Malware comes in different types and each of them is destructive in its own way. One of those types and infamously known, the destructive power of ransomware is in an eerie manner. The way ransomware encrypts a target’s data and reverts it only when the ransom is paid makes it a point of no return unless the ransom is paid. Just like any other type of malware, a lot of ransomware has come and gone with only a few staying long enough with an impact to be remembered. Here are the top 5 ransomware.
Table of Contents
Toggle1. Sodinokibi
Ransomware that tried to show that ransomware isn’t all about the encryption of data and the ransom involved in it, Sodinokibi’s latest target illustrates that. Having hit other companies with ransomware attacks before, their latest target was the foreign exchange company Travelex. The company announced that the attack happened on December 31st, 2019, but the company suspects that they were compromised up to six months before the official announcement.

The company was forced to stop services and shut down its website. Customers from Australia, France, UK, and the USA were affected by the attack. The attackers demanded a ransom of $6 million but after multiple negotiations, the amount was settled at $2.3 million.
The company paid the money. With the fact that Sodinokibi shared data with the attackers beforehand, it tried to move ransomware beyond mere encryption of data to make it unusable. The ransom was paid to retain data as well as ensure that none of the data was saved on their servers ensuring that sensitive customer information didn’t leak out.
Read More: Why Invisimole – The Spying Malware
2. Maze
Another ransomware that did more than encrypting data, Cognizant was Maze’s latest target. Similar to the Sodinokibi ransomware, Maze sends a copy of the data before encrypting it.

If companies have a recent backup of the lost data, they can get running their operations without any issues. But what makes the companies pay the ransom is the threat of having customer information in the hands of a cybercriminal. Maze claims to steal around 100 GB of data from each of its victims.
3. Ryuk
Suspected to be of Russian origin, Ryuk hasn’t been found to run on a single computer that uses the Russian, Belarusian, or Ukrainian display language.

Ryuk targets companies like LA Times, Union-Tribune, and more which are unequipped to handle such attacks. Ryuk’s disabling of the Windows System Restore option makes it difficult for ransomware to escape from.
4.WannaCry
The poster boy for ransomware, its notoriety is well known throughout the world. WannaCry combines the destruction of ransomware and the spreading nature of a worm.
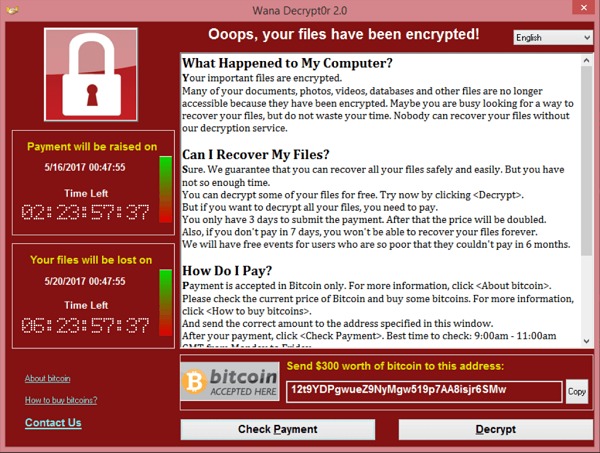
Hitting over 150 countries, WannaCry extorted a single kind of system. Outdated Windows systems that didn’t have a patch for the ExternalBlue exploit. These systems were the targets of WannaCry and the ransomware kept on making international headlines till the patch was rolled out using a kill switch.
Read More: NOTPETYA MALWARE: Cyber World’s Foe
5. Crytpowall
First discovered in 2014, Cryptowall has had multiple iterations throughout the years. The encryption used by the ransomware makes it internally secure and difficult to crack with AES 256 – bit encryption. The encryption makes it impenetrable even for brute force attacks.
Cryptowall is nasty ransomware that hides inside your startup folder. It works in the shadows by deleting small files without your knowledge. It injects malicious code into legitimate devices, compromising them. Protection is always better than cure and it stays the same for ransomware. Ensure that your system stays up to date with the patched software versions. Keep a live backup data backup, updating it now and then whenever your files undergo a major change.
Practice safe data habits, and always raise your defences, including a firewall and a strong antivirus program. Interested to learn more about the different types of malware and the top ones in each category? Follow our blog to keep yourself updated with the latest trends in cybersecurity.







