impending cyber attacks.
In addition to the above techniques discussed here, Ethical Hacking has also emerged to be an effective network security testing technique to minimize vulnerabilities and evade any form or degree of cyber threats by black hat hackers out there.
In a nutshell, network security testing serves to effectively strengthen the security posture of your business by appropriately applying different methods, tools, and techniques explained above. Businesses both small and big are bound to undergo mandatory network security analysis to ensure the same is updated enough to keep potentially malicious intruders and hackers out of reach.
Regular security assessments by way of vulnerability analysis and penetration testing are considered to be effective proactive measures to prevent cyber threats given the rising incidents of cyberattacks.
Also Read: What Is Security Awareness Training? & Why Is It Important?
Wattlecorp Cybersecurity Labs LLP being a leading cybersecurity service provider has been reputed to offer state-of-the-art network service testing online to its clients regionally, nationally, and internationally, With its service centers located in India (Kerala and Bangalore), UAE (Saudi Arabia), and USA, it proudly possesses a remarkable team of cybersecurity professionals, who work day in and out to tackle any network security-related issues for its clients.
Through our experienced and qualified VAPT team, we could once again prove that Network Security Analysis indeed requires a professional handling.
By involving safe and effective Network Security Testing processes, Wattlecorp has built a considerable degree of trust among its clients and customers worldwide, most of which are Fortune 500 companies, such as Bentley, Walmart, and Mercedes Benz.
If your network safety is what concerns you the most regardless of the industry you are in, do book an appointment with us, and our staff will get in touch with you shortly regarding the necessary formalities and procedures for securing you and your systems.
Frequently Asked Questions
1 .What are the different types of network security testing?
Network security testing typically comprises vulnerability scanning and penetration testing as its two major types or components. These are meant to assess the security measures of an organization to look for any loopholes by conducting real-world cyber attacks. The prime intent is to strongly secure the network and computers from any untoward phishing attempts or malicious intrusion.
2 .What are common network vulnerabilities?
Common network vulnerabilities have been known to include weaknesses found within the hardware and software of a network, outdated network security policies, and problems with administration. Time elapsed in identifying these anomalies is enough to invite exploitation from hackers or cyber thefts.
3. How often should network security testing be conducted?
Experts recommend regularly undergoing network security testing to prevent cyberattacks. Businesses undertaking regular security testing by way of vulnerability scanning and penetration have been witnessed to be effectively wading off cyber threats, thus proactively protecting their network and computers.








