SECURE YOUR BUSINESS WITH EXPERT VAPT STRATEGIES
How Secure Is Your Infrastructure? Book a Free Consultation with Wattlecorp’s Experts to identify vulnerabilities, develop a robust VAPT strategy, and safeguard your business with tailored protection solutions.

With each passing day, technology is evolving by leaps and bounds, whether we are aware of it or not, and as more and more businesses rely on technology to power their operational processes, the risk of potential cyber threats such as cyber security attacks and data breaches also increases exponentially. This is where security measures such as VAPT testing become vital.
Let us understand VAPT testing in detail, so as to harness its powers in the most efficient way possible. Once you read this blog and familiarize yourself with VAPT testing methodology, the phases of VAPT testing, the types of VAPT testing assessments, and the best VAPT testing tools in the market, you will be able to fully appreciate the importance of VAPT for small businesses and large enterprises and will have better clarity on how to choose a VAPT testing provider.
Let’s get started! First things first!
Table of Contents
ToggleWhat is VAPT Testing?
VAPT, or Vulnerability Assessment and Penetration Testing, is a critical security evaluation method that combines both automated and manual testing techniques to get an overview of the security status of the networks and systems you’re testing for vulnerabilities.
VAPT was devised by cybersecurity experts to not only aid businesses in the daunting task of identifying potential cybersecurity threats, but to also take active measures to mitigate these harmful vulnerabilities.

Any organization that is reliant on technology and data to fuel its business operations is at risk of cyber security threats by default. Such organizations will have complex layers of access to sensitive data through applications with business logic and security functions that only authorized users can penetrate.
VAPT tests will essentially help you test and understand if access layers have any weaknesses or holes existing in them that could pose a potential security breach situation.
VAPT testing does not only check the effectiveness of your organization’s security measures but will also help you in your efforts to eliminate and mitigate such risks.
VAPT testing enables you to go in using the mindset of a potential malicious agent to get a detailed insight into your security’s strengths and weaknesses, identify all your system vulnerabilities, analyze and prioritize risk management, and create clear reports that outline concise actionable steps to strategically and tactically overcome your security vulnerabilities in the order of priority without any business disruption.
What Are the Phases of VAPT Testing?
Now that you’ve understood the basics of what is VAPT in security, let us take a moment to understand how to do VAPT testing in the right way to get the most out of the procedure. It is important to do your VAPT testing in a meticulous and well-planned way because a VAPT test requires not only the right specialized tools but also the right expertise and must only be carried out by professionals to avoid accidental data corruption or business disruption.
Keep the following phases of VAPT testing in mind in order to ensure that your VAPT testing is thorough and effective:
1 Information Gathering
This is the first and most basic phase in VAPT testing that you need to follow meticulously because it will act as the foundation for your entire testing process. You need to gather as much information as possible about the testing methodology, the different parameters you need to test, and the systems you will be subjected to the test.
2. Planning and Scope Preparation
Based on your information gathering, define and prepare the scope and objective of the testing, which will help you confirm the assets you want to test, the methods used, and the outcomes expected. Overall, having a good scope will help you make the testing process as seamless as possible.
3. Vulnerability Assessment
This is the first part of the actual testing process and involves the conduction of an automated or manual scan of your test systems to identify and assess known vulnerabilities. After the vulnerability assessment phase, you can go on to the next phase and final testing phase, which is the penetration testing phase.
4. Penetration Testing
Now that you have identified and assessed your security system’s vulnerabilities, it is time to try to exploit these vulnerabilities. Penetration testing is carried out from an attacker’s point of view so that you will know which security holes a hacker is likely to try to exploit and can rectify them accordingly.
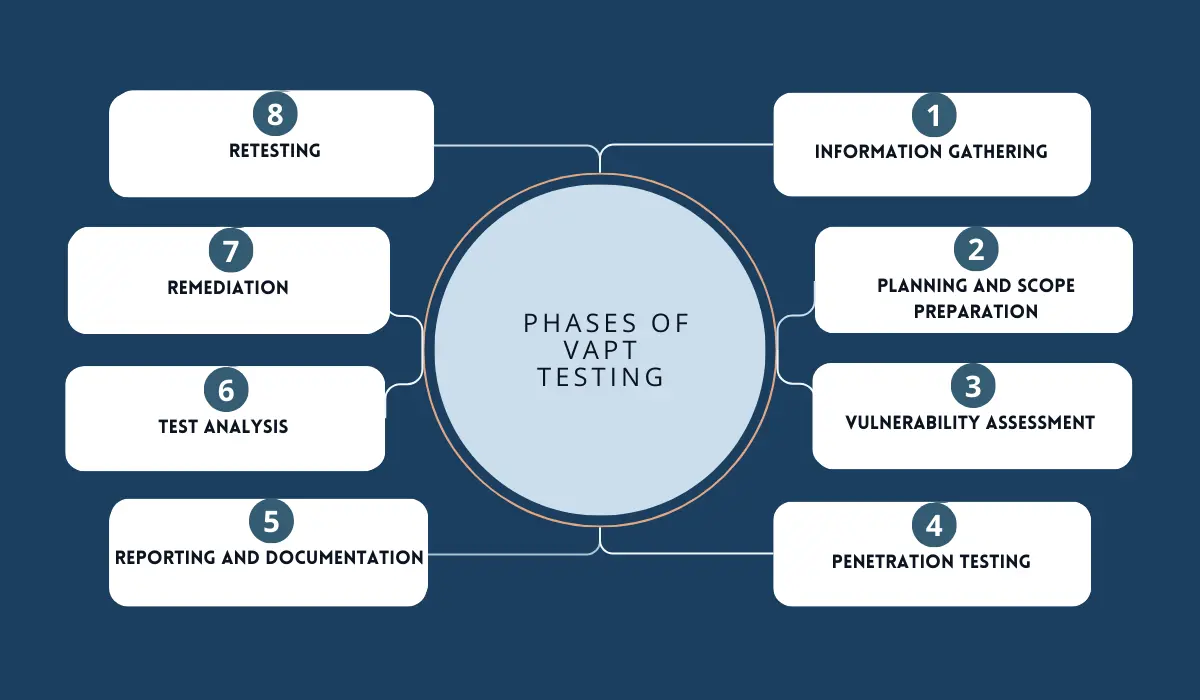
5. Reporting and Documentation
This might seem trivial, but is actually one of the most important phases of VAPT testing. With your results documented properly, there will be no historical log you can go back and refer to understand your security systems’ strengths and weaknesses. The documented test results must include all the found vulnerabilities as well as the ramifications these vulnerabilities can have. A good VAPT test report will also contain the risk factors associated with each vulnerability, risk management strategies, and actionable steps to remedy the situation.
6. Test analysis
Once you have all the documentation and reports in place, it is time to analyze the results of your VAPT test with your IT team. You must also make a note to check for false positives to ensure that you prioritize and manage your vulnerabilities in an organized and effective manner.
7. Remediation
Now comes the hard part! You need to start remedying the vulnerabilities identified through the VAPT testing one by one and ensure that you use well-coordinated strategies to confirm that the vulnerabilities have been correctly addressed. It is a good idea to involve all the concerned IT stakeholders in this process so that nothing is overlooked.
8. Retesting
You cannot stop VAPT testing after just one round, even if you have very few vulnerabilities to tackle. This is because as technology evolves, so does the capability of malicious agents to attack your data systems. Periodic retesting and follow-up scanning for vulnerabilities is important to ensure that your security systems are kept up-to-date and safe from future threats as well. So, make it a point to include automated, periodic vulnerability scans as part of your remediation strategy.
Main Types of VAPT Assessments
VAPT assessments can be of different types and it is important for you to have a basic understanding of the four different categories of VAPT assessments, which are listed below:
- API Assessment and Penetration Testing
In order to ensure that your company’s data assets and IT infrastructure are secure from malicious threats, you must ensure that a VAPT test is carried out to determine the overall efficiency of your APIs.
- Web Application Assessment and Penetration Testing
Say you are an e-commerce business. Your website may be the main glue holding your business together and acting as the face for your customers. Imagine if it got hacked! You and your business will lose all credibility in front of your end users and investors, not to mention the potential lawsuits that can follow for loss of customer data. This is why conducting a VAPT test to identify the security vulnerabilities of your websites and web applications is crucial.
Also Read: What is Vulnerability Assessment?
- Mobile Application Assessment and Penetration Testing
Mobile phones are an integral part of consumers’ lives, and hence your business must be accessible to consumers through mobile apps for you to grow, especially if you are a B2C business. VAPT tests must be conducted for mobile applications to identify the system, code, application, and database vulnerabilities that are exploitable by hackers before they discover them and extract confidential information that may spell doom for your business.
- Cloud Assessment and Penetration Testing
As more and more businesses are moving to the cloud to store their business data, conducting VAPT tests to analyze the cloud computing environments that are related to your business information for potential risks and vulnerabilities that are exploitable and fixing them is of paramount importance.
Types of VAPT Testing
You can conduct a VAPT test mainly in three different ways, listed below:
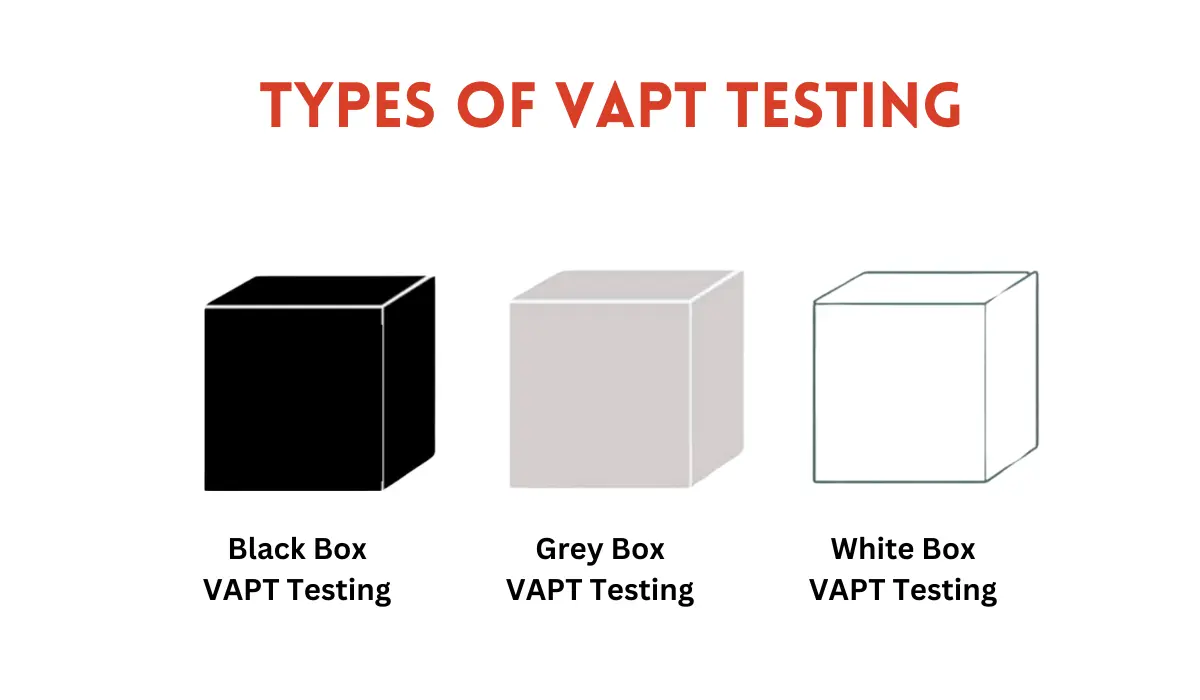
White Box VAPT Testing
In this type of VAPT testing, the testing is conducted from the internal network, which means you need to have a wrong knowledge of the system and it’s internal network to conduct white box VAPT testing. White box testing is the most recommended form of VAPT testing as it can give you the maximum coverage. It is also important to note that during white box VAPT for web applications, the source code security review is to be given utmost priority.
Black Box VAPT Testing
If you do not have adequate knowledge of the internal networks and systems, or if you simply want to do it another way, you can conduct your VAPT testing from the external network. This simplifies the process in many cases, for example, let’s say you want to conduct a black box VAPT test for your website or web application. All you need to do is give the IP address or the URL of your website to the VAPT tester and they can go ahead and assess the website and check for vulnerabilities using external networks.
Grey Box VAPT Testing
What do you get when you combine black and white? Grey! And this is exactly what grey box VAPT testing is. It is a combination of both the black box and white box testing approaches, which brings together the knowledge of your internal network and external system and enables the testing to be conducted on either internal or external networks. It does not give as much coverage as white-box testing, but grey-box testing is superior to black-box testing when it comes to identifying the most vulnerable.
VAPT Testing Tools
With the right VAPT testing tools and strategies, you can ensure that your business is well protected from the risk of potential data breaches, which could lead to costly lawsuits, loss of consumer faith, and financial losses that might make it hard for your business to ever recover from. Not to mention the reputational damage!
Let us take a quick look at the top 5 tools that are used by VAPT testing specialists:
1. Burp Suite
Burp Suite is a graphical web application testing tool that is primarily used by VAPT testers to intercept and modify HTTP/S requests while trying to identify vulnerabilities.
2. Nmap
Nmap, which is used by VAPT testers to audit networks and also for intrusion detection, is an open-source tool that is handy for testing professionals.

3. Nessus
Nessus is a vulnerability scanner that will provide you with reports of potentially exploitable vulnerabilities after scanning computer systems during the VAPT testing process.
4. Wireshark
Wireshark is yet another VAPT testing tool that is widely used by VAPT testers to analyze and monitor network connections.
5. Metasploit
Metasploit is an aptly named framework that VAPT testers use to develop and execute exploit code against remote target machines while trying to VAPT test using external networks.
Do Businesses Benefit from VAPT Testing?
We already know that data makes the world go round. If there are no proper security measures in place to safeguard organizational data, you might as well be inviting unethical hackers to target your business. If you take a moment’s pause to think about the ramifications of leaving your data unprotected, you’ll see why it is important to understand why VAPT testing is an ally you need to make!
Let us now cover some of the ways in which VAPT testing can prove really beneficial for your business, whether big or small:
1. Protection from Cyber Attacks
The first and foremost functionality of VAPT testing is to ensure that you can identify your system’s security vulnerabilities and fix them before malicious hackers exploit them to gain access to your sensitive information and business processes. So, with regular VAPT testing and remediation, you can make sure that your business is safe from most cyber attacks, which can result in far-reaching repercussions like data loss, financial damage and business disruption.
2. Business Reputation Protection
This is in fact an extension of the aforementioned point. A data security breach can have far-reaching consequences that are not limited to just financial loss. A well timed cyber attack can do so much damage to your business reputation that you may not only lose the faith of your customers but might also find it hard to help your business recover after the blow. VAPT tests help build your customer’s faith in you as they know that your systems are secure against cyber threats and they can rest assured that their data is in good hands.
3. Time and Money savings
A stitch in time does indeed save nine! VAPT testing and the associated remediation will help you patch your security vulnerabilities before they fall into the wrong hands. If you spend a judicious amount of money on getting the right VAPT service providers for your business safety, you can avoid the potential hefty fines and lawsuits that will follow if your data security is compromised by hackers.

4. Compliance Regulation
VAPT testing is required to meet the industry standard compliance that your specific industry demands. If you do VAPT tests frequently and keep your certificates up-to-date, you will be able to avoid the penalties and fines that come with improper compliance.
5. Effective Risk Management
Even if you identify the vulnerabilities in your system, it is not going to be of much help to you unless you take immediate action to remedy them. A thorough VAPT test conducted under the guidance of experts gives you excellent insights into the possible security threats that your networks and IT infrastructure might be facing and gives you time to prioritize and manage your risks in the best way possible.
Best Practices for VAPT Testing
There are some best practices you can follow to make sure that your business VAPT testing is seamless and successful and to make the most out of every VAPT test you conduct:
1. Define the scope of your VAPT test
Scope definition is important before starting any sort of testing and it applies to VAPT testing too. It is important to be clear while defining the exact scope of your VAPT test including the application’s network and systems that need to be tested as well as the methodologies that you are planning to employ. This will ensure that you do not miss any critical aspects while testing and will also make sure that all stakeholder expectations are met.
2. Efficient stakeholder collaboration
There are multiple stakeholders in a VAPT testing endeavor, starting from the business owners, the VAPT testers themselves, and the IT teams of the business organization, among others. To be able to conduct a highly evolved and efficient VAPT test that is thorough and covers all bases, it is important to involve all the stakeholders, make sure everyone is on the same page, and take everyone’s input in a timely manner.
3. Timely remediation of discovered vulnerabilities
As soon as you discover a vulnerability while testing, it is your duty to fix it without any delays. Of course, you need to prioritize the order in which you fix vulnerabilities after evaluating them and understanding their risk factor. You need to come up with a strategy to remediate the vulnerabilities as and when you come across them and follow up to make sure that the security measures to combat the discovered vulnerabilities are employed properly.
4. Continuous monitoring of the security network
You need not have a monitoring system in place only while running VAPT tests, rather, make sure you have some continuous monitoring program running with well-placed triggers that will activate and alert you as and when there’s a new vulnerability identified or a new threat to your security ecosystem emerges. It is also advisable to update and patch your software regularly as part of your continuous monitoring strategy.
5. Lastly, employ regular VAPT testing
VAPT testing is not a one-time thing that you can do just for the sake of a certification. It must be conducted on a regular basis to ensure that you stay on top of emerging trends and threats in the cybersecurity world. Ideally, your organization must be subjected to a VAPT test at least once a year, but more frequent checkups might be required based on factors such as the scale of the organization, the type of industry, and the dependency of the business on technology, among others.
A VAPT test is not a one-and-done deal – it is an ongoing event that can be carried out at any frequency based on your requirements, even every day or every month. Newer and more nuanced cyber security threats pop up every day as technology becomes more advanced and the prowess of malicious users evolves, making VAPT tests essential to the safety of your businesses’ sustainability. A VAPT test should be carried out for your business at least twice a year, and ideally once every quarter, to ensure that your critical data assets are protected from all new cyber security threats.
It is also important to ensure that your business stays compliant with security guidelines by getting an assessment certificate from a third-party solutions provider professional who is reliable and trusted in the industry.
Frequently Asked Questions
A simple vulnerability assessment is a security assessment method that helps you detect potential security vulnerabilities in your network system, whereas penetration testing is an invasive method of security assessment that simulates an attack from a malignant source and helps you find security holes by exploiting the vulnerabilities found during the pen testing simulated attack – when you combine both methods, you get a holistic approach to security assessment, that is, VAPT.
The steps involved in VAPT can be simplified as the following – planning and gathering the scope of the VAPT assessment, gathering of information required, assessment of vulnerability, exploitation of vulnerability, analysis of the exploitation carried out, documentation and report creation, followed by the steps required to remedy the security holes found.
Ideally, a thorough VAPT report must include a concise executive summary that is comprehensible for non-technical stakeholders as well, a well-detailed scope of the assessment and the proposed methodologies, a description of how the testing was conducted and the results obtained, a comprehensive technical list of all the vulnerabilities that were uncovered, a risk evaluation reports and the action items to be executed to remedy the situation.