Businesses in the UAE have achieved stupendous growth, thanks to the rapid evolution of digitalization! Nonetheless, there is a need to comply with data regulation frameworks, especially as far as maintaining cybersecurity is a strict necessity.
With all necessary laws and regulations also tied up with relevant data regulation standards, this makes way for adopting proactive security measures. Vulnerability Assessment and Penetration Testing (VAPT) has eventually emerged as a critical enabler to keep up with the aforementioned requirements.
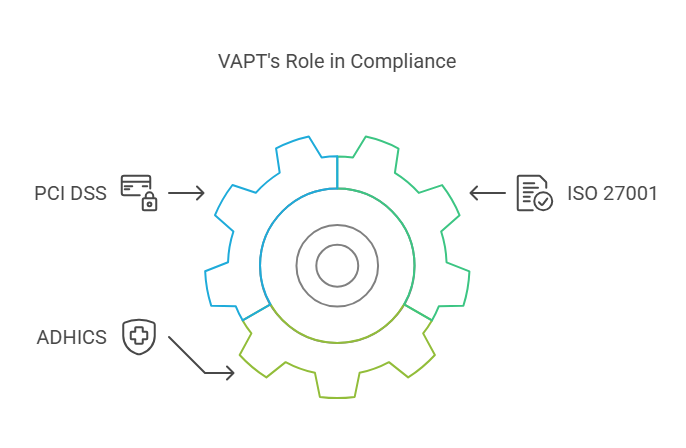
Adherence to regulatory frameworks such as PCI DSS, ISO 27001, and ADHICS is crucial to data protection. At this juncture, it would be worth appreciating the role of VAPT in ensuring cybersecurity and overall governance. Pay close attention as this blog guides you through the essential data frameworks specific to UAE governance. You will also be able to understand how VAPT compliance audits can aptly align with these and other relevant data regulations mentioned above.
Table of Contents
ToggleUnderstanding Compliance Frameworks
It is highly mandatory for businesses to comply with the ongoing rules and regulations of a country in which they operate.
That said, let’s take a look into some of the most prominent regulatory frameworks that have evolved. It would also be worthwhile to know how organisations can adhere to the same.
PCI DSS
An acronym for the Payment Card Industry Data Security Standard, PCI DSS is a ‘must-have’ for businesses handling payment card details, i.e., debit cards, credit cards, etc.
Set by the PCI SSC (Payment Card Industry Security Standards Council), PCI DSS guidelines also involve undertaking regular security assessments. These include access controls, encryption, and vulnerability scans and are strictly meant to protect cardholder information.
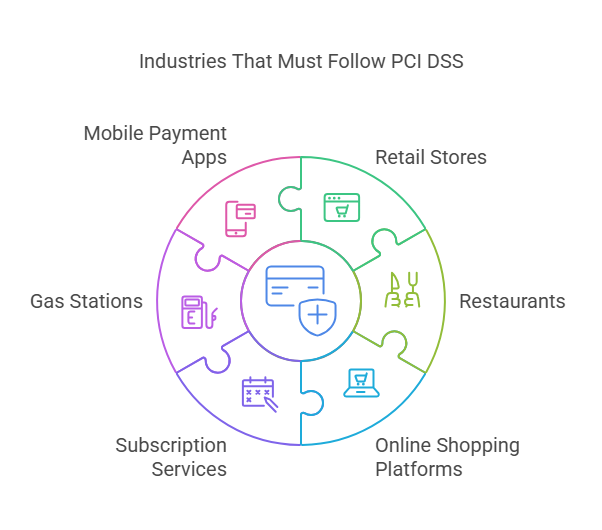
PCI DSS should be followed by companies, such as:
- Retail stores
- Restaurants
- Online shopping platforms
- Subscription services
- Gas stations
- Mobile payment apps
ISO 27001
ISO 27001 is an international standard that outlines the requirements of the Information Security Management System (ISMS). As a globally recognized standard, ISO 27001 helps organisations protect their information through the following features:
- Risk Management for defining requirements for risk assessments and treatment.
- Best practices for managing information security.
- Security Controls that consist of a set of security controls to effectively help manage information risks.
ISO 27001 comprises the following:
- Regulatory Compliance: Organisations with ISO 27001 certifications can comply with regulatory frameworks, such as GDPR.
- Risk Management: By integrating ISO 27001 into their systems and networks, organisations can identify, assess, and mitigate potential threats to their information security.
- Information Security: ISO 27001 helps ensure the confidentiality, integrity, and availability of an organisation’s critical information.

Also Read: What is VAPT?
ADHICS
ADHICS (The Abu Dhabi Healthcare Information and Cybersecurity Standards) is a sector-level standard established by the Department of Health (DoH). It primarily serves to help ensure the security and resilience of patient data and healthcare systems to protect them against cyber threats.
What Does ADHICS Do?
As a health regulatory framework to protect patient data, ADHICS involves the following:
- Strictly implementing robust cybersecurity practices for all healthcare organisations operating in Abu Dhabi.
- Ensuring confidentiality, integrity, and availability of healthcare information within the Emirate.
ADHICS ensures that every healthcare organisation in Abu Dhabi meets compliance standards by focusing on healthcare and adhering to data protection standards.
Effectiveness Of VAPT In Facilitating Compliance With ISO 27001 , ADHICS, And PCI DSS
VAPT, a security testing process to identify and fix vulnerabilities within an organisation, is also purposeful in having the latter comply with the legal and industry-specific regulatory frameworks. These include ISO 27001, PCI DSS, and ADHICS and the following approaches to ensure compliance:
1. Identifying and Mitigating Risks
- VAPT For PCI DSS: By uncovering vulnerabilities in payment systems and networks, VAPT services help fix security gaps, thus preventing unauthorized access and ensuring compliance with PCI DSS.
- VAPT For ISO 27001: VAPT Testing Services help identify vulnerabilities and verify the effectiveness of information security measures to ensure compliance with ISO 27001. They also support the risk assessment and management processes that are central to ISO 27001.
- ADHICS: VAPT procedures for healthcare organizations in Abu Dhabi enable the latter to align their operations with the security standards set by ADHICS. By pinpointing vulnerabilities in medical devices and electronic health records, VAPT helps protect sensitive patient data.
2. Validating Security Controls
By verifying the effectiveness of the implemented security measures, VAPT helps organisations align the latter with the required regulatory standards. Note that such as validation is crucial to:
- Demonstrate compliance during audits.
- Building trust with stakeholders and customers.
Also Read: The Business Impact of Compliance Failures in SaaS ?
3. Supporting Continued Adherence
Compliance frameworks do require adherence on an ongoing basis. This statement clarifies that regulatory compliance is not a one-time effort. When organisations engage in regular VAPT assessments, they are more than likely to strengthen their security posture through the following:
- Monitor evolving threats.
- Prompt redressal of new vulnerabilities.
- Maintain long-term compliance.
Understanding The Role Of VAPT In Achieving Compliance In The UAE
VAPT plays a pivotal role in achieving compliance in the UAE by helping its organisations proactively identify and address potential security vulnerabilities. This allows the latter to meet strict security regulations that are specific to the region in addition to preventing exploitation.
VAPT Services to align with UAE regulatory compliance involves the following:
1. Help Identify Security Gaps
- VAPT can effectively uncover vulnerabilities by scanning systems and applications on a regular basis.
- VAPT services can address security weaknesses (configuration errors, weak passwords, and outdated software) upon vulnerability identification.
2. Maintaining Sector-Specific Compliance
- Compliance requirements are unique to every sector.
- VAPT assessments can be efficiently tailored to specific industrial and cybersecurity requirements in the UAE.
3. Simulating Real-World Attacks
- By mimicking real-world hacker tactics, VAPT helps organisations in the UAE realize how malicious intruders can easily exploit their vulnerabilities if these are left undetected.
- Businesses can eventually prioritize their remediation efforts upon identifying security weaknesses by gauging their severity.
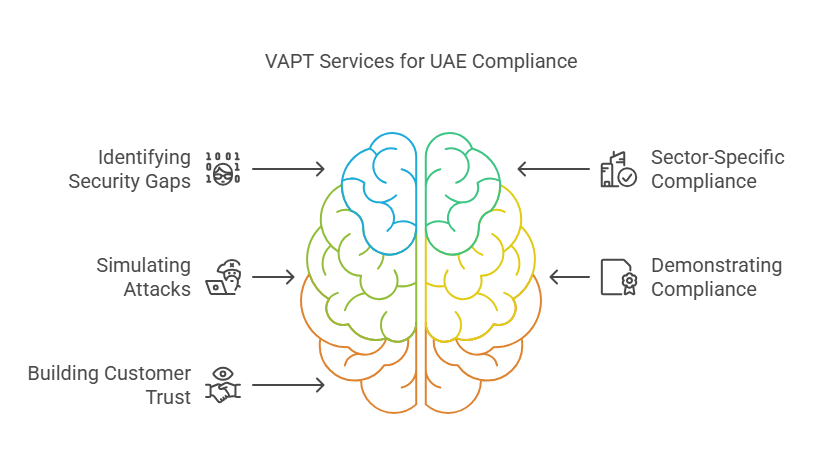
4. Demonstrating Compliance
- VAPT helps UAE businesses to strengthen regulatory compliance by conducting regular vulnerability assessments.
- Organisations can eventually demonstrate their commitment to data protection frameworks by embedding VAPT-enabled evaluations.
5. Building Customer Trust
- By incorporating VAPT, organisations can become proactive enough to protect sensitive data.
- When securing healthcare services or protecting payment card details, VAPT enables businesses to win customer confidence and trust.
Whether you utilize VAPT for PCI DSS or for any other regulatory frameworks discussed above, the thing is that you end up being proactive enough to prevent potential cyberattacks.
Ultimately, you will be able to achieve compliance with the aforementioned standards that are inherent to the legal and industrial requirements in the UAE.
Also Read: The Business Impact of Compliance Failures in SaaS ?
Outlining The Benefits Of Ensuring VAPT-Enabled Compliance Measures In The UAE
Businesses availing VAPT services to achieve regulatory compliance in the UAE can benefit through the following:
- Improved data protection by detecting security vulnerabilities to safeguard sensitive customer/client/patient information.
- Managing reputation by proactively engaging in cybersecurity measures.
- Minimizing cyber risks by patching vulnerabilities upon identification, thus preventing exploitation.
UAE businesses should strictly abide by data regulation standards, such as PCI DSS, ISO 27001, and ADHICS. The role of VAPT is vital to achieving regulatory compliance through continued adherence to the aforementioned regulatory frameworks. However, there lies potential security risks, considering the pace at which data regulations are evolving from a global perspective. With VAPT-integrated security assessments, UAE businesses can derive substantial insights and the needed guidance and assurance to stay compliant at all times.
Wattlecorp’s expertise in conducting VAPT compliance audits can help you navigate the complexities of compliance with confidence and ease. Fortifying your security posture is key to stay compliant with different UAE data regulatory frameworks. Our extensive cybersecurity team is adept at performing VAPT compliance audits tailored to your industry needs.
By leveraging cutting-edge techniques and tools, our cybersecurity professionals can identify vulnerabilities in your business to the point of having you achieve compliance. So, how compliant is your business with UAE Data Protection and regulation standards? Connect with us for a free VAPT Compliance Testing to know your compliance score.
Sign up if achieving and retaining compliance as well as staying ahead of emerging cyber threats truly matter to you!
VAPT Compliance FAQs
1. What does a VAPT Compliance Audit involve?
VAPT Compliance Audit refers to a process where you conduct a security assessment for your business. It extensively involves the need to identify potential security vulnerabilities, which if found can equally affect your compliance score. VAPT Compliance Audits are therefore meant to protect your business data and that of your customers and clients.
Through addressing and fixing security weaknesses, VAPT Compliance Audits can effectively prevent cyber threats.
At the same time, it will help you stay compliant with regulatory frameworks that are specific to the country you operate in.
2. How often should I perform VAPT Compliance Audits?
While experts recommend performing VAPT Compliance Audits annually, the frequency of undertaking the same can vary. Such a difference is based on the sensitivity of the data you handle. At other times, it can be due to system complexity or the extent at which your business is exposed to external threats.
3. What should a VAPT Compliance Checklist include?
A full-fledged VAPT Compliance Checklist should ideally comprise the following to ensure best practices to undertake a VAPT-enabled compliance audit:
• Creating a Strong Password: Should untick the ‘remember password’ checkbox when logging in from a different device.
• Encrypting Data and Files: For preventing unauthorized access.
• Installing A Viable Anti-Virus Software: To prevent phishing attacks by securing system, network, and applications.
• Secure Data Backup: This will help ascertain that the backup is encrypted and is not connected to any other device.
• Installing Third-Party Firewall: To monitor incoming and outgoing traffic and ensure proper configuration.
• Employee Training: To develop awareness on the dangers of clicking out-of-scope websites.