Think about keeping your most sensitive company data on a hacker-prone server.
This is the case for many SaaS providers; however, server hardening can serve as a buffer. Server hardening for SaaS is more than just a catchphrase—it’s essential to ensure secure operations. As the backbone of SaaS infrastructure, servers must be hardened in order to reduce risks, reduce attack surfaces, and comply with security standards.
According to Gartner, until 2020, security and IT experts will continue to be aware of 99% of exploited weaknesses for a minimum of 12 months.
Server hardening, which comprises enhancing the security of your server infrastructure, is your first line of defense. Businesses that don’t have robust server hardening for SaaS run the danger of losing data, incurring costly downtime, and perhaps even being stolen.
This blog will emphasize and walk into server hardening, which is the foundation of SaaS security.
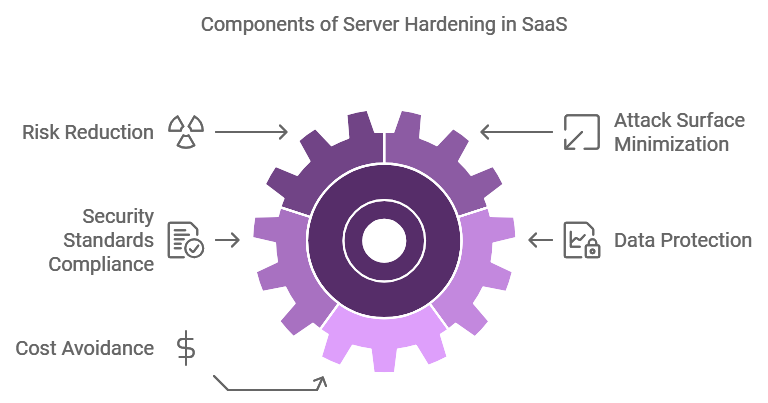
Table of Contents
Toggle- What Is Server Hardening?
- Why Server Hardening Is Important for SaaS Security
- Benefits of Server Hardening for Small Businesses
- Server Hardening Best Practices for SaaS Providers
- Advanced Server Hardening Techniques for SaaS Providers
- Challenges in Server Hardening for SaaS Providers
- How ASP’s Server Optimization and Hardening Services are Critical for SaaS Companies?
- Role of Server Hardening in SaaS Data Protection & Compliance
- Frequantly Asked Questions
What Is Server Hardening?
Configuring servers to reduce vulnerabilities, protect their functioning, and guarantee that unauthorized users cannot access them is known as server hardening. Patch management, intrusion detection, and access control are essential security features for SaaS environments. Shared servers that store data from several customers are the cause of this.
The procedure guarantees adherence to ISO 27001 guidelines for both Windows and Linux server hardening in SaaS environments. This lowers the quantity of unnecessary ports and services. Businesses protect themselves against threats like widespread malware and targeted assaults by taking this action.
Why Server Hardening Is Important for SaaS Security
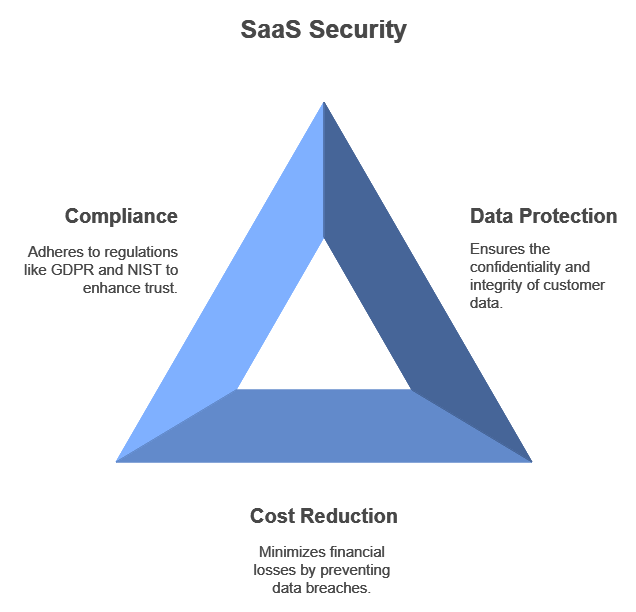
For SaaS companies, availability and customer data protection are essential. SaaS server hardening guarantees that a stable, secure infrastructure powers the services. Without it, weaknesses could be taken advantage of, resulting in financial and data loss. A poll found that in 2023, the average cost of a data breach worldwide was $4.45 million. Reduce attack surfaces, safeguard critical data, and prevent expensive breaches by putting server hardening principles into practice.
Customer confidence is further enhanced by providers being able to comply with GDPR and NIST regulations due to SaaS security technologies that maintain server security.
Benefits of Server Hardening for Small Businesses
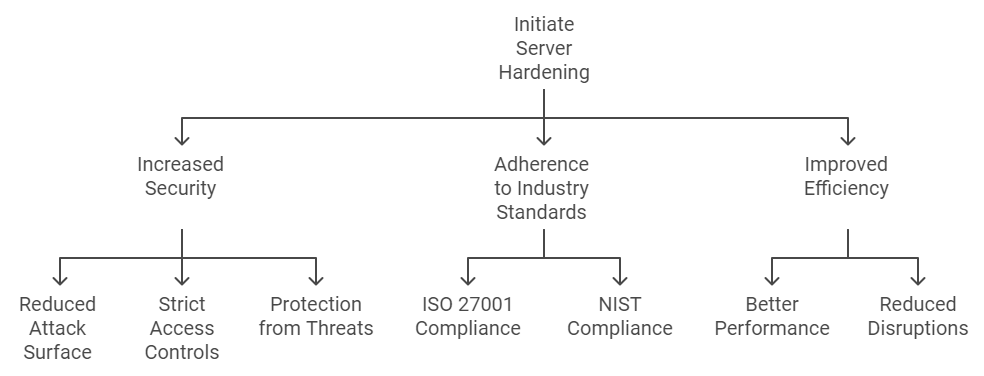
1. Increased Security and Reduced Exposure
Server hardening for SaaS companies—which involves securing servers by reducing attack surfaces, plugging holes, and implementing strict access controls—is crucial. Regular server hardening ensures that private data is protected from ransomware, hacking, and other internet threats. This is true for SaaS settings with Windows or Linux servers. As more businesses adopt SaaS, robust server security becomes more important.
2. Ensuring Adherence to Industry Standards
SaaS organizations can meet international security requirements by adhering to server hardening standards, such as ISO 27001 or NIST Windows Server Hardening. This can prevent fines and other repercussions in addition to promoting consumer trust. Keeping up a server hardening checklist ensures that AWS, Ubuntu, and other architectures’ mandatory compliance steps are followed.
3. Improved Effectiveness and Stability
Servers that have been hardened outperform those that have not, and they are safer. By reducing the attack surface, streamlining processes, and eliminating unnecessary services, server hardening improves the efficiency and reliability of SaaS platforms. These speed advantages help reduce disruption in a market where SaaS providers face intense competition. CTA – Harden Your Servers, Protect Your Data. Connect with us.
Server Hardening Best Practices for SaaS Providers
1. Windows Server Hardening in SaaS
The first step in hardening SaaS platforms running Windows servers is to establish robust firewall rules. Next, it involves disabling unused services and enabling multi-factor authentication (MFA). To mitigate hazards, patch management must be done at frequent intervals. Common tasks in a Windows server hardening checklist include limiting administrator rights, turning on encryption for any sensitive data, and doing vulnerability assessments to ensure the server conforms with industry standards like ISO 27001 server hardening or NIST.
2. Linux Server Hardening in SaaS
Linux server hardening requires the installation of firewalls, the blocking of unneeded ports, and routine software and kernel updates. Among other things, the SSH protocol is fortified by preventing root login and necessitating key-based authentication.
By using tools like AppArmor or SELinux to enforce mandatory access control, one can increase security even further. SaaS companies also need to encrypt their SaaS servers and monitor any anomalies in file integrity.
3. SaaS Server Hardening Checklist
Here are some characteristics that every SaaS platform should include on its entire server hardening checklist:
- ASP,Develop an ASP or Annual security program, from one of the best cybersecurity companies in the world.
- Create firewall and access control policies.
- Encrypt sensitive data before sending and receiving it.
- Schedule frequent operating system updates and security patch installations for the server.
- Do vulnerability scans and penetration tests regularlyon a regular basis.
- Turn on multi-factor authentication to allow users access.
- Set up intrusion detection systems to monitor potential breaches.
- Respect server hardening standards like ISO 27001 or NIST to guarantee compliance.
Advanced Server Hardening Techniques for SaaS Providers
1. Automation in Server Hardening
Enhancing server security and maintaining uniformity across SaaS systems require automation. Businesses can automate tedious security operations like configuring system security, fixing vulnerabilities, and deploying security updates using server hardening solutions. Configuration management is made simple by automated technologies like Ansible and Chef, which uphold uniform security requirements. By guaranteeing consistency in security procedures, these solutions lessen human error and the attack surface on servers.
2. Role of Vulnerability Scanning and Patch Management
It’s necessary to often do vulnerability screening on servers to find vulnerable areas in order to prevent hacking attempts. SaaS providers can search for known vulnerabilities and misconfigurations using tools like Nessus and OpenVAS.
A strong patch management system makes sure that any potential vulnerabilities are fixed as soon as they are identified. Maintaining servers with the most recent updates installed lowers the risk of security lapses and improves the overall cybersecurity of server design. Patch management is also necessary for secure servers in order to maintain compliance with NIST and ISO 27001 server security standards.
Also Read: Why Your SaaS Business Needs an Annual Security Program
Challenges in Server Hardening for SaaS Providers
Server hardening presents a number of difficulties for SaaS providers, many of which are a result of the dynamic nature of cyber threats. Prevention measures, technological know-how, and ongoing monitoring are needed to solve these problems. Let’s examine two important matters:
1. Common Vulnerabilities in Security
Although many SaaS providers make basic security mistakes, server hardening in SaaS systems refers to setting servers to minimize vulnerabilities. These include misconfigured systems, out-of-date software, and inadequately strict encryption methods. Servers are more susceptible to cyberattacks in the absence of firewalls, multi-factor authentication, and access controls. This can result in data leakage. The infrastructure becomes even more vulnerable when suggested security practices—such as routinely patching and updating servers—are not adhered to.
2. Overcoming Compliance Obstacles
Making sure that NIST and ISO 27001, two industry standards, are followed might be difficult. The standards’ multiple requirements—such as those pertaining to privacy, audits, and secure data storage—are the source of the issues. In order to oversee server vulnerability management and include technology for enhanced server security, SaaS providers must remain current with the regulatory frameworks that are constantly changing. Maintaining compliance through this delicate balancing act costs money, time, and the correct security measures.
How ASP’s Server Optimization and Hardening Services are Critical for SaaS Companies?
So, what is an ASP, or Annual Security Program?
ASP is an exclusive cybersecurity barrier that helps companies improve their business operations safely. At Wattlecorp, we provide the industry’s best ASP services to help companies combat cybersecurity vulnerabilities. ASP is an extensive continuous approach that comprises everything from vulnerability checks to coding practices to server hardening and compliance. Thus, it is an overall approach to mitigate cybersecurity vulnerabilities.
Investing in ASP can be a better option when you want to protect not just your confidential data but also your business operations, clients, and business development.
- Enhanced Security for SaaS: By lowering vulnerabilities and adhering to stringent server hardening standards like NIST, ASP’s server hardening for SaaS guarantees that your servers are safeguarded, enhancing the whole protection of your SaaS platform.
- Industry Standard Compliance: SaaS enterprises can meet regulatory requirements and gain consumer trust by using ASP’s services to achieve compliance with standards like ISO 27001 and NIST Windows Server Hardening.
- Optimized Server Performance: You can improve the response speeds of your SaaS apps by using server optimization strategies, such as Windows and Linux server hardening in SaaS.
- Vulnerability Management: ASP assists in proactively identifying vulnerabilities and managing risks before they become threats by installing server hardening technologies for automated security.
- Robust Security Solutions: ASP provides sophisticated server hardening techniques that are customized to meet the needs of SaaS organizations. This is to ensure scalable and flexible security solutions that support business growth.
Also Read: Top 5 Security Challenges Faced by SaaS Products
Role of Server Hardening in SaaS Data Protection & Compliance
For SaaS, server hardening is required to ensure data privacy and legal compliance. Companies that lack strong security measures expose themselves to the danger of financial loss, reputational harm, and data breaches. To reduce risks, SaaS organizations need to use server hardening strategies that adhere to important industry standards like ISO 27001 and NIST guidelines. Reducing attack surfaces, managing vulnerabilities, and implementing security measures are all part of server hardening. NIST recommendations offer a framework for risk identification, management, and mitigation.
For reducing any kind of data breach or compliance issues, the annual security program (ASP) offered by Wattlecorp helps in this. ASP helps SaaS companies to ensure robust security. Our penetration testing team frequently does quality checks for security, offers SaaS compliance checklists, understands the potential threats coming, and helps mitigate those issues. Moreover, according to ISO 27001 and other standards, it guarantees that the security needs of your server design are met to the highest degree. This entails implementing encryption, access control, and multi-factor authentication (MFA) to protect sensitive data and guarantee adherence to industry norms.

Server hardening for SaaS is the first step in any robust security approach. As cyber threats evolve, SaaS companies need to have strong server security measures. This is in accordance with industry standards such as ISO 27001 and NIST recommendations, and it also serves to protect sensitive customer information. By reducing its attack surface, a server that is sufficiently fortified prevents vulnerabilities from being exploited.
More crucial to server hardening success than merely completing a checklist is fostering a culture of ongoing system security configuration and improvement. Access restrictions, multi-factor authentication, encryption, and routine vulnerability assessments are all necessary for protecting your SaaS system.Wattlecorp put advanced server hardening techniques into place. Thereby, SaaS providers may increase server security, ensure data safety, and maintain client trust. Preventive threat detection, meticulous patch management, and configuration evaluations are all necessary for the ongoing process of server hardening.
Worried If you annual Connect with us now for more insights.
Frequantly Asked Questions
1. How does server hardening specifically benefit SaaS platforms?
Through the reduction of vulnerabilities, protection of sensitive data, and maintenance of operational stability, server hardening improves the security of SaaS platforms. It keeps breaches from happening, reduces possible access points for hackers, and protects client information as well as the platform. SaaS companies establish confidence and provide a secure user experience by putting best practices in hardening into effect.
2. What are the key steps in server hardening for SaaS applications?
Disabling pointless services, establishing stringent access controls, patching and updating software on a regular basis, activating firewalls, and requiring robust authentication techniques are all important measures in server hardening. SaaS server security also depends on encrypting data while it’s in transit and at rest, running frequent vulnerability scans, and keep
3. How does server hardening contribute to compliance in the SaaS industry?
Server hardening guarantees that SaaS platforms adhere to NIST and ISO 27001 security compliance standards. Strict access controls, encryption, and vulnerability monitoring are implemented by providers to comply with regulatory requirements, lower risks, and show a dedication to data protection. Following the law keeps one out of trouble with the law and fosters client trust.