Modern software applications undergo a series of threats besides the numerous possibilities they offer. It is wise to be updated on the latest security vulnerabilities and recent exploits. Setting up benchmarks on these threats is important to ensure the application is secure before an attack occurs.
The Open Web Application Security Project is a secure nonprofit foundation publishing software security analyses. They are popular for their annual reports of the top software vulnerabilities. Since 2019, they have also released API security vulnerabilities.
Since the role of APIs has been profound in our everyday lives, these touchpoints have been highly vulnerable to attacks. In this blog, let’s delve deeper into the latest OWASP Top 10 API vulnerabilities and the actions API providers can adopt to address every mentioned concern.
Table of Contents
Toggle- What is OWASP?
- What is API Security?
- What are the OWASP API Security Top 10 Risks?
- API1:2023 -Broken Object Level Authorization (BOLA)
- API2:2023 -Broken Authentication
- API3:2023 -Broken Object Property Level Authorisation
- API4:2023 -Unrestricted Resource Consumption
- API5:2023 -Broken Function Level Authorization (BFLA)
- API6:2023 -Unrestricted Access to Sensitive Business Flows
- API7:2023 -Server-Side Request Forgery (SSRF)
- API8:2023 -Security Misconfiguration
- API9:2023 -Improper Inventory Management
- API10:2023 -Unsafe Consumption of APIs
- How to Mitigate API Security Vulnerabilities?
What is OWASP?
Open Web Application Security Project, (OWASP) is an online open community, i.e., a non-profit foundation that emphasizes software security.
The guiding principle of OWASP is that all their resources should be freely accessible and easy to find across the website, which enables people to improve the security of the applications they build.
These offer tools, forums, videos, and documentation,n among other things. OWASP Top 10 offers a report that outlines the security concerns of web application security. OWASP API Top 10 portrays the most common API security risks which we shall discuss further in the blog in detail.
What is API Security?
API is the driving force of innovation in the existing app-driven business sphere. From financial institutions, retail, and transportation to the Internet of Things (IoT), smart vehicles, and autonomous systems, APIs play a major role in powering mobile, SaaS, and web applications. APIs are prevalent in customer-facing, partner-facing, and internal applications.

Generally, APIs expose sensitive information and application logic like Personally Identifiable Information (PII) , and due to this, they have become a target to attackers. Rapid innovation would be a hurdle in the absence of secure APIs.
API security works on strategies and solutions to recognize and eliminate precise vulnerabilities and security risks of employing Application Programming Interfaces (APIs).
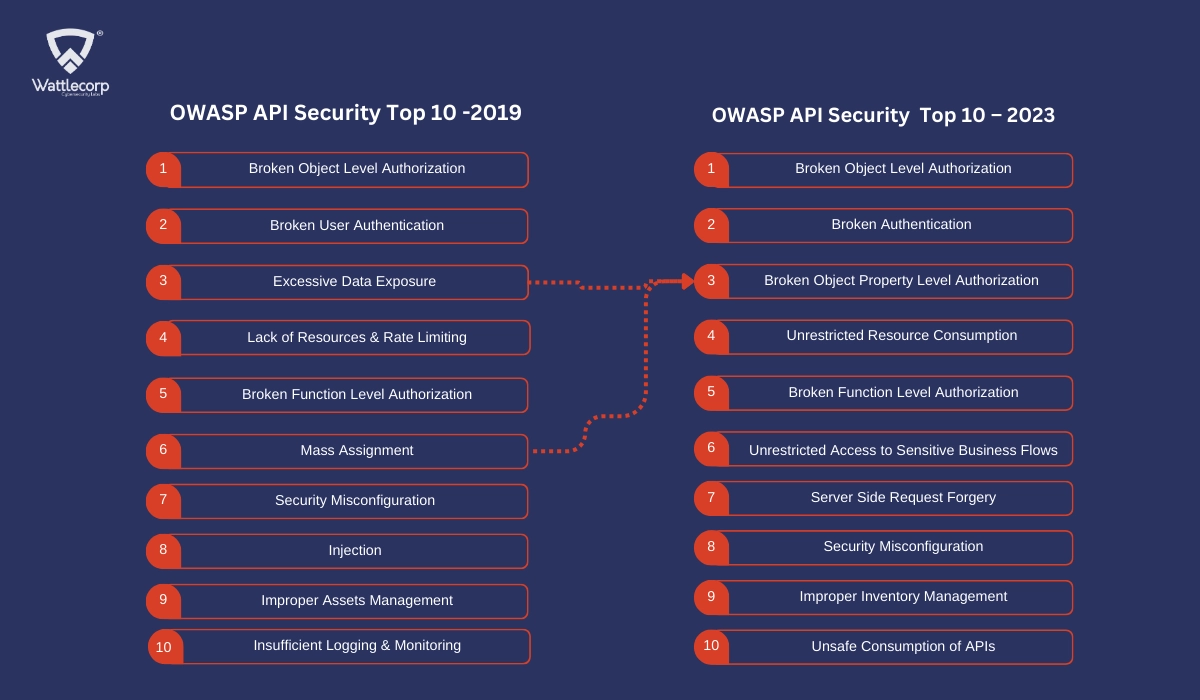
What are the OWASP API Security Top 10 Risks?
The cost of API security breaches travels beyond the financial costs concerning legal disputes, lost customers, and fines. The destruction of reputation and broken trust with the user base can affect long-lasting measures that could take many years to resolve.
To ensure that this doesn’t happen to you, let’s understand the list of OWASP API Security TOP 10 vulnerabilities
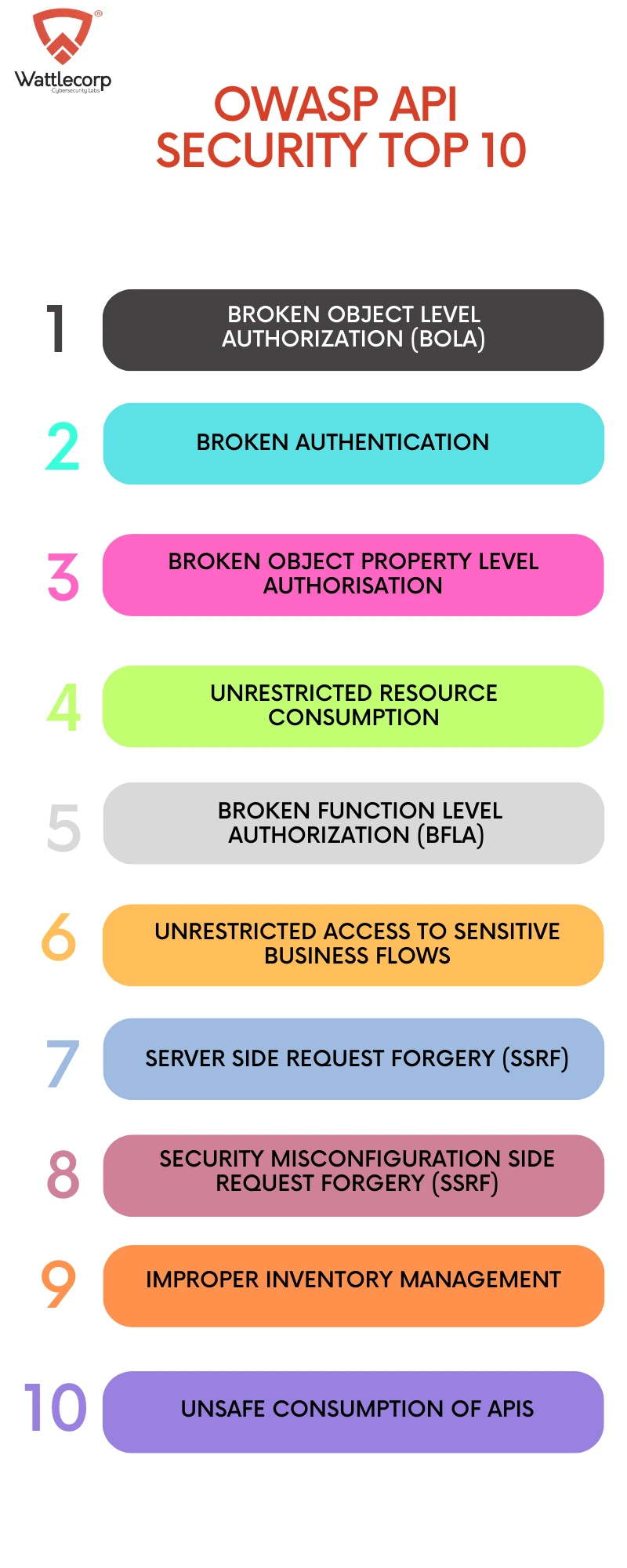
- API1:2023 – Broken Object Level Authorization (BOLA)
- API2:2023 – Broken Authentication
- API3:2023 –Broken Object Property Level Authorisation
- API4:2023 –Unrestricted Resource Consumption
- API5:2023 –Broken Function Level Authorization (BFLA)
- API6:2023 -Unrestricted Access to Sensitive Business Flows
- API7:2023– Server-Side Request Forgery (SSRF)
- API8:2023 -Security Misconfiguration
- API9:2023 –Improper Inventory Management
- API10:2023 –Unsafe Consumption of APIs
Read further to get a detailed insight into OWASP API’s Top 10 vulnerabilities:
API1:2023 -Broken Object Level Authorization (BOLA)
Broken Object Level Authorization (BOLA), emerges due to the inadequate access controls across API endpoints. This enables unauthorized users to access and modify highly sensitive information.
BOLA is earmarked as the most common security threat with its presence in almost 40% of all recorded API attacks. BOLA API vulnerabilities have always been in the first position on the OWASP list since 2019 and hit the same top spot in the OWASP API Top 10 this time.
API2:2023 -Broken Authentication
Broken authentication gives attackers the privilege to use authentication tokens, brute force attacks, and credential stuffing to exercise unauthorized access to the applications. This API authentication takes the number two position in the OWASP API Top 10 list from 2019.
API3:2023 -Broken Object Property Level Authorisation
This is defined as a possible set of attacks that occurs when unauthorized access to sensitive object properties causes data disclosure, corruption, or data loss. It merges the attacks that occur due to Excessive Data Exposure (API reveals more data or fields than what the client expects through API response) and Mass Assignment (when an active record pattern in web apps is prone to modifying data items that users are not usually allowed to access like passwords, permissions, etc). Both these methods stated above rely on API endpoint manipulation to win access to sensitive information.
API4:2023 -Unrestricted Resource Consumption
This vulnerability happens in APIs that improperly handle or neglect to maintain limits for resource consumption, making them largely vulnerable to brute-force attacks. Unrestricted resource consumption took rank #4, replacing ‘Lack of Resources and Rate Limiting’ in the 2019 report. But, though the name has been changed, the vulnerability is no different.
API5:2023 -Broken Function Level Authorization (BFLA)
This threat occurs when authorization is not implemented properly, causing unauthorized users to be capable of executing API functions like addition, updation, or deletion of customer records, user roles, etc. BFLA has been ranked #5 on the list since 2019.
Also Read: OWASP Top 10 Vulnerabilities
API6:2023 -Unrestricted Access to Sensitive Business Flows
When an API gives access to major tasks without taking adequate security measures, unrestricted access to sensitive business flows arises. Attackers can take advantage of this vulnerability by creating malicious payloads, like blind cross-site scripting (XSS) in the API. They can leverage these payloads to achieve unauthorized access to downstream systems. It also helps to reveal other weaknesses in the connected infrastructure.
API7:2023 -Server-Side Request Forgery (SSRF)
Server Side Request Forgery (SSRF) occurs when a user-controlled URL is passed over API, and processed using a backend server. When the backend server makes an effort to connect to the user-fed URL, it paves the way for SSRF and leads to API security risks.
API8:2023 -Security Misconfiguration
API security misconfigurations can occur when security features and settings are configured improperly or removed unintentionally. Such misconfigurations can leave APIs vulnerable to several attacks, which compromise the confidentiality, availability, and integrity of sensitive information. This can also be a result of ad-hoc or incomplete configurations, open cloud storage, unnecessary HTTP methods, misconfigured HTTP headers, verbose error messages, Cross-Origin resource sharing, etc.
Also Read: OWASP Mobile Top 10 Vulnerabilities
API9:2023 -Improper Inventory Management
Threat is a result of an incomplete or outdated inventory which builds unknown gaps in the API attack surface and makes it hard to detect the older API versions that demand decommissioning. By exploiting improper inventory management, attackers can earn unauthorized access to sensitive information, or gain complete server access through unpatched, old, or vulnerable API versions.
API10:2023 -Unsafe Consumption of APIs
Data exposure and unauthorized access can be a major concern caused by API clients’ inadequate use of APIs, say, bypassing API authentication security controls or manipulating API responses. API data consumption itself or through abusing third-party integration issues results in this API vulnerability. It causes attackers to exploit the weaknesses and gain access to sensitive data or app functionality.
How to Mitigate API Security Vulnerabilities?
API attacks pose a serious risk that can end up in huge financial losses. To stay ahead of hackers, it is essential to have a reliable security system in place that can detect and block malicious requests.
It is also necessary to adhere to the latest API security best practices if you wish to publicly share your APIs (using authentication, authorization, traffic encryption, rate limit, etc.).

You should also test API regularly against the API vulnerability list to resolve them before they get exploited.
Here are some key points you can use to strengthen API security:
- Use strong authentication and authorization mechanisms to make sure that only authorized users or applications gain your API access.
- Use HTTPS to enable data encryption in transit and make sure that the sensitive data is encrypted at rest to avoid unauthorized access or eavesdropping.
- Validate and analyze the input data to secure against injection attacks like SQL injection and cross-site scripting.
- Implement rate limiting and throttling to avoid abuse and DoS (Denial of Service) attacks by limiting the requests a client makes to your API in a specific timeframe.
- Conduct regular security audits & penetration testing to understand and fix API vulnerabilities.
- Use API gateways to monitor, safeguard, and manage API traffic. Gateways help enforce security policies, manage rate limiting, and offer analytics and logging.
- Ensure that every component of the API stack including dependencies and libraries is updated regularly to secure against identified vulnerabilities.
Why Should You Understand OWASP API Security Top 10?
APIs connect modern-day applications, scale up business innovation, and let companies meet the increasing expectations of customers to boost speed and digitalization. However, by being an invaluable asset to organizations, APIs have also become a key target for attackers.
Understanding the core issues that threaten your APIs means you will be highly equipped to develop a robust and reliable API security strategy in place. If you would like to implement the best API security strategies for your business, let’s talk today!
OWASP Top 10 is a form of awareness document that helps developers know about software security risks and mitigate vulnerabilities. OWASP API Top 10 is a specific category of project by OWASP in which developers and security experts can understand and eliminate the potential risks of insecure APIs.
You can get the latest updates on the OWASP API Top 10 list from our blog, making it easy to stay subscribed. Also, you may bookmark the page of the OWASP website to learn about the updates or changes.
No. The OWASP API Top 10 is not static. The project is susceptible to revisions and reflects the emerging threat landscape and the top API security practices. New vulnerabilities arise and the importance of the existing ones could be changed. OWASP replaces them and updates the Top 10 to focus on the most serious API security risks.