With people trying out what they’re interested in or not and knowing their other options, even cybercriminals have started attacking the Mac system during this pandemic. Since January, the number of cyberattacks on Macs has increased for a while now. The latest statistics say that cybercrime against Mac os has increased by over 25%. While a lot of this has to do with COVID-19 – hackers have been taking advantage of decreased security due to working from home and fears surrounding the pandemic.
Ransomware on a Mac?
While most ransomware and other types of malware aren’t specifically designed for a Mac OS, some of them still make it. The latest ransomware on Mac is called Evilquest, also known as Thief Quest.
ThiefQuest ransomware is different from previous macOS ransomware threats. Besides encrypting the victim’s files, ThiefQuest also installs a keylogger, and a reverse shell, and steals cryptocurrency wallet-related files from infected hosts. The malicious code was first found in a pirate copy of the Little Snitch app available on a Russian forum with torrent links.
The downloaded app comes with a PKG installer file, unlike its original version. By examining this PKG file, Malwarebytes (An American Internet security company) discovered that the app comes with a “post-install script”, which is typically used to clean up the installation after the process is completed.
In this case, however, the script implements malware in macOS. The script file is copied to a folder related to the Little Snitch app under the name CrashReporter, so the user won’t notice it running in the Activity Monitor since macOS has an internal app with a similar name.
The set location is/Library/LittleSnitchd/CrashReporter. Malwarebytes notes that it takes some time before the ransomware starts working after it’s installed, so the user won’t associate it with the latest app installed. Once the malicious code is activated, it modifies the system and user files with unknown encryption. Part of the encryption causes the Finder not to work properly and the system crashes constantly. Even the system’s Keychain gets corrupted, so it’s impossible to access passwords and certificates saved on the Mac.
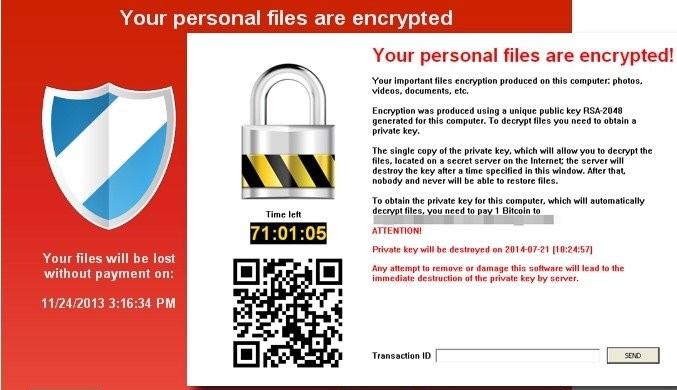
Once all files are encrypted there are 18 beeps after which the customary ransom note/message is shown. An alert with text-to-speech is raised to inform the user about the encryption and then the ransomware note gets dropped onto the desktop. In a sample ransom note, the malware operators claim to use an AES-256 algorithm to encrypt the files, and demand a modest $50 payment in bitcoin to unlock files — described as a one-time “fixed processing fee” because the decryption process “will require us to use some processing power, electricity and storage on our side.”
The threat actors tell the victims they have three days to pay or lose their files permanently. The ransomware can also receive commands from a Command and Control server and perform operations such as executing commands, executing a payload directly in memory, and keylogging. A typical Windows ransomware counterpart would “self destruct” once the deed is done.
Phil Stokes, macOS security researcher at SentinelOne mentioned that the ransomware will encrypt any files with the following file extensions: .pdf, .doc, .jpg, .txt, .pages, .pem, .cer, .crt, .php, .py, .h, .m, .hpp, .cpp, .cs, .pl, .p, .p3, .html, .webarchive, .zip, .xsl, .xslx, .docx, .ppt, .pptx, .keynote, .js, .sqlite3, .wallet, .dat After the encryption process ends, the ransomware installs a keylogger to record all the user’s keystrokes, a reverse shell so the attacker can connect to the infected host and run custom commands, and will also look to steal the following types of files, usually employed by cryptocurrency wallet applications.
● “wallet.pdf”
● “wallet.png”
● “key.png”
● “*.p12,”
Malwarebytes researchers noticed that the malware also attempts to modify some files specific that are part of Google Software Update and attempts to use them to achieve persistence on infected hosts. The malware does include some obfuscation features to help it hide.
The malware won’t run if it detects certain security tools like Norton Antivirus. It also lays low if it’s being opened in a digital environment that’s often used for security testing, like a sandbox or virtual machine. The best way to protect yourself from this and other malware is to only download software from a legitimate source. Ideally, only download from the Mac App Store. Bear in mind that downloading software from questionable Torrent sites (such as ThePirateBay) is very likely to lead to various system infections.
Interested and want to know more about device-specific malware? Follow our blog to keep yourself updated with the latest trends in cybersecurity.