Any security weakness that can push organizations to be exposed to risks or cyber threats is termed “vulnerability”. Vulnerability assessment involves the detection, classification, and prioritization of possible threats in computer systems, infrastructure, or business applications. Vulnerability assessments commonly use automated testing tools like network security scanners which display the results in vulnerability assessment reports.
Businesses that face continuous cyberattacks can highly benefit from the usual vulnerability assessments. Threat actors generally search for vulnerabilities they can use to breach systems, applications, and networks. New vulnerabilities get discovered every time in the existing hardware and software components, and businesses introduce new components regularly. Vulnerability assessment and vulnerability management programs hand in hand can help detect and fix potential security weaknesses to elevate the security posture. Now, what is vulnerability assessment? Let us read further to answer this question and learn more about vulnerability assessment.
Table of Contents
ToggleThe Significance of Vulnerability Assessment
The most specific security vulnerabilities emerge from either the technology concerns or the user behavior:
- Breaches could occur when insiders accidentally expose the information to an external source or intentionally leak the information.
- Stolen and lost devices contain unencrypted data, a core vector for infiltration into the organization’s network.
- Cybercriminals install malware on target systems to gain control of the computing systems or exfiltrate data.
Vulnerability management helps organizations eliminate data leaks and data breaches, however, it demands ongoing vigilance. The process is continuous and needs regular vulnerability assessments— completing one assessment should begin the other one. Vulnerability assessments help security teams to detect, analyze, classify, report, and remediate security threats in business applications, web browsers, operating systems, and endpoint devices.
Organizations find many new vulnerabilities every year, demanding continuous patching and reconfiguration to secure applications, networks, and operating systems. However, many companies don’t have an ideal patch management strategy and don’t apply the mandatory patches in time to eliminate the security breach. It is impractical to give all vulnerabilities an immediate patch.
With a vulnerability management system in place, you can manage the vulnerabilities and ensure that the security experts resolve vulnerabilities with high risks initially. Vulnerability management incorporates the processes and tools needed to understand and remediate the core vulnerabilities regularly.
What Potential Threats Can You Reduce Using Vulnerability Assessment?
Some of the cyber threats and attacks you can prevent using vulnerability assessment are as follows:
- Privilege escalation attacks:
These refer to exploiting the threat, programming error, configuration oversight, design error, or access control in the application or OS to attain unauthorized access to the resources that are restricted usually from the user.
- SQL injections:
It is defined as the attacks that occur when untrusted or invalidated data is sent to a code interpreter through a form input or the other data submission field within the web application. Successful injection attacks can cause data breaches, data leaks, data corruption, denial of access, or loss of accountability.

- XSS attacks:
XSS or Cross-site scripting is a security vulnerability usually detected in web applications. XSS helps attackers inject the client-side scripts into web pages that users view and could be leveraged to bypass access control, like the same-origin policy. XSS can pose either a small nuisance or a great cybersecurity risk according to the sensitivity of data the vulnerable website manages and the type of mitigations used.
- Insecure default configurations:
Hardware and software usually ship with insecure settings like easy-to-guess passwords making the user onboarding easy. Though it offers high usability, many people don’t change these configurations, which increases the chances of leaving them exposed.
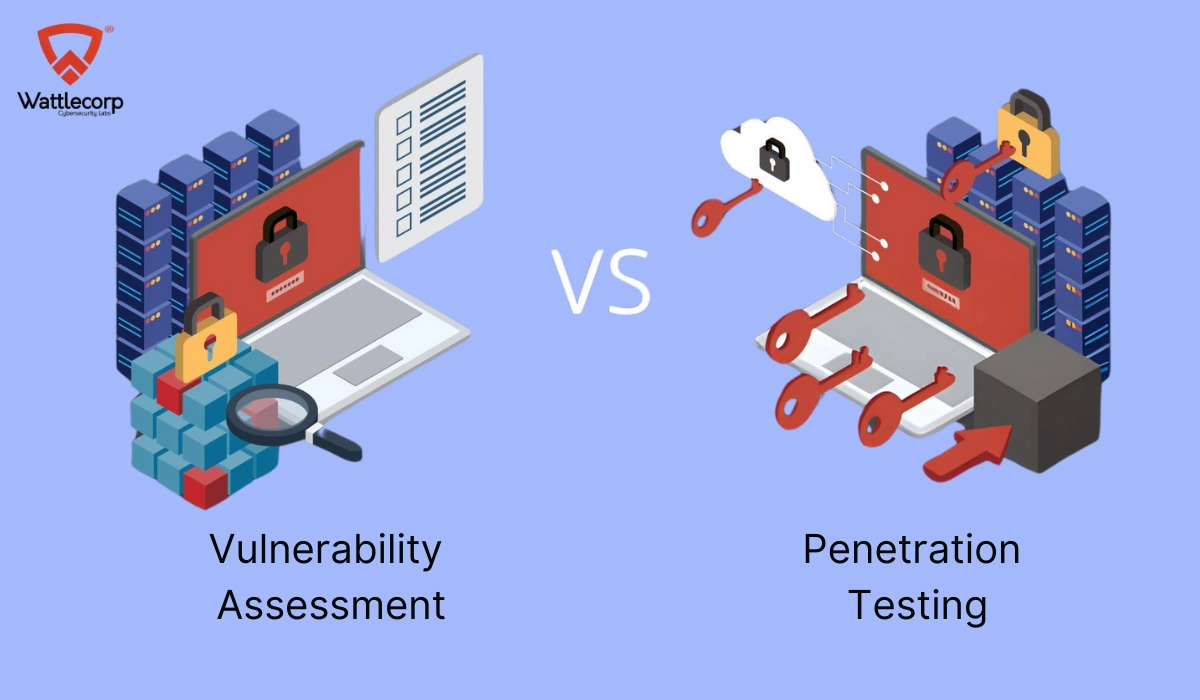
Vulnerability Assessment Vs Penetration Testing
Vulnerability assessment often incorporates penetration testing to detect vulnerabilities that might not be detected using automated scanning. This process is termed vulnerability assessment/penetration testing or VAPT.
| Vulnerability Assessment | Penetration Testing |
| Vulnerability assessment focuses on exploring vulnerabilities and recommending the ideal remediation or mitigation steps to minimize or eliminate the risks identified. | Penetration testing alone is not sufficient for a whole vulnerability assessment. |
| Though this can be implemented as part of vulnerability assessment, the major emphasis of the penetrating system is to identify whether a vulnerability is found exploitable. | On the contrary, penetration testing involves identifying vulnerabilities and attempts to exploit them to intrude on a system, cause data breaches, or expose sensitive data. |
Types of Vulnerability Assessments
An in-depth vulnerability assessment process utilizes different automated vulnerability assessment tools to implement various scans across the whole IT ecosystem. This lets the organization identify vulnerabilities that exist across endpoints, applications, systems, and databases.
The four major scans executed as a part of vulnerability assessment include:
1. Network-based scan
- It identifies the threats and vulnerabilities you can exploit in network security attacks. It includes analysis of traditional and wireless networks.
- The scan emphasizes present network security policies and controls.
2. Host-based scan
- It identifies the vulnerabilities that exist across servers, systems, containers, work, clothes, workstations, and other network hosts.
- This is implemented as an agent that could scan monitor devices, hosts, etc., to detect authorized activities, systems, issues, or changes.
- It offers high visibility to the patch history and system configuration.
3. Application scan
- It detects the vulnerabilities that concern software applications, including source code, application, architecture, and database.
- It identifies misconfigurations and related security weaknesses in network and web applications.
4. Database scan
- It explores vulnerabilities within the service or the database systems.
- It helps to eliminate data-specific attacks like SQL injections and detect vulnerabilities, like misconfigurations and escalated privileges.
Also Read: Penetration Testing Guide For Businesses
Cybersecurity Vulnerability Assessment Steps
1. Determine Attractive and Critical Systems
Initially, it is important to analyze the entire ecosystem and determine which business and networks speak well to your business operations. The attacker’s target can vary based on your perspective. Check every asset from the intruder’s perspective and rank them according to their attractiveness.
2. Execute Cybersecurity Vulnerability Assessment
Scan your entire network actively with the help of automated tools to discover security weaknesses and flaws. The attractive and critical assets better known as ‘targets’ need further analysis, which includes testing using real-time scenarios to understand and evaluate perceived cybersecurity weaknesses.
The assessments should depend on aspects such as vendor vulnerability announcements, vulnerability databases, asset management, and threat intelligence feed. A vulnerability assessment is completed when the overall system or network efficiency meets the defined security standards.
3. Conduct Vulnerability Analysis and Risk Assessment
Source identification and root cause analysis are important factors you need to consider once the vulnerabilities are detected. It provides a holistic view that supports remediation. The process includes assigning a severity score or rank to every susceptibility according to factors such as:
- What information is at risk?
- Which systems or networks have been affected?
- How severe are the potential attacks?
- Ease of compromise
- What is the potential damage when an attack occurs?
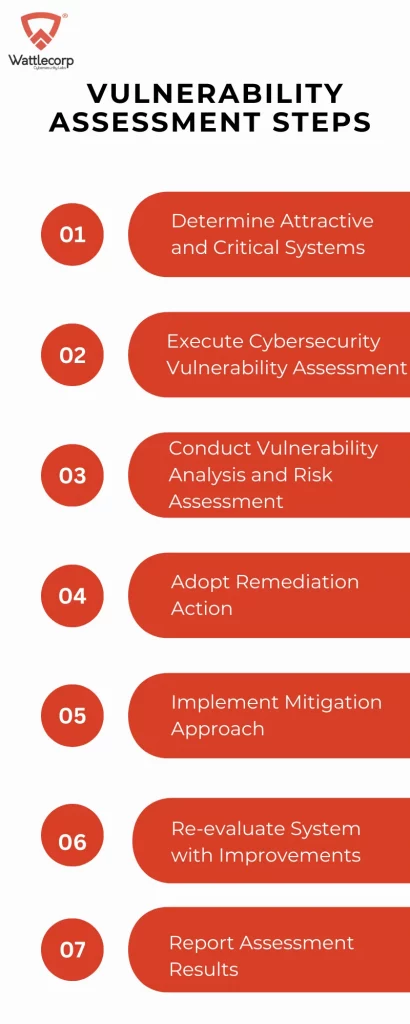
4. Adopt Remediation Action
The key objective of this stage is closing the security gaps. Determine remediation actions for every identified vulnerability. The remediation actions include:
- Updating configurational or operational changes;
- Development and implementation of vulnerability patches;
- Implementation of advanced security measures, vulnerability assessment tools, or procedures.
5. Implement Mitigation Approach
Every vulnerability can’t be completely resolved, in this context, mitigation comes to action. Mitigation emphasizes reducing the chances of a vulnerability getting exploited or limiting the impact of its exploitation.
Through a practical approach called ‘virtual patching’, you can promptly apply a patch to the vulnerability identified without changing the source code or the components.
The virtual patch builds a secure barrier that blocks malicious actors from taking advantage of the vulnerability. This effectively buys time up to the implementation of a permanent patch or code fix.
6. Re-evaluate System with Improvements
In this phase of vulnerability assessment methodology, the system’s security posture gets assessed using methods similar to the initial assessment. This includes vulnerability testing, code reviews, penetration testing, and other specific techniques. The focus is however moved towards recognizing whether the previously detected vulnerabilities have been eliminated or minimized successfully to an acceptable extent. The assessment also targets identifying any new vulnerabilities that have arisen due to the configurations or changes applied.
7. Report Assessment Results
The next phase is reporting the assessment results. The key objective of the vulnerability assessment report is to define the system’s effectiveness clearly and propose potential solutions if the present security measures prove ineffective. A detailed vulnerability assessment report includes additional factors such as:
- Which systems get impacted?
- What is the level of simplicity in compromising or attacking the system?
- What are the potential business consequences that result from a successful breach?
- Can the vulnerability be accessed via the Internet or does it demand physical proximity?
- How old is the identified vulnerability?
- Are there any regulatory obligations your organization sticks to?
- What is the expense associated with the data breach in your particular industry?
Comprehensive and real-time visibility throughout the IT ecosystem is important for every organization focusing on cybersecurity. Organizations that make persistent efforts to scan the environment for vulnerabilities can defend their business against potential risks and threats. However, all vulnerability assessment tools are never created equal. Combining vulnerability assessment with Secure Source Code Review Services India ensures a more robust security approach, identifying both application-level weaknesses and infrastructure vulnerabilities.
While choosing vulnerability assessment services, choosing the tool that offers timely identification of threats without a delay in endpoint or system performance is pivotal. Hence, organizations should consider adopting vulnerability management with the right cybersecurity services provider, which can act immediately and close all potentially dangerous gaps in the security system.
Frequently Asked Questions
Firstly, identify the systems and networks that are part of the vulnerability assessment. Now scan the network or system with automated vulnerability scanning tools. Identify the security vulnerabilities and eliminate the false positives with threat intelligence. Review the causes of the vulnerabilities, the impacts, and the solutions for remediation. Implement assessment whenever you make significant changes to the system or the network.
Vulnerability assessment is defined as the systematic review of the security loopholes within an information system. it identifies whether the system is susceptible to any potential security defects in the given time frame. The process can involve manual and automated techniques, with a focus on comprehensive coverage of the security posture.
Vulnerability assessment helps businesses identify the vulnerabilities in the software and its infrastructure before the compromise arises. This is a roadmap to a high state of security preparedness underlying the specific risks you confront due to the technological challenges that underpin your organization.