There are many different types of malware and it is difficult to keep track of them all. It gets even more difficult when the malware stays under the radar. One of the longest active spyware, before it was discovered, is the Invisimole malware.
What is Invisimole?
As the name suggests, Invisimole is an invisible mole that is used for spying. While it is named spyware it combines the functionalities and features of a trojan, a backdoor to do its actual work, spying. Invisimole is filled with a lot of well-equipped backdoors.
These backdoors allow attackers to peek into the compromised system. From webcam and microphone access, Invisimole also allows the attacker to edit files inside the system and spawn command shells among other functionalities.
Where Was it Found?
The first known discovery of Invisimole was in 2018. It was found in compromised Russian and Ukrainian systems. Even though it was 
Aimed to target both the Russian and Ukrainian governments, the campaign was highly concentrated. The places of discovery hint at it being used strictly for cyber espionage.
Read More: NOTPETYA MALWARE: CYBER WORLD’S FOE
How Does it Work?
The Invisimole spyware consists of a wrapper DLL file. The resources also have feature-rich backdoor modules embedded in them. The backdoor modules come in play once a system has been infected.
The backdoor modules work analogously to a Remote Access Trojan. They enable the attacker to gain a huge level of control over the 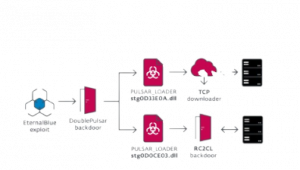
The developers of the code have also taken extra measures to avoid grabbing the attention of the victim. This ensures the malware’s presence in the system for a long time. The malware is written in both 32-bit and 64-bit versions, making it functional on both architectures.
The lengthy dwell time for Invisimole made it difficult to understand the attack vector. It was thought to be done using a couple of different methods including spear-phishing or physical access to the infected systems. The concentration of the malware to just a few dozen systems make cybersecurity experts believe that there is no code to self-propagate.
Such access to the attacker can be frightening. Combining that with the sneaky approach makes Invisimole a dangerous malware. No one knows the amount of data that the attackers got from 2013 till 2018 when it was discovered.
Read More: The Manifestation of Malware
The Return of Invisimole
Invisimole made a return in June 2020. This time it was found in high-profile organizations in the military sector and diplomatic missions of Eastern Europe. The dwell time for this discovery was short and it was believed to be present since 2019. This also allowed cybersecurity experts to find the attack vector.
This discovery also allowed security researchers to understand how it spreads inside the system once it enters the system. It spreads across the network by exploiting the BlueKeep vulnerability in the RDP protocol and the EternalBlue vulnerability in the SMB protocol (Yes, the same one used by WannaCry).
The toolset was found to be updated this time around.
The Updated Version of Invisimole 2.0
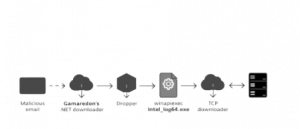
The code has had updates from the original version which was running in 2013. It used DNS tunneling for a stealthier command and control communication (C2 communication).
The Concerns of Undetectable Spyware
Imagining an unknown entity being able to access your webcam and microphone without being caught for 5 years can be frightening. The impacts of such malware being used to spy and incite cyberwars between countries will bring a lot of changes to the world as we know it.
Interested to learn more about the big shots of other types of malware? Follow our blog to keep yourself updated with the latest trends in cybersecurity.
Contributors : Navaneeth S








