As with every technology, the more it is popular, the greater the chances of being found with vulnerabilities and attacked by bad actors. OWASP Mobile Top 10 is an extensive resource that helps security researchers and mobile application developers alike with relevant security data. It contains comprehensive data that helps to detect, assess, and address threats affecting mobile applications based on their degree of risk.
Mobile devices and its related technologies are growing at an exponential rate. All it ever took was a few decades to have such an immense transition from landlines to tiny gadgets with versatile features. Its popularity is primarily due to its easy access and integration of various applications such as communication, entertainment, finance, and healthcare.
Table of Contents
Toggle- What is OWASP Mobile Top 10
- The OWASP Top 10 Mobile Risks
- M1: Improper Credential Usage
- M2: Inadequate Supply Chain Security
- M3: Insecure Authentication/Authorization
- M4: Insufficient Input/Output Validation
- M5: Insecure Communication
- M6: Inadequate Privacy Controls
- M7: Insufficient Binary Protections
- M8: Security Misconfiguration
- M9: Insecure Data Storage
- M10: Insufficient Cryptography
- Why Securing Mobile Apps Matters
- Impact of Security Risks on Mobile Applications
- Steps to securing your mobile apps way ahead
What is OWASP Mobile Top 10
OWASP, also known as the Open Web Application Security Project, is a collaborative and open-source organization dedicated to enhancing the security of applications. The OWASP mobile top 10 list is simply the compilation of ten vulnerabilities that infected the mobile application, listed based on the number of times it is reported. The data is provided by various contributing agencies across the world, which are companies related to the same.

The OWASP Mobile Top 10 is a list of the biggest security risks that mobile apps face. It’s published by the Open Web Application Security Project, a non-profit company with a mission of developing software security standards. Security experts, researchers, and developers across the globe contribute to this list.
Updated regularly to stay ahead of threats. Anyone who works on creating or securing mobile apps should have this resource. By understanding what’s listed in this top 10, developers can take steps to prevent them. Making their application safe and secure.
OWASP goes above and beyond with two extra resources. The first is the OWASP Mobile Application Security Verification Standard (MASVS), which lists security requirements for mobile applications. Following that is the OWASP Mobile Application Security Testing Guide (MASTG) which is a guide to test how secure your application is.
Combined these three resources provide a complete set of guidelines to make mobile applications extremely secure. To make sure no one loses their mind going through the process, just start by following these recommendations in the OWASP Mobile Top 10, developers will be able to help.
The OWASP Top 10 Mobile Risks
The OWASP Mobile Top 10 provides the most common mobile app security risks in effect. Similar to every other list by OWASP, the mobile risks also follow the hierarchy based on the occurrence of the particular vulnerability. Following is the latest update from OWASP aka “Top 10 Mobile Risks – Initial Release 2023”.
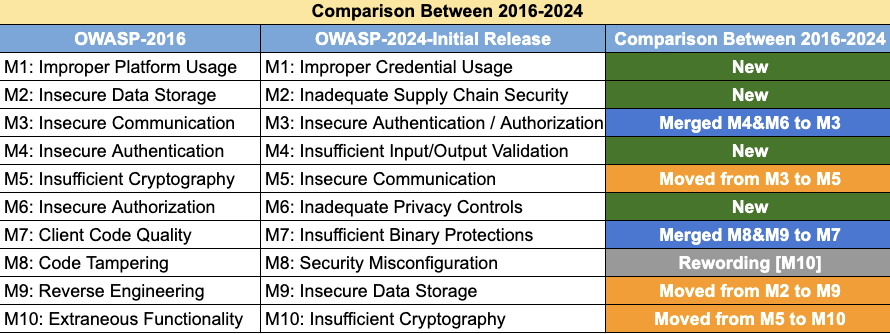
M1: Improper Credential Usage
It is a vulnerability that allows misuse of credentials including the hardcoding of credentials, plain text storage of credentials, or failure to validate the credentials properly. This can lead to a security breach, loss of user privacy, and unauthorized access to your sensitive data and systems.
M2: Inadequate Supply Chain Security
If the components used to build a mobile app aren’t properly checked for security flaws, it opens the door for attackers to inject malicious code into it.
M3: Insecure Authentication/Authorization
Without precautions that verify who is using an application or restrict their access to certain data, it makes it easier for someone unauthorized to sneak in. Once they’re in they have free reign over all accounts and data.
M4: Insufficient Input/Output Validation
Applications must double-check user input before processing. Failing to validate user input gives attackers the ability to slip in code meant to harm other users or manipulate data.
M5: Insecure Communication
Apps that transfer sensitive information over unencrypted channels or use weak encryptions are waiting for their messages to be intercepted by anyone along their route. Normally, an adversary listening on the communication channel can intercept and change data delivered in plaintext or using an obsolete encryption scheme as it travels via the internet and the carrier network of the mobile device. Their intentions might vary and include stealing a person’s identity, espionage, unauthorized access to sensitive information, etc.
M6: Inadequate Privacy Controls
This potential risk arises when developers fail to implement strong systems to protect user data privacy, leading to a variety of privacy breaches. Inadequate security measures in mobile applications pose major dangers to user data, potentially disclosing sensitive information and compromising trust among users.
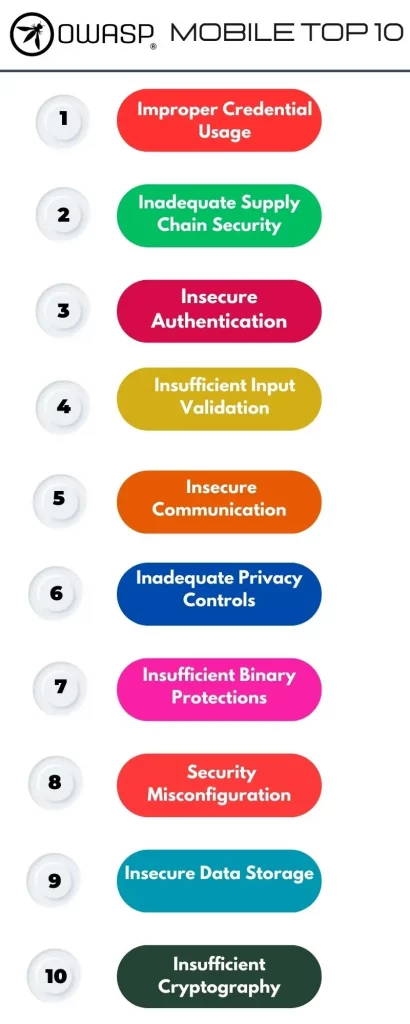
M7: Insufficient Binary Protections
Since software binaries are usually available from app stores or duplicated from mobile devices, binary attacks are easy to set up. The binaries might include important information, such as private API keys or encoded cryptographic secrets, which an attacker could exploit.
Reconfiguring the payment IDs in an application, repacking it, and distributing it through app stores is a classic form of attack. The attacker then obtains money instead from the legitimate developer when users download this unauthorized copy from the app store.
M8: Security Misconfiguration
It refers to wrongly set security configurations, permissions, and controls, which are vulnerable and susceptible to unauthorized access. Attackers who could take advantage of security flaws are able to utilize sensitive data to perform malicious actions.
M9: Insecure Data Storage
Insecure data storage on a mobile application opens its doors to incidents ranging from direct data extraction to sensitive data leakage. The main reason for this vulnerability is the storage of privileged data in plain text format in insecure file locations.
M10: Insufficient Cryptography
An attacker can use such vulnerabilities to bypass encryption, execute cryptographic attacks, modify data, or get unauthorized access to sensitive data. It exposes security flaws that may compromise the efficiency of cryptographic security measures and compromise the confidentiality and integrity of the data within. It includes the use of insecure encryption algorithms or insufficient key lengths, poor key management practices, improper encryption key handling, insecure random number generation, flawed cryptographic protocol implementation, or weaknesses in cryptographic libraries.
Also Read : OWASP Top 10
Why Securing Mobile Apps Matters
Hope you have a clear idea about OWASP Mobile top 10, so Mobile app security is a necessity, never an extra. Mobile applications should be designed to manage sensitive data regularly; it could be your banking credentials, health records, or even your social insurance number. A lapse in the security of these apps could lead your data to land in the wrong hands and wreak havoc with unprecedented implications.
But there’s more than just worrying about your data; it’s your privacy too. An application can’t just sever its ties after handling our sensitive data recklessly. That trust which progressively disappeared won’t spring back to life overnight; it needs work. The procedure of securing your mobile application is beneficial double-fold; you are protecting your vested interests and your user base. Also, remember that fortifying your app only works to add to your favorable position in the market competition.
Impact of Security Risks on Mobile Applications
As with any vulnerabilities, those infecting mobile applications also have a huge impact on the organization and user horizons. From a business perspective, it includes reputational damages, identity fraud, data breaches, and disruptions of business operations.
For an attacker, all it ever wants is merely a single-minute vulnerability with which they elevate it to higher levels, leading to catastrophes. For a user, it is the loss of the data that they shared with your business and ended up in malicious hands. This ends up in a loss of trust in the business collectively leading to financial loss due to profit decline and expenses to remediate the incident.
Also, many of the countries and regions have strict information security-related policies and laws. While doing business in these regions, it is by default expected to ensure resilience. Along with other losses, a breach also causes regulatory fines, which costs nothing less than a huge amount of money.
Steps to securing your mobile apps way ahead
Secure mobile applications are something every user expects in the cyber-vigilant era of the technological landscape. And the need for effective mobile app penetration testing, you need a greater partner in security which is capable of providing you nothing less than the best. Wattlecorp always follows the OWASP Mobile top10 vulnerabilities in each respective year and helps you to experience how the expertise helps your application to ensure cyber resilience with our team of seasoned security professionals.







