The use of cloud applications has doubled in recent times. Companies offering cloud applications (SaaS, PaaS, IaaS, etc.) should consider adopting required security measures to protect themselves as well as their clients.
VAPT (Vulnerability Assessment and Penetration Testing)-enabled vulnerability assessments have gained considerable recognition for their effectiveness in preventing cyber threats and attacks.
VAPT’s role in proactively identifying potential weaknesses through vulnerability scanning in a system or application effectively applies to cloud applications as well. Securing cloud applications with VAPT helps address and prevent vulnerabilities by simulating real-world cyberattacks.
In this blog, we will help you understand how to secure cloud applications with VAPT Services and how it can help safeguard your concerned infrastructure.
Table of Contents
ToggleThe 8 Unique Challenges That Cloud Applications Face and Their Possible Impacts
From AI integration to widely utilizing hybrid and multi-cloud services, businesses in the millennial era depend heavily on cloud applications. This tendency makes cloud applications open to multiple challenges, which include the following:
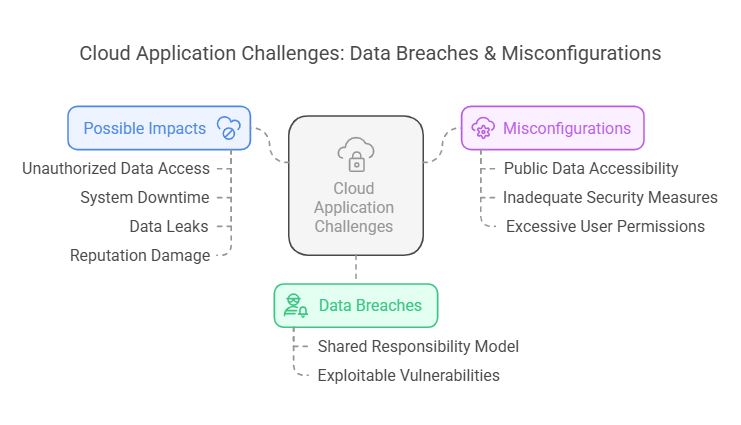
- Data breaches due to Shared responsibility model in cloud computing
Data breaches in cloud computing can occur when users or organizations fail to secure their data and configurations within the cloud environment. While these happen despite the cloud providers securing the underlying infrastructure, they can cause vulnerabilities, which attackers can exploit easily.
- Misconfigurations in Cloud Environments
Any misconfiguration within a cloud computing platform can potentially expose sensitive information to potential hackers. Not only this, but do look at the following instances :
- Leave data accessible publicly
- Not utilizing appropriate security measures (encrypting)
- Granting excessive permissions to user accounts
Misconfigurations can also include not properly setting up cloud systems, which can significantly risk data, further leading to data breaches.
Possible Impacts
- Misconfigurations leading to unauthorised data access
- Frequent system downtime
- Data leaks.
- Damage of reputation.
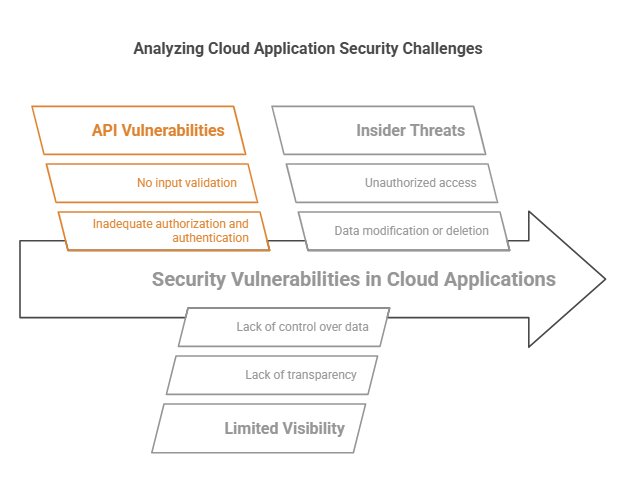
- API vulnerabilities
API vulnerabilities denote weaknesses in an API code, which hackers can easily exploit to attain unauthorised access.
- API vulnerabilities often exist as:
- Inadequate authorization and authentication
- No input validation
- Lack of adequate limits on resource consumption
Also Read: Top Cloud Security Frameworks In 2024
Impacts:
- Data manipulation and disruption due to unauthorised access to sensitive data
- Data breaches
- Abuse of resources
- Manipulation of system configurations
- Significant damage to reputation
- Limited Visibility Into Cloud Infrastructure
Suggests a lack of transparency and control over data and systems within a cloud environment, leaving organizations highly vulnerable to security threats.
Impacts: Include:
- unauthorised access
- Data breaches
- Misconfigurations
- Insider Threats
Indicates a security risk in which an authorized user of an organisation, say an employee, partner, or contractor misuses access to cloud services. While these actions (misusing accessibility) may be intentional or unintentional, harm to a company (one which offers cloud services) is certain. This can happen by way of unauthorised access, modification, or deletion of sensitive data.
Possible impacts:
- Significant interruption of business operations.
- Loss of sensitive business data.
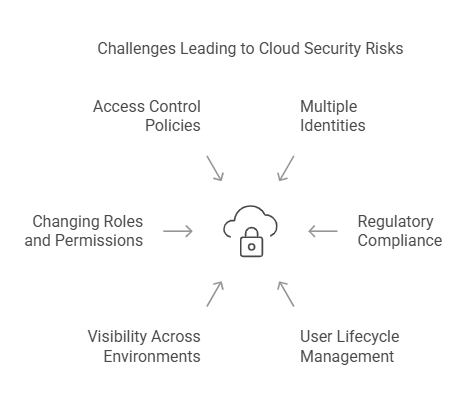
- Complex Identity and Access Management (IAM)
Cloud applications often face challenges when handling multiple identities across various cloud platforms.
Also due to offering services to clients from varied industries, they should consistently comply with diverse regulations. The other specific challenges associated with the complex IAM process of cloud applications also include:
- Handling user lifecycle management, such as provisioning and deprovisioning.
- Maintaining visibility across different cloud environments.
- Adapting to rapidly changing user roles and permissions.
- Dealing with complex access control policies.
These aforementioned issues can be further complicated by the need to mitigate security risks and prevent unauthorised access.
Potential impacts:
- Increased risk of data breaches.
- Operational inefficiencies.
- Compliance violations.
- Hindrance to business agility.
- Potential unauthorised access.
- Data leakage.
- Difficult to maintain a secure environment.
- Lack of Expertise in Cloud Security
Companies offering cloud applications as service may not be proficient enough to properly secure their cloud applications. Reasons can well include a lack of knowledge to properly secure cloud applications and infrastructure.
Potential Impacts:
- Inadequate access controls.
- Misconfigurations.
- Inadequate threat detection.
- Increased vulnerability to data breaches.
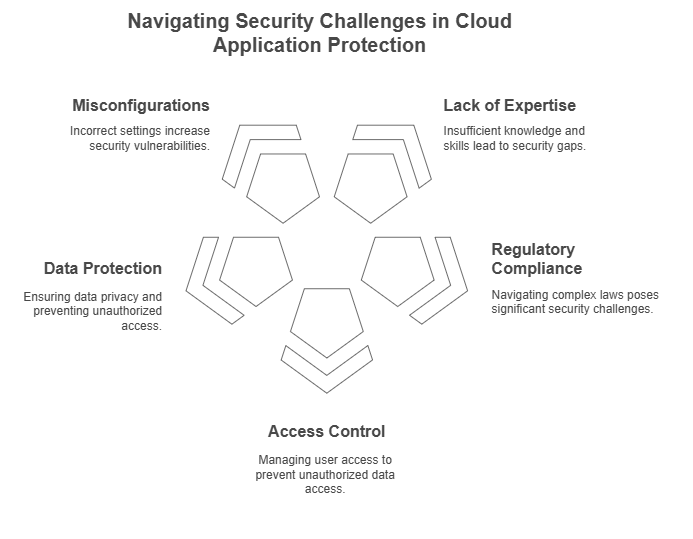
- Issues Due to Navigating Complex Regulatory Compliance
Cloud applications often face challenges when navigating through complex regulatory compliance requirements. Specific challenges usually include the following:
- Complexities with Access Control: Managing user access levels across multiple cloud applications and environments can increasingly risk unauthorised access to sensitive data.
- Data Protection and Privacy: The vulnerability of storing sensitive data on the cloud is high as it relates to unauthorised access, breaches, and leaks. This will require robust data encryption and issuing privacy controls to comply with data regulations, such as HIPAA, GDPA, etc.
- Data Residency: Data privacy laws are specific to a region. This makes it difficult for cloud application providing companies to ensure data is stored appropriately in compliant locations.
- Misconfigurations: When cloud services are not configured appropriately, this increases the risk of misconfigurations.
- Limited visibility and auditability: The complexity of cloud environments makes it even more difficult to track data movement and activities, which are crucial to undertake compliance audits.
Possible Impacts:
- Increased security risks
- Legal percussions
- Damage to reputation
- Significant financial penalties
- Loss of customer trust
VAPT – Outlining Its Specifications and Significance in Cloud Applications
VAPT is a kind of security testing that helps strengthen an organisation’s security posture by identifying and fixing security vulnerabilities. VAPT thus prevents malicious attacks.
- Significance of VAPT in Cloud App Security
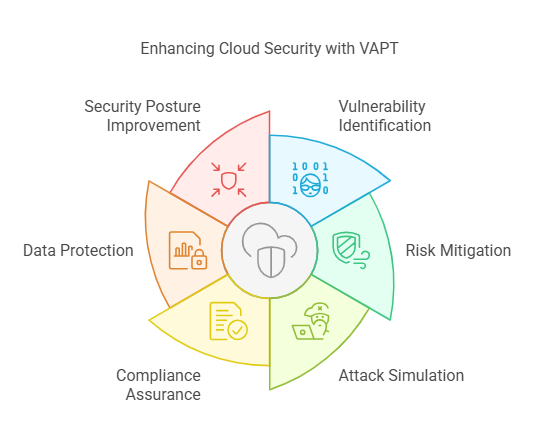
Like any other organisation, VAPT’s function is key to securing cloud applications. Its effectiveness in ensuring Cloud App Security can be summarized through the following:
- Vulnerability Identification: When it concerns risk identification, VAPT is that one solution! Doing so, proactively helps cloud applications prevent vulnerability exploitation.
- Mitigating Security Risks To Protect Sensitive Data: Following detection of underlying vulnerabilities, VAPT can effectively mitigate associated threats by enabling timely remediation of the former.
- Real-World Attack Simulation: The penetration testing component of VAPT assessment simulates real-world attacks to identify potential entry points for malicious intruders. Also assists in assessing the effectiveness of existing security controls within the application.
- Ensuring Compliance: By regularly conducting VAPT assessments, cloud-based applications can ensure compliance with data protection standards or frameworks specific to their industry.
- Data Protection: VAPT helps cloud-based service entities safeguard sensitive data by identifying and patching vulnerabilities.
- Improving Security Posture: By regularly implementing VAPT for cloud applications ensures improved and strengthened security posture. Also helps enhance resilience against potential cyberattacks.
How Can VAPT Services Help Secure Cloud Applications?
VAPT’s effectiveness lies in proactively identifying and addressing potential security weaknesses within an application, network, and infrastructure. This process not only helps secure cloud applications, but also prevents malicious intruders from attacking them.
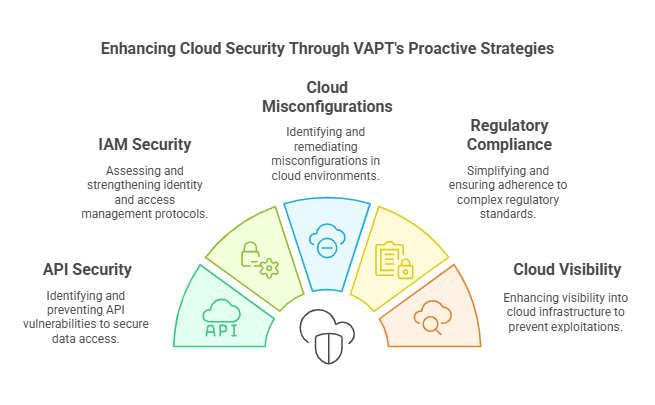
VAPT can enhance Cloud App Security by analysing the various challenges that cloud applications face. With some of them being discussed above, let’s get to understand VAPT Service’ effectiveness in addressing the same:
Also Read: Cloud Security Audit: An Ultimate Guide
- API Security: This involves identifying API (Application Programming Interface) vulnerabilities to proactively prevent malicious data manipulation and unauthorised access.
- Identity and Access Management (IAM): By testing and looking for weak password policies, improper user permissions, and poor multi-factor authentication, VAPT professionals can effectively assess IAM.
- Addressing Misconfigurations in Cloud Environment: Vulnerability identification, penetration testing, prioritizing vulnerabilities based on their risks, and remediating them are the steps that can help address misconfigurations within the cloud environment.
- Simplifying Navigating Complex Regulatory Compliance: Addressing these by VAPT services involves proactively identifying and mitigating vulnerabilities when assessing cloud app security.
- Improving Visibility Into Cloud Infrastructure: This involves undertaking penetration testing to detect vulnerabilities, such as misconfigurations, weak access controls, outdated software, and unpatched systems. In this way, visibility can be improved, also preventing exploitations by cyber thefts.
- Improving Cloud Security Expertise: This can be facilitated by identifying critical vulnerabilities, offering targeted remediation guidance, and simulating real-world attacks.
VAPT Tools For Assessing And Ensuring Cloud Security
There are specific VAPT tools that are meant to assess, ensure, and strengthen security for cloud applications. These include:
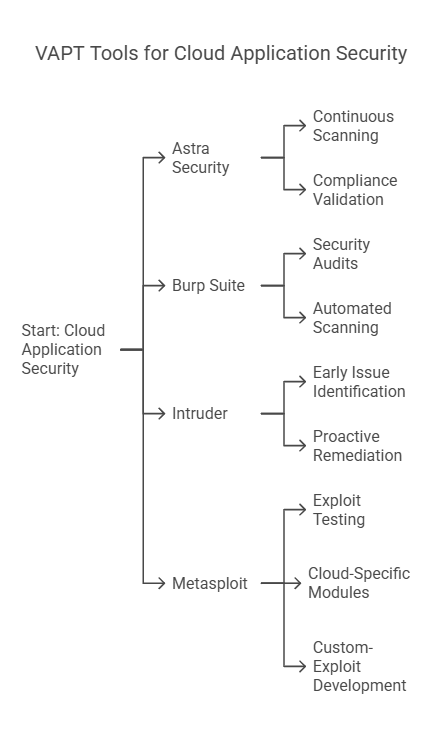
- Astra Security:
Offers comprehensive vulnerability scanning and penetration testing services. Key features include:
- Continuous scanning
- Extensive testing capabilities
- Cloud-native integration
- Compliance validation.
- Prioritization and remediation guidance.
- Burp Suite
Again a comprehensive security testing tool that can effectively scan and identify vulnerabilities in cloud-based applications. Also helps with:
- Conducting security audits for web applications and APIs on the cloud.
- Automated scanning to test cloud applications for common vulnerabilities, such as SQL injection, cross-site request forgery, and cross-site scripting (XSS),
- Intruder
A vulnerability scanner tool, Intruder for cloud applications helps identify potential weaknesses and security flaws.
Benefits include:
- Early identification of security issues
- Prioritizing vulnerabilities based on severity
- Proactive threat remediation
- Automated scanning to continuously monitor cloud app security.
- Metasploit
Helps simulate real-world attacks to identify vulnerabilities in the cloud infrastructure, application code, and configuration.
Metasploit in cloud app security is helpful for the following:
- Undertakes vulnerability scanning leverages an extensive database of exploits to identify potential entry points for attacks.
- Exploit testing to allow penetration testers to test known vulnerabilities by initiating targeted exploits. This helps check whether these exploits can gain access to an application or system.
- Cloud-specific modules that are applicable for cloud services, such as AWS S3 buckets, Azure storage, etc.
- Post-exploitation feature to further explore the compromised system once vulnerability has been successfully exploited. Also helps gather sensitive information and assess potential impact of an attack.
- Custom-exploit development for assessing unique vulnerabilities, which allows users to develop a custom exploit code to test and validate findings.
Enforcing cloud security is pivotal in protecting critical business data stored on the cloud. This is mandatory for both cloud-based applications and systems and network settings involved in cloud computing. Failure to enforce cloud app security measures can lead to major security incidents, causing irreversible damage to reputation. Given the current cloud application security trends, these do not sound as robust as expected.
This significantly calls for identifying and addressing potential vulnerabilities and threats within the cloud environment with more efficient and reliable security tools. VAPT has been identified as the most trending vulnerability assessment tool for assessing and addressing noted security issues for cloud-based applications. This also recommends adopting essential tools and techniques, Companies offering VAPT services can effectively help cloud applications-offering companies combat potential vulnerabilities to proactively avoid cyberattacks.
Tired of browsing for quality VAPT services near you? Sign in/Sign up with Wattlecorp to schedule a free CASA (Cloud Application Security Assessment) to experience an expert-cum-hassle-free cloud security assessment for your organisation.
Cloud applications FAQs
1.What does VAPT involve in the context of Cloud App Security?
VAPT services for cloud app security involves a proactive assessment of underlying vulnerabilities within a cloud application, infrastructure, systems, and network and subsequently undertaking penetration testing and proactively preventing cyberattacks.
2.What are the best practices for ensuring Cloud Application Security?
Some of the best practices to ensure cloud application security involve:
-Data encryption to prevent unauthorised access
-Using IAM (Identity and Access Management) to manage accessibility.
-Ensuring Network Security to secure network perimeter to monitor misconfigurations.
-Threat Detection to monitor threats and suspicious activity.
-Compliance management to ensure compliance requirements.
-Security training for employees.
-Incident response plan in place to aptly respond to security incidents.
-Remediation to regularly assess and fix vulnerabilities.
3.How can I secure cloud applications with VAPT?
Securing cloud applications with VAPT will require you to regularly undertake comprehensive vulnerability scans. You should also consider the following:
-Checking network configurations.
-Monitoring access controls and application code.
-Simulating real-world attacks to exploit known vulnerabilities.
-Prioritizing remediation based on risk severity.