SECURE YOUR BUSINESS WITH EXPERT VAPT STRATEGIES
How Secure Is Your Infrastructure? Book a Free Consultation with Wattlecorp’s Experts to identify vulnerabilities, develop a robust VAPT strategy, and safeguard your business with tailored protection solutions.

Penetration testing trends are evolving daily with the exponential change in the threat landscape and the rapid technological evolution. The primary reason for this is the wider susceptibility of digital and physical assets to most organizations globally.
As technology and digital information get more integrated into daily operations, organizations become more vulnerable to cyberattacks. The need to protect applications is driving penetration testing’s value for all. Most tech companies and financial services firms rely on pen-testing to find application vulnerabilities, due to which penetration testing market trends are evolving substantially.
Table of Contents
ToggleWhat is penetration testing?
Pen testing is a tactic employed by ethical hackers to conduct planned attacks upon the security of an organization’s architecture to find weaknesses in the system. Pen testing is a portion of the all-encompassing application security plan. It is a security exercise used by a cyber-security professional to find and exploit vulnerabilities in a computer system.

This attack simulation aims to identify any security holes in a system that might be used by an attacker. Once ample permissions from the organization are obtained, pen tests begin with a reconnaissance phase, in which an ethical hacker invests effort in obtaining knowledge and data to help them organize their attack.
Once ample data is collected, the next step is to attempt to infiltrate the application infrastructure, and then maintain access, using precise tools tailored for each case scenario. The procedure that the pentester went through is recorded along with screenshots to share with the decision makers or the technical team of the organization as the final step.
Top 10 penetration testing trends In 2024
We have listed the top penetration testing trends
- Automated penetration testing
- Artificial Intelligence
- Adaptive penetration testing
- Continuous penetration testing
- Cloud security pen-testing
- IoT security testing
- GRC, SIEM, and help desk system integrations
- DevSecOps
- Advanced Persistent Threat (APT) Simulation Testing
- Data security compliance
1. Automated penetration testing
It has emerged as a revolutionary penetration testing trend, which optimizes how security assessments are performed in an organization. The repetitive tasks such as vulnerability scanning and configuration reviews are automated in this approach, which helps deliver faster results.
The automated penetration testing approach is more faster and scalable. However, its coverage is still not up to par due to the higher need for technological advancements and research in this field.
2. Artificial Intelligence
As a step ahead of automated penetration testing, the integration of AI in penetration testing helps enhance penetration testing. It differentiates from the automated approach with its capability to adapt and learn from past tests conducted towards getting updated into a more fine-tuned testing engine.

Recent technological advancements in AI are indeed a greater opportunity for effective penetration testing, but it indeed comes with challenges. It helps to find results much faster and more accurately. And it is most required to be updated from recent hacker tactics.
3. Adaptive penetration testing
It is one of the penetration testing trends that helps to mimic the bad actor more realistically, and it is more inclined toward understanding the organization’s unique risks and threats.
It is a method that provides a much more comprehensive and efficient approach to identifying the vulnerabilities in a system as compared to primitive tactics. Also, this provides more adaptability and flexibility to the pen-testers towards adjusting their strategies and technologies based on the data collected from the reconnaissance phase of penetration testing.
4. Continuous penetration testing
This is another most recent penetration testing trend, in which organizations conduct regular tests on their systems and applications. It is indeed a proactive approach to security resilience.
This helps to stay ahead of the latest known vulnerabilities. Contrary to the traditional approach which is conducted annually or bi-annually, continuous penetration testing is conducted more often on a monthly or quarterly basis. This helps to stay ahead in the rapidly evolving threat landscape for businesses.
5. Cloud security pen-testing
Through cloud penetration testing, businesses can protect themselves from system breaches, improve the security of their cloud environments, and adhere to industry requirements. A lot of businesses are moving to the cloud to boost efficiency and promote teamwork.

Nevertheless, the majority of cloud services do not currently provide businesses with safe authentication or encryption. Firms must implement cloud-based application security testing to protect all endpoints through proactive vulnerability detection and mitigation. They will thus need penetration testing to guarantee the security within their cloud.
6. IoT security testing
IoT security assessments are used to find security flaws in hardware, software, services, WiFi and Bluetooth connectivity, and other device components.

The devices undergo testing to identify security flaws that hackers can use to gain access to your network, alter data on it, or steal personal information. This may result in severe monetary damages, identity theft, and harm to your company’s and the susceptible gadget manufacturer’s reputations.
Implementing IoT security measures helps to ensure the security of gadgets from unauthorized users and attackers.
7. GRC, SIEM, and help desk system integrations
Integration of GRC, SIEM, and other helpdesk systems into the security operations of businesses is a recent penetration testing trend. This helps in faster patching of systems, rules, and procedures by uniting numerous teams into a cybersecurity unit.
When it comes to support and risk mitigation, these solutions help to automate and streamline the work of several departments. When a vulnerability is discovered, alerts are forwarded to the appropriate teams, and suggestions are made for remedial steps.
8.DevSecOps
DevSecOps, aka development, security, and operations, is an application development practice that automates the integration of security and security practices throughout the whole software development lifecycle, from initial design to deployment.
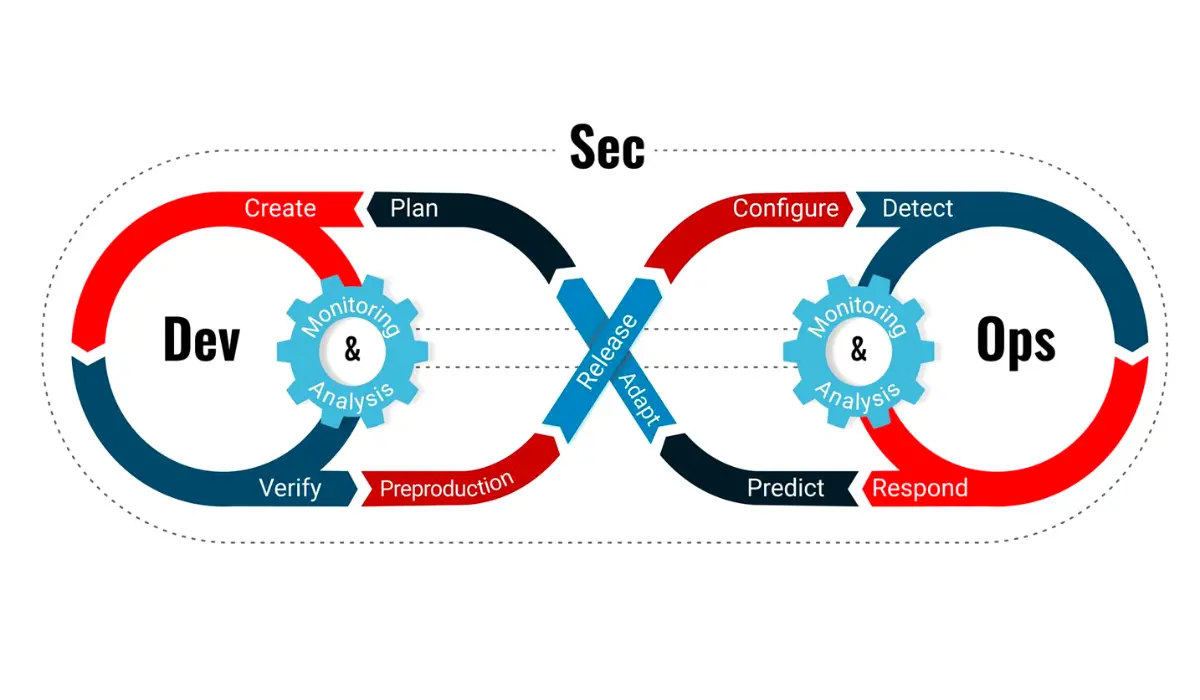
It can also be referred to as integrating security into the DevOps architecture. The emphasis is on secure code, which allows security activities to be automated. It uses agile methodologies to include security testing in the development process, which is beneficial to penetration testers.
9. Advanced Persistent Threat (APT) Simulation Testing
Advanced Persistent Threat Testing is appropriate for enterprises with developed or advanced IT environments that demand an in-depth examination to ensure the highest level of security. APT simulation testing, which is a blend of vulnerability and penetration testing as well as social engineering, helps companies enhance their security posture while establishing a comprehensive, proactive security plan.
10. Data security compliance
As technology advances, cyber-attacks evolve, necessitating more regulatory compliance. Penetration testers must stay current with data security requirements as the regulatory landscape changes.

Data security is the process of determining the appropriate governance for data protection, security, storage, and other operations. It also includes developing rules, policies, and protocols to guarantee that data is fully protected against unauthorized access and use, malware, and other cybersecurity threats.
Limitations and challenges to traditional penetration testing
Traditional penetration testing follows a pre-defined process, in which the threat hunting is often closely aligned with the known problems. This typically misses new or complex threats, which reduces the efficiency of the penetration test. Conducting it manually costs a lot of time and resources.

The modern complex and large-scale digital infrastructures are often overwhelming for a comprehensive penetration test, potentially leaving vulnerabilities undetected. A malicious actor who once found this unpatched vulnerability could potentially exploit it to cause operational disruptions to the business.
The resistance to social engineering attacks is still a greater concern in the traditional penetration testing approach. Also, the acute shortage of expert human resources is a greater challenge faced in conducting effective penetration testing. Relying too much on automation also causes trouble since it delivers false results occasionally due to the immaturity of current pre-trained models.
The lack of robust visualization and reporting tools is also a concern in primitive penetration testing, which makes it harder for the stakeholders to understand the implications of the result and make informed decisions on fixing the detected vulnerabilities.
Penetration testing has come a long way and indeed there is room for improvement. By bringing various aspects of cybersecurity together, better and stronger defenses can be built toward better resilience in the security posture.
Penetration testing trends are in constant evolution with time and changes in the threat landscape. Ranging from manual to automated approaches to penetration testing, market trends have changed technologically and methodologically. This helps greatly to deliver more effective and comprehensive assessments of the application and assets of organizations across the globe.
Integration of AI into security operations has been creating revolutionary changes recently, which have helped reduce the resources of humans, time, and money drastically. However, solely relying on automated solutions is not enough since the threats are getting more sophisticated than ever and the technological advancements are much less in comparison with the threats.
The future of penetration testing will be all about continuous innovations in technologies and talents. Organizations can stay ahead in the modern vulnerability landscape with the combination of effective penetration testing and related technologies.
Frequently Asked Questions (FAQs)
What emerging technologies are shaking up pen testing?
Technologies such as the integration of artificial intelligence, and machine learning, and approaches such as adaptive penetration testing, continuous penetration testing, cloud security pen-testing, etc. are recent penetration testing trends.
How are AI and machine learning transforming pen testing efficiency?
Artificial intelligence (AI) and machine learning (ML) have significantly improved the efficiency of penetration testing. Their capability to assess huge amounts of data in a shorter time and make faster decisions greatly helps in vulnerability assessment and mitigation. Also, the capability to learn from past tests and adapt penetration testing strategies makes it more effective in identifying emerging threats.
How can we prepare future pen testers for an innovative landscape?
Preparing future penetration testers for the current and upcoming vulnerability landscape is a multi-faceted approach. They require a combination of a thorough understanding of technologies, hands-on experience, continuous learning, and soft skills, including both oral and written communication. Participating in various professional cybersecurity communities and their events is indeed a greater approach to effective learning for them.